We investigate a macOS keylogger targeting Exodus cryptocurrency asset manager. Learn what to look out for and how to avoid similar spyware attacks.

In early November, F-Secure reported a targeted campaign aimed at installing a keylogger on devices belonging to users of Exodus cryptowallet. According to their initial report, an email campaign pretending to offer an update for Exodus in fact tried to install spyware. The preliminary analysis indicated the scammers had repurposed a binary belonging to a commercial spyware app, RealTimeSpy. Although there’s no suggestion the developers of RealTimeSpy were involved, there is no doubt that those behind the email campaign hoped to install a version of RealTimeSpy on victims’ computers. It’s reasonable to assume the aim was to steal the contents of bitcoin wallets, but this macOS spyware can also steal other personal data through screenshots and keylogging. The program is also able to capture social networking activities and website visits.
In this post, we look into this incident in more detail and examine the implications of this kind of spyware.
Spyware with Low Chance of Success, but High Rewards
RealTimeSpy is a commercial product which, according to the developer’s website, is aimed at employers and parents who want to monitor their computers. We’ll leave aside the ethics of covert surveillance in such situations, noting only that the developers do make repeated efforts to warn that their software shouldn’t be installed on any device not owned by the installer. Verbose alerts are displayed when installing the spyware:
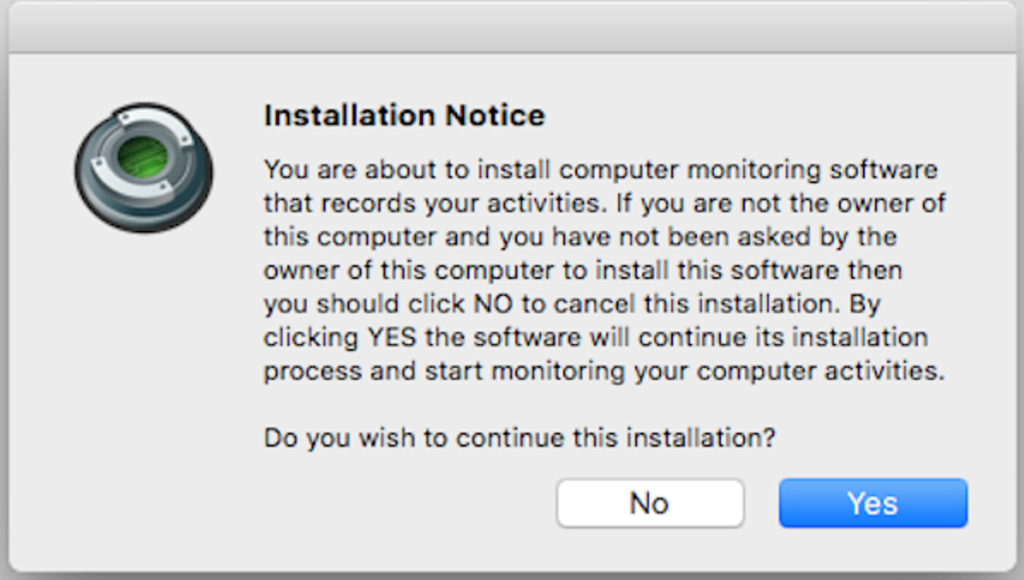
Given this, and that there’s at least two authorization requests that follow, we would expect a low infection rate. The attackers did not make any attempts to remove or hide these alerts, such as through binary editing or splash screens with transparent buttons. That may have been due to a lack of technical skill, but we shouldn’t ignore the likelihood the authors were aware of this even as they planned their campaign. Any success would reap high rewards given the spyware’s capabilities. It’s worth noting that “Yes” is enabled by default, meaning that anyone put off by the lengthy text could reflexively hit the enter/return key before realising what they were doing. After installation, stealth is one of the key features the developers of RealTimeSpy promote.
Variants
This was not the first case of this trojan spyware. In fact, we found three different versions distributed in six fake apps since 2016:
1. Build A
First seen on VirusTotal in March 2017 in launchPad.app, this version of the spyware appears to have been created around November 2016. The same binary appears on VirusTotal as Macbook.app in September 2017, and again as Taxviewer.app in May 2018.
2. Build B
A slightly different version, picupdater.app, is created on July 31, 2018 and is first seen on VirusTotal the very next day.
3. Build C
Exodus-MacOS-1.64.1-update, the one seen in the email campaign, contains an updated version of the executable that was built on 31 October, 2018 and again first seen on VirusTotal the following day.
