It’s Day 2 of RSAC and we really ripped up a storm! Top of the list of stellar presentations was our integration with Intel. While we talked about how our Cryptominer detection integrates with Intel’s Accelerated Memory Scanning to Threat Detection Technology, Intel were here at Booth S 1527 to talk to our customers and visitors.
Endpoint Security on the Move
Earlier in the day we announced our new S1 Mobile Admin App. For too long, admins of cybersecurity products have been bound to their chairs and offices. Now, managing S1 can be done on our iOS and Android admin apps! Chris Goodman gave a cracking presentation showing how this powerful new tech can add value to your SOC team and ensure your networks are protected no matter where you are. Great job, Chris!
Lookout – Here Comes S1 Integration
That wasn’t all we had to say about mobile, either. Dave Richardson spoke about our collaboration with Lookout – a collaboration in a best-of-breed cyber readiness program. The integration will allow managing all Lookout mobile agents on your network, all from the convenience of your SentinelOne console.

Detected: Intel Inside S1’s Booth!
Later in the day, Alex Nayshtut from Intel and Aviram Shmueli from SentinelOne took turns at both booths going into the finer points of the S1/Intel integration. We are the first next generation vendor to leverage hardware to improve detection. Another great win for SentinelOne’s best-in-class Endpoint Security platform. Thank you, Intel (and thank you Alex and Avi!).


Ranging Far and Wide
Caleb Fenton also talked in more detail about S1 Ranger today, an upcoming feature we announced yesterday that will provide even greater visibility into your network to discover running services, unmanaged endpoints, IoT devices, and mobiles. Caleb explained how S1 Ranger achieves all this without adding any extra agents or doing heavy-duty network scanning. Ranger leverages S1’s existing agents as sensors and will be completely integrated within the S1 management console.
