Whether you wanted to relax, safe in the knowledge that you are protected by SentinelOne’s leading autonomous endpoint protection solution, or just felt like taking a mid-week breather, rest assured that for RSAC Day 3 we had you covered as we continued with a blend of presentations showcasing innovative security tech and a little mid-week R&R!

Cutting Through The Cloud
On RSAC Day 3, Yishay Yovel joined us at Booth S 1527 to explain how Cato Networks implemented the SentinelOne Nexus SDK, bringing zero-day threat protection to their cloud-based network offering. With our SDK, they are able to scan all traffic in Cato Cloud, including services like email and web gateways, file sync and share services, traditional file servers, medical devices, and much more. Their implementation accelerates deployment of next-gen prevention capabilities across Cato Cloud, offering unrivalled protection with the SentinelOne Nexus SDK.
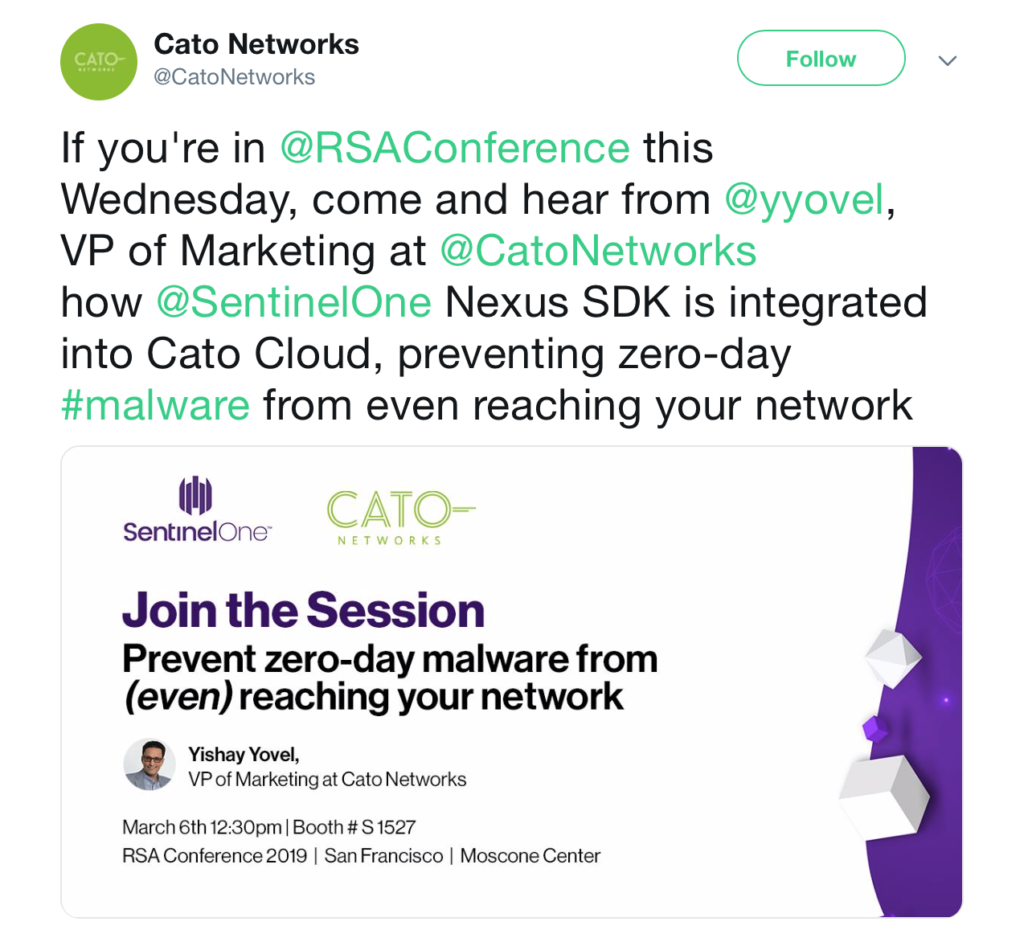
Sticking with the cloud-based theme, we hosted Automox’s Chief Product Officer Bryan Gale, who explained how Automox can help enterprises reduce their attack surface through cloud-based, automated patching of the OS and 3rd party software.
The Future is Here
Earlier this week we announced the S1 Mobile Admin app, which also integrated Recorded Future in a dedicated tab. Today, Thien Huynh shared his demo on how Recorded Future and SentinelOne combine to allow not only the best detection possible but also greater, in-depth threat intel from the rich data provided by the SentinelOne agent.