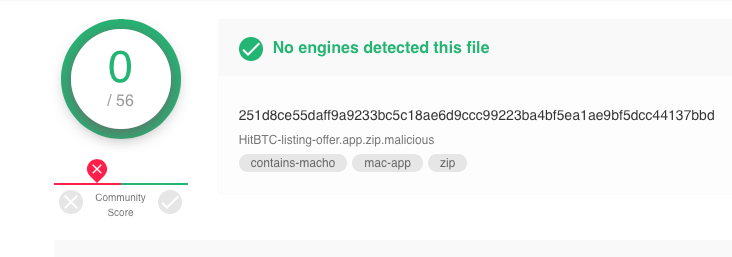
All the above are detected by 21 of the engines on VirusTotal, but we also discovered another version of this build, called HitBTC-listing-offer.app. This remains undetected on VirusTotal at the time of writing. Based on the name, it would also appear to be targeting bitcoin users:
The core binary in all cases is a Mach-O 64-bit executable with the name rtcfg. All versions of the spyware have the same bundle identifier, system.rtcfg. Likewise, each contains a second executable in the Resources folder called relaunch.
Dropped Files
Upon successful installation, the malware uses AppleScript to add itself to the user’s Login Items. This appears to be its only means of persistence across boot ups, although the relaunch binary – as might be expected from the name – helps persist the rtcfg executable during the same session if it is killed for some reason.
Exodus-MacOS-1.64.1-update and friends also add themselves to System Preferences’ Accessibility Privacy pane, though for versions of macOS 10.12 or later this is disabled by default. This has a serious effect on the spyware’s capabilities, as we’ll see a little further on.
When all is functioning as intended, the rtcfg exec creates two invisible folders in the User’s home directory. ~/.rts records active app usage in a binary plist file called syslog:

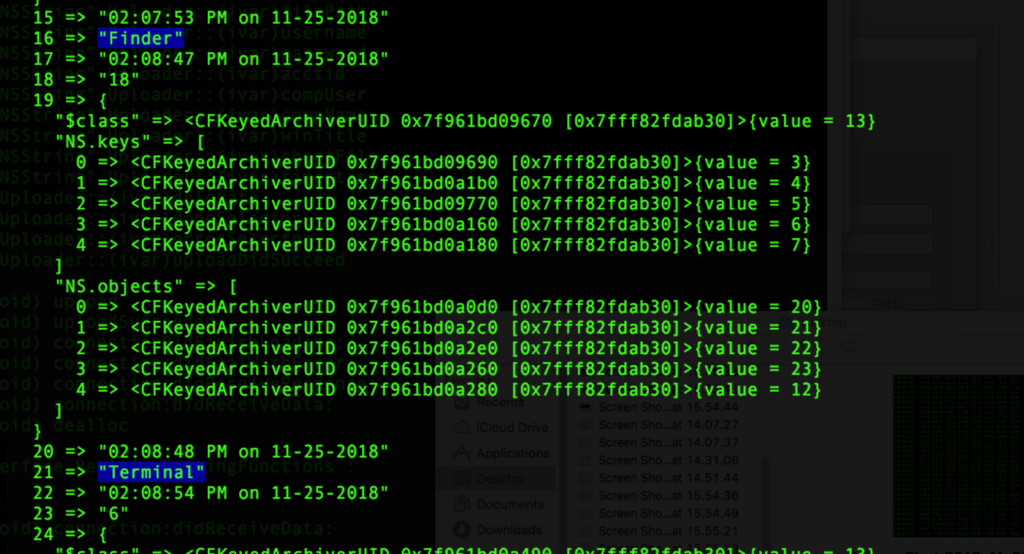
The keylogger saves data in ~/.keys folder, also as a binary plist in consecutively numbered log files, skey1.log, skey2.log and so on.
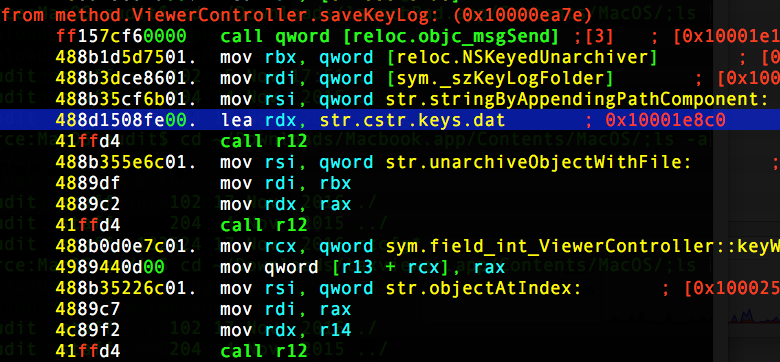
Two other files, both binary property lists containing serialized data, may also be dropped directly in the Home folder, ~/kspf.dat, and ~/ksa.dat.
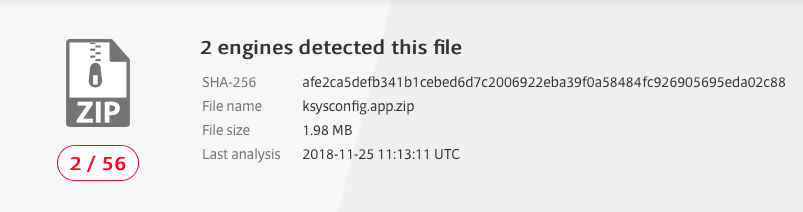
Another Keylogger
Based on this analysis, we discovered another associated but different spyware item, detected by only two of 56 engines on VirusTotal:
ksysconfig.app appears to be a dedicated keylogger, and uses both a different bundle identifier, system.ksysconfig and different executable, ksysconfig, albeit clearly following a similar naming convention. Code analysis shows that ksysconfig is not just a renamed version of rtcfg binary, although there are clear similarities in both the classes and methods they use and the files they drop. ksysconfig also writes to ~/.keys directory, and to another invisible directory at ~/.ss. This contains another binary plist, sslist.data containing serialized object data.