The day continued in fine style with Jamie Williams explaining how SentinelOne integrates with the MITRE ATT&CK framework and riffed on the importance of behavioral indicators to help enterprise understand the full context of an intrusion.
ActiveEDR: Changing the Game
Migo Kedem took a turn on the booth to explain ActiveEDR and the crucial difference that this brings to the endpoint security marketplace. Why have humans slogging through the logs and alerts provided by passive EDR tools, when an automated, machine learning-driven solution can do the work for you on the endpoint, and without the delays of cloud-based detection systems?
It’s Raining Threats, Hallelujah!
We were on a thunderous roll all day, but we hope you didn’t miss our demo of SentinelOne Hunter. This demo illustrates how Advanced ActiveEDR can be used to enhance threat hunting using the Hunter Chrome browser extension. Imagine your SOC team receives a threat advisory containing one or more IOCs (Indicators of Compromise). A threat actor has compromised systems and is using Powershell with a C2 mechanism. Has your organization been exposed to the threat? Let’s find out from the convenience of our Chrome browser using S1 Hunter!
Here’s a few screenshots of Hunter in action. For the full demo, come by our booth.
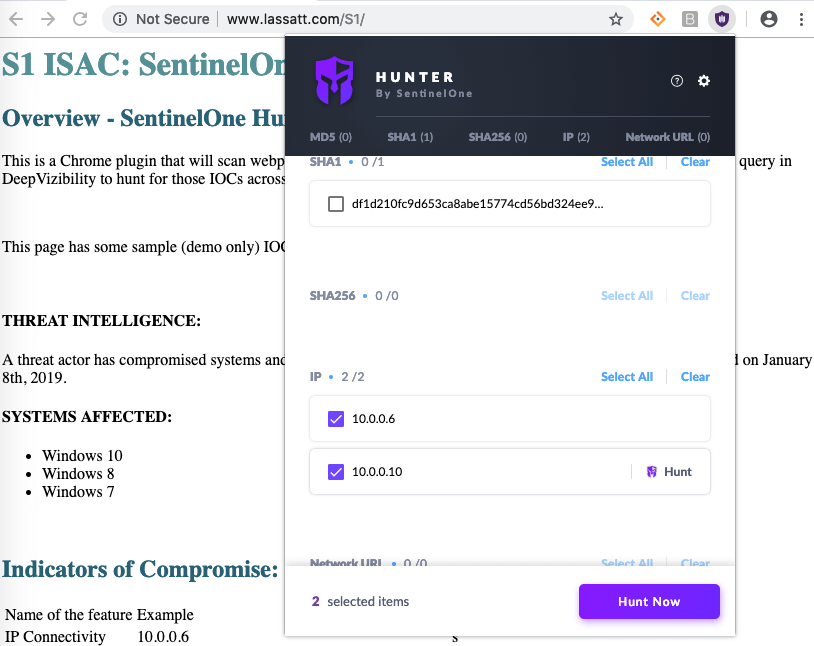
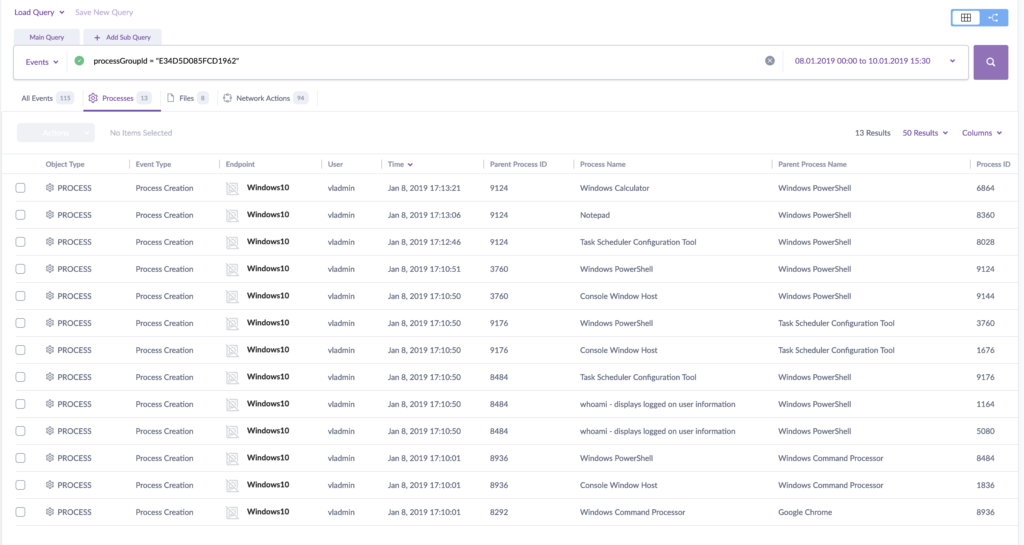
“Hunt Now” presents us with a clean view of the attack history, as shown here:
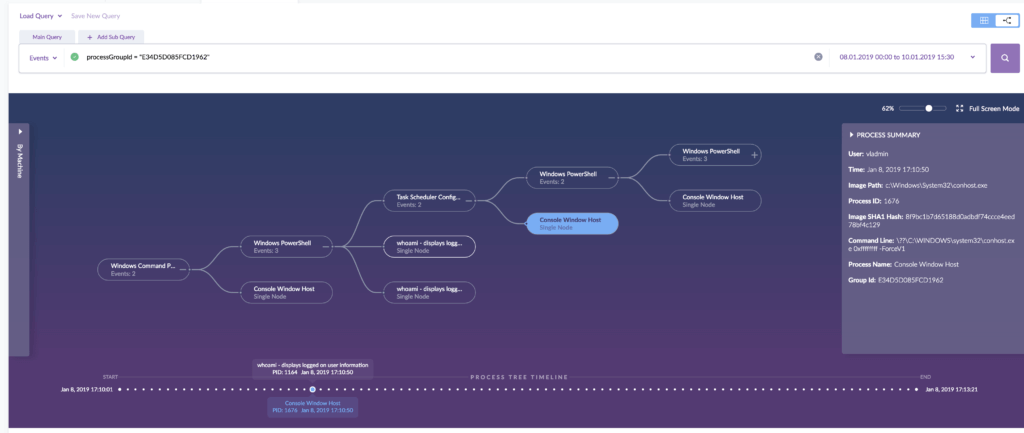
Here’s how the attack story line looks in the interactive process tree view:
Day 2 has been a truly awesome day. It may have been pouring with rain outside, but the sun was really shining inside the hall on Day 2 with great presentations of innovative tech in abundance, nowhere more so than at SentinelOne’s Booth S 1527.


