A Guest Post by Shridhar Mittal, CEO of Zimperium
For the past few decades, corporations have spent considerable time and resources investing in security solutions for traditional endpoints and the infrastructure to which these devices connect. The focus has been on the devices their employees and customers use to connect to their services or workflows.
Modern workflows have evolved and grown, and as a result, new devices have been introduced into the enterprise environment. Many organizations big and small accepted these tablets and phones into their systems in the spirit of productivity, but have dedicated little thought as to how these devices might impact their attack surface.

The Rise of Mobile in the Enterprise
Over the last two years, the modern workforce has changed the face of enterprise security needs, pushing the envelope of technology, access, and capabilities for workers connecting into corporate systems all around the world. Far outside the scope of the physical corporate perimeters and the security within, these new workflows have done more than increase distributed efficiency; they have increased the modern enterprise attack surface to a scale many enterprises were not prepared to handle.
In the context of these last two years and the rapid transformation to work that they represented, mobile devices became utterly critical assets. From replacing the encrypted token keys of the past with two-factor authentication (2FA) apps, to enabling Microsoft Office 365 and other workforce productivity applications for mobile access, the phones and tablets adorning the desks of employees around the world were now part of the core enterprise technology ecosystem in a way they just had not been previously.
These devices are not all corporate-owned either. According to the Verizon Mobile Security Index 2021, 70% of organizations adopted BYOD policies to support the distributed worker. It must be stated explicitly: this means that enterprise data is being accessed, downloaded, and transferred to all of these devices, many of which are personally owned.
And this is not a flash in the pan. The reliance on the mobile endpoint is here to stay. According to the Verizon Mobile Security Index 2021, 71% of enterprises consider mobile to be very critical to business, a trend that rapidly accelerated due to the global pandemic. But with this heavy reliance comes a major shift in the total attack surface for each of these enterprises, and yet far too many still lack even the basic security afforded to more traditional endpoints.
Unprotected Mobiles Increase Your Attack Surface
With this sharp uptick in mobile reliance and usage, attackers have turned their focus to unsecured mobile devices, ripe with corporate system connections, personal and private data, and a low risk of being caught. Many recent headlines demonstrate these attacks are not just small data leaks. Instead, enterprises are faced with zero-day and zero-click vulnerabilities designed to target mobile devices to steal or spy on unsuspecting users. With the average user unaware of the risks to their devices, many of these attacks are more successful than even malicious actors anticipated.
According to Google’s Project Zero, so far in 2021 Android and iOS have accounted for 31% of all zero-day, in the wild vulnerabilities used in real attacks against real users (18 out of 58). This is a sharp uptick over 2020 where mobile-only accounted for 11% (3 out of 26).
Maddie Stone and Clement Lecigne of Google’s Threat Analysis Group attribute this sharp rise in attacks and the changing attack surface to the earlier mentioned reliance and aforementioned growth of mobile throughout the world.
When you start thinking about enterprise data and security, the bottom line is mobile endpoints pose a great risk. From BYOD policies to Office 365, compliance mandates like HIPAA, PCI, or NERC, enterprises need to mandate security on all endpoints, including mobile just like traditional endpoints. There is no difference if an employee has data sitting on a laptop or a tablet; it’s one and the same.
From the rise of man-in-the-middle attacks targeting endpoints to misconfigured apps leaking critical information, it’s not just malware that is threatening mobile security. These relied-upon mobile endpoints and the data they are connected to through enterprise apps and services are left at risk due to vulnerable operating systems, malicious and poorly secured apps, and phishing. Rogue and compromised networks, an increasing number of apps with cross-functionality, and even mobile-malware complexity mirroring traditional threats continue to introduce risks to mobile endpoints and apps.
MDM Is No Substitute For Mobile Threat Defense
Over the last few years, many enterprises have turned to mobile device management (MDM) solutions to provide minimal aircover over their iOS and Android devices. When the threat was minimal, these solutions made sense as they could detect changes in the OS or delete corporate data in the event of a lost or stolen device.
But MDMs are not fit to fulfill the security needs of the modern enterprise, lacking the security controls, protections, and capabilities necessary to stand up against advanced threats. MDM solutions are the start of a cohesive mobile security strategy, but MDM cannot be relied upon as the only layer protecting enterprises from the growing mobile threat.
