Cybercriminals often look at different methods to gain an organization’s sensitive data. One common way is to abuse the AdminSDHolder object in Active Directory. This post discusses how attackers can add accounts with sufficient access to the AdminSDHolder object and end up gaining complete control of the Active Directory environment.

What is an AdminSDHolder?
Active Directory Domain Services (AD DS) use the AdminSDHolder object and the Security Descriptor propagator (SDProp) process to secure privileged users and groups. The AdminSDHolder object has a unique Access Control List (ACL), which controls the permissions of security principals that are members of built-in privileged Active Directory groups. The SDProp is a process that runs every 60 minutes on the Primary Domain Controller emulator to ensure the AdminSDHolder Access Control List (ACL) is consistent on all privileged users and groups.
How Do Attackers Exploit AdminSDHolder for Persistent Administrative Access to Active Directory?
The AdminSDHolder attack allows attackers to apply changes to the AdminSDHolder object. Attackers can add accounts to the list with the same privileged access as other protected accounts and move laterally. The figure below shows an attacker adding a new account to the ACL in the AdminSDHolder object and granting permissions – either full control or modified rights.
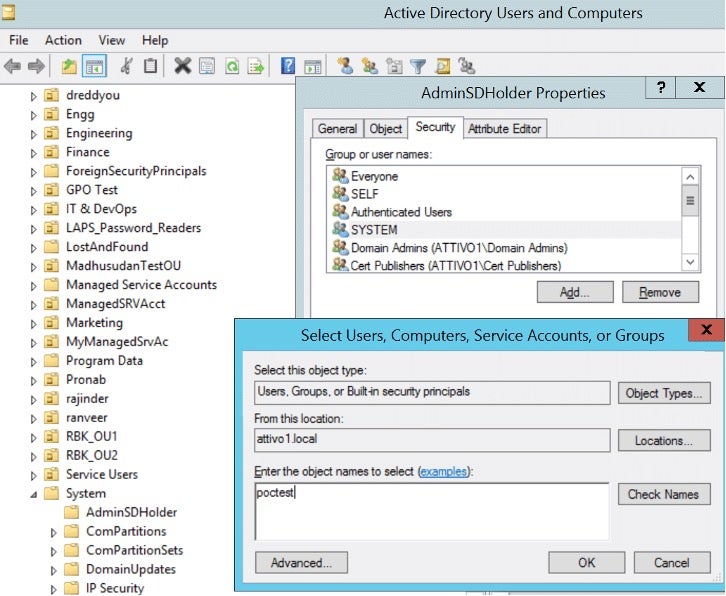
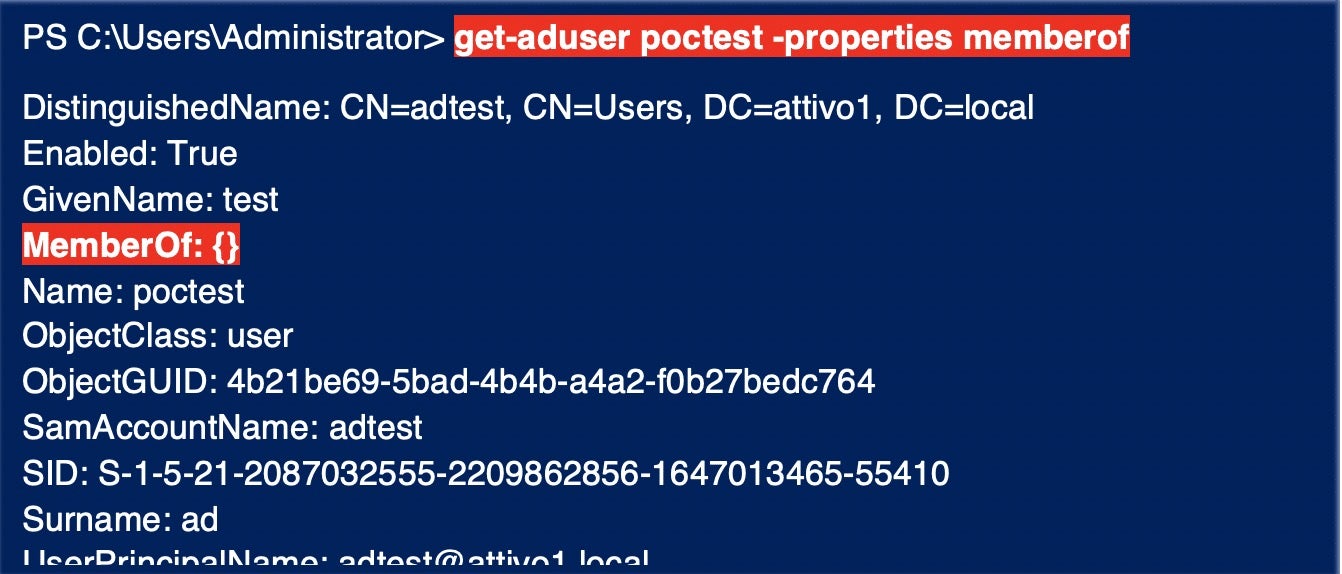
After running SDProp, the user account “poctest” is automatically added to the Security Descriptor of the Domain Admins group, giving “poctest” full control or modify permission on the group. This new user account added can change the Domain Admins group membership. Note that the user account “poctest” has no group membership. Despite not being a member of any groups, attackers can use this new account to modify the group membership of Domain Admins. You can run the PowerShell command below to check the group membership.