CryptoCocktails Anyone?
Sounds like a recipe for relaxation, and a little fun! Together with Intel, we hosted customers, prospects and friends at a nearby restaurant for our CryptoCocktail Reception, providing some light relief during a day of in-depth cyber security talks, demos and presentations.

S1 and Syncurity SOAR Higher Together!
Day 3 was rounded out by JP Bourget’s talk on SentinelOne and Syncurity’s IR-Flow SOAR ( Security Orchestration, Automation and Response) platform integration. Using SentinelOne’s native APIs, IR-Flow is able to automate the quarantine and remediation of threats on compromised endpoints.
In parallel, we also ran a demo on Advanced ActiveEDR. Consider the following: You receive a call from the FBI saying your enterprise data is available to all on Pastebin! How did this happen? If you are a SentinelOne client, you could just go to the Visibility tab and get the full attack story with all relevant context.
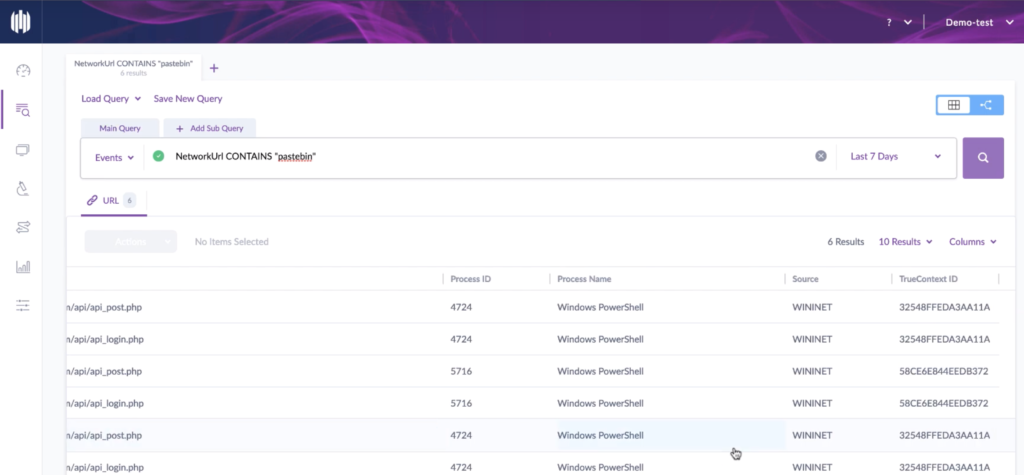
But in most cases, the site policy would be set to Protect mode, and this scenario would never occur. The threat would be automatically blocked and deleted, without any action needed by the user on the endpoint.
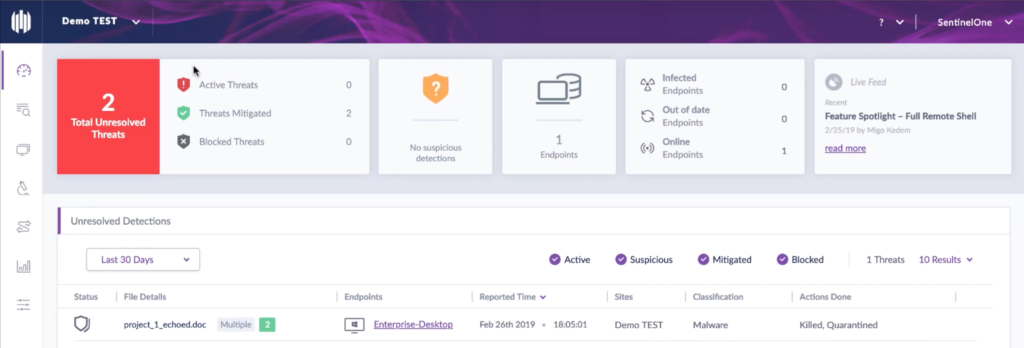
Want to see more? Come and watch the full demo at our booth.