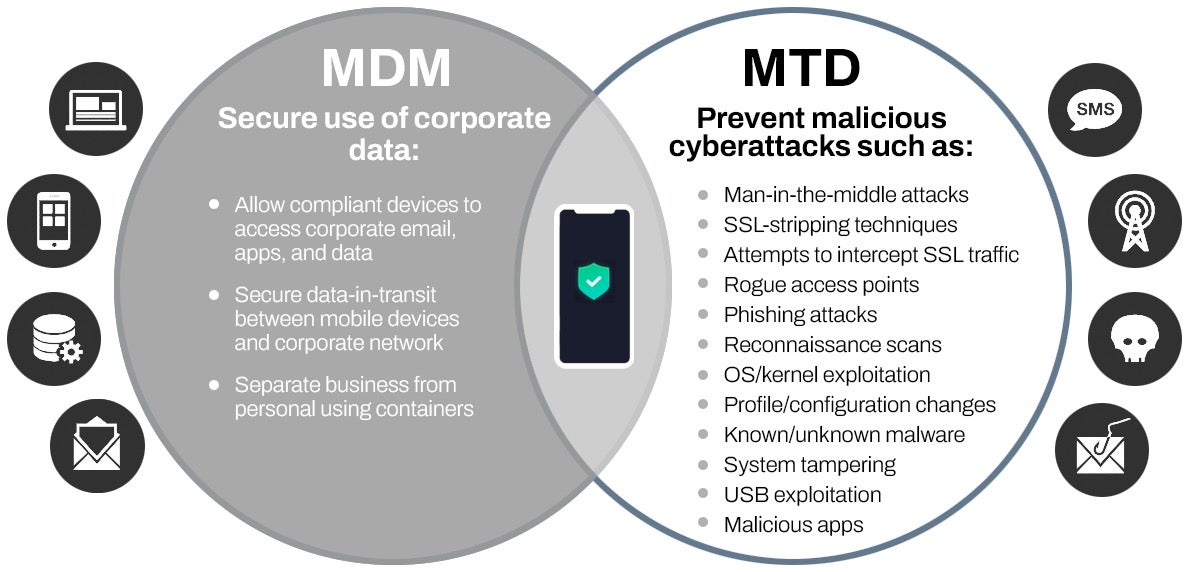
Protect Your Mobile Endpoints with MTD
The modern threat requires a modern security solution to stay ahead of the hacks and malware, minimizing the attack surface. Mobile threat defense (MTD) is enterprise security designed to stay ahead of the attackers, providing the visibility and confidence that IT and security teams need as more mobile endpoints connect into the corporate network.
The mobile endpoint’s security posture connected to corporate networks, both managed and unmanaged, needs to be addressed to avoid any of these devices becoming the starting point for a much larger security incident.
Properly configured and integrated, advanced MTD solutions can enhance existing zero-trust controls by providing mobile device risk attestation. This integration and extended security capabilities are vital to shoring up defenses for enterprises evolving from EPP to XDR security solutions. Advanced MTD solutions provide the features, workflow, and capability that complement XDR capabilities on mobile devices.
IT and security leaders responsible for their enterprise’s mobile endpoint security should be aware that purpose-built mobile security applications are designed to do more than prevent attacks and bring a whole host of other advanced security features to the mobile devices. While legacy mobile security tools do exist, they lack the advanced approach to mobile endpoint security necessary to keep up with modern-day threats.
“MTD products not only prevent attacks but also detect and remediate them. MTD focuses on identifying and thwarting malicious threats, rather than relying on device management configuration to protect against simple user mistakes.
[We] see no value in adopting antivirus solutions that do not provide behavioral anomaly prevention and detection, as the underlying mobile platforms already perform signature-based scans to look for malware.” – Gartner Market Guide for Mobile Threat Defense, March 2021
Integrating Mobile Threat Defense and XDR
With MTD and XDR coming together, organizations are taking a step into the future of complete endpoint security, addressing all the devices from the phone in the pocket to the desktop in the office with advanced security solutions. The alliance between Zimperium and SentinelOne addresses the complete endpoint attack surface, delivering critical security controls to security teams and protection to employees near and far.
By powering the brand new SentinelOne SingularityTM Mobile application added to the lineup, SentinelOne is now providing complete endpoint coverage and protection with the most advanced endpoint security solutions on the market, covering Android, ChromeOS, iOS, macOS, Linux, Windows and Windows Server operating systems, as well as IoT devices and Cloud workloads.
Conclusion
SentinelOne SingularityTM Mobile customers can now manage mobile device security alongside their user workstations, cloud workloads, and IoT devices. SingularityTM Mobile brings behavioral AI-driven protection, detection, and response directly to iOS, Android, and ChromeOS devices. Part of the Singularity Platform, SentinelOne delivers mobile threat defense that is local, adaptive, and real-time, to thwart mobile malware and phishing attacks at the device, with or without a cloud connection.
About Zimperium
Zimperium, the global leader in mobile security, offers the only real-time, on-device, machine learning-based protection against Android, iOS, and Chromebook threats. Powered by z9, Zimperium provides protection against the device, network, phishing, and malicious app attacks.