> get-aduser poctest -properties memberof
Detect and Report AdminSDHolder ACL Exposure
Active Directory misconfigurations significantly increase the risk of advanced attacks. The Ranger® AD Assessor (Ranger AD) solution continuously monitors AD exposures and detects unprivileged ACLs in AdminSDHolder that could lead to malicious activity.
Security admins must identify who currently possesses permissions/access as per the organization’s existing access policies, monitor the default configured ACLs, and review access permissions for objects that are members of privileged groups on the AdminSDHolder object.
The following security steps can adequately mitigate the risks of unprivileged AD exposures:
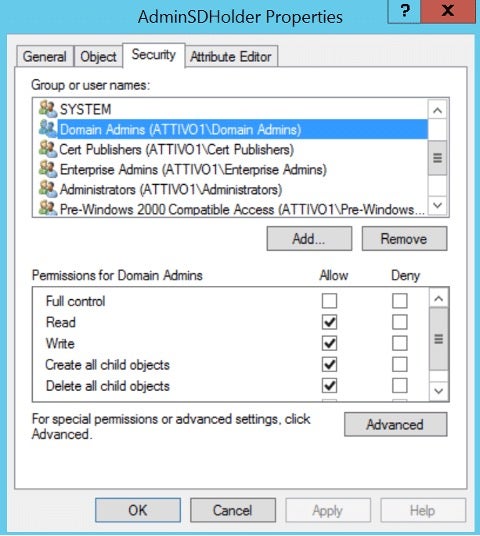
- Security admins can verify and remove unprivileged users from the AdminSDHolder ACL. As shown in the figure below, the Security tab displays the ACL applied to all members of protected groups.
- Monitor users and groups with
adminCount = 1to identify accounts with ACLs set by SDProp. The PowerShell AD cmdlets output below shows users with security ACLs set by SDProp.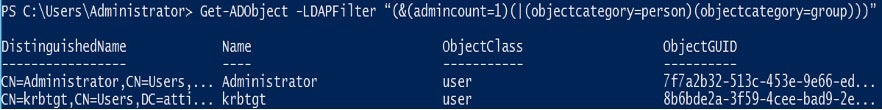
Conclusion
AdminSDHolder object offers attackers opportunities to exploit user accounts and groups to take relative control of the Active Directory environment. Organizations must identify all unprivileged users that pose potential risks. The Ranger® AD solution provides real-time detection of AD privilege escalations. Assessing and monitoring the rights of specific privileged domain objects will reduce the attacker’s ability to modify the most privileged groups in Active Directory.
For more information, please visit Singularity RANGER | AD Assessor.