The ksysconfig binary appears to be part of an application called “Keystroke Spy”. Given the code similarities, it looks as if it originates from the same developers as RealTimeSpy. Since this app wasn’t involved in the email scam campaign, we did not analyse it further.
AppleScript Strikes Out
One of the lines of code that stood out during our analysis in all these binaries was this one:

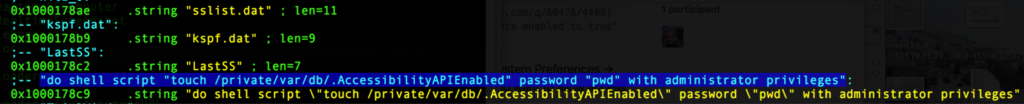
This code used to allow Accessibility control for any app in macOS prior to 10.9. It is essential for spyware as it allows the process access to UI elements. However, in 2013, Apple changed the way Accessibility works and this code is now ineffective. Our research indicates that the first version of rtcfg to appear on VirusTotal probably began life around November 2015, by which time this code was already redundant. The fake Exodus update app lists its minimum version as 10.6, so that indicates that either rtcfg included code from an older version, and/or the spyware is intended to target as wide a range of users as possible.
However, code that would have made it possible to enable Accessibility on macOS 10.9 to 10.11 is missing, although it would be a simple matter for it to be added in a future build. Despite that, there’s no way to do this programmatically on 10.12 or 10.13 (Mojave is another matter), so it looks as if the malware authors are out of luck unless their targets are way behind the times.
Command & Control?
Another interesting feature of this malware is that it does not have it’s own C2 structure, so how is it supposed to exfiltrate the user’s data? If we look at the offerings of the commercial spyware company, RealTimeSpy, it appears they expect their customers to view any data saved through an account on the company’s servers. One researcher who looked into the fake Exodus updater reported that the application repeatedly tried to log into an account at realtime-spy.com. We’re not sure if that was intentional or just a product of copying the binary from elsewhere, but our tests also confirmed there was no successful communication to any domains other than realtime-spy.com.
Staying Safe
There’s no doubt that the intent of those behind the email campaign was to deceive and compromise the unwary. If successful, we’d be inclined to class this as a medium to severe threat due to the range of functions that a completed compromise would offer to the attacker. However, there are several barriers to success which reduce the severity of the risk.
First, by repurposing commercial software that includes multiple warnings to the user, even the most casual of users should spot that something is wrong even if they fall for the phishing email. As always, heed warnings and avoid the temptation to “click-through” modal alerts.
Second, the malware won’t work as intended on 10.12 or later unless the user takes further steps to enable it in the Privacy tab of System Preferences’ Security & Privacy pane. On Mojave that’s an even taller bar, as there’s at least three separate user settings that, ideally, would need to be manually activated. As we’ve warned elsewhere, consider carefully what you allow in this pane because it applies to all users on the system.
Those on 10.11 or earlier would be most at risk. The best remedy there is to upgrade. El Capitan is now three years out of date and suffers from a number of unpatched vulnerabilities. The risks of remaining on such an old version of macOS really should compel anyone still using it to upgrade.
Takeaways
In sum, this campaign to infect unsuspecting users with macOS spyware has small chance of success for the majority of users. Even so, a single compromise would hand an attacker everything they need to steal bitcoins and other valuable personal data from the unfortunate victim.
Indicators of Compromise
Filepaths
~/ksa.dat
~/kspf.dat
~/.ss/sslist.dat
~/.keys/keys.dat
~/.keys/skey[1].log
~/.rts/sys[001].log
/Applications/ksysconfig.app
~/Library/Application Support/rsysconfig.app
Hashes
Exodus-MacOS-1.64.1-update.app
ae2390d8f49084ab514a5d2d8c5fd2b15a8b8dbfc65920d8362fe84fbe7ed8dd
HitBTC-listing-offer.app
251d8ce55daff9a9233bc5c18ae6d9ccc99223ba4bf5ea1ae9bf5dcc44137bbd
picupdater.app
123c0447d0a755723025344d6263856eaf3f4be790f5cda8754cdbb36ac52b98
taxviewer.app
987fd09af8096bce5bb8e662bdf2dd6a9dec32c6e6d238edfeba662dd8a998fc
launchPad.app
b1da51b6776857166562fa4abdf9ded23d2bdd2cf09cb34761529dfce327f2ec
Macbook.app
2ec250a5ec1949e5bb7979f0f425586a2ddc81c8da93e56158126cae8db81fd1
ksysconfig.app
afe2ca5defb341b1cebed6d7c2006922eba39f0a58484fc926905695eda02c88


