Samsam ransomware used in targeted attacks was first seen around 2016 and it’s set its sights on the healthcare industry. Typical ransomware victims are infected by clicking on a malicious link, opening an email attachment, or through malvertising. Samsam is unique because it infects servers directly using a vulnerability in Red Hat’s JBoss enterprise products. Hackers use tools like JexBoss, an open-source penetration testing tool, to identify unpatched vulnerabilities in JBoss application servers. Once a hacker infiltrates one of these servers, they install the Samsam ransomware onto the targeted Web application server and spread the ransomware client to Windows devices and encrypt their files.

The City of Atlanta is currently experiencing outages on various customer facing applications, including some that customers may use to pay bills or access court-related information. We will post any updates as we receive them. pic.twitter.com/kc51rojhBl
— City of Atlanta, GA (@Cityofatlanta) March 22, 2018
It followed a press conference:
Mayor @KeishaBottoms holds a press conference regarding the security breach. https://t.co/h1WlcyUc6x
— City of Atlanta, GA (@Cityofatlanta) March 22, 2018

According to 11Alive, the ransomware that was seen is Samsam. Earlier this year, Samsam infected the Colorado Department of Transportation.
Demo
Subscribe to our YouTube channel
Analysis
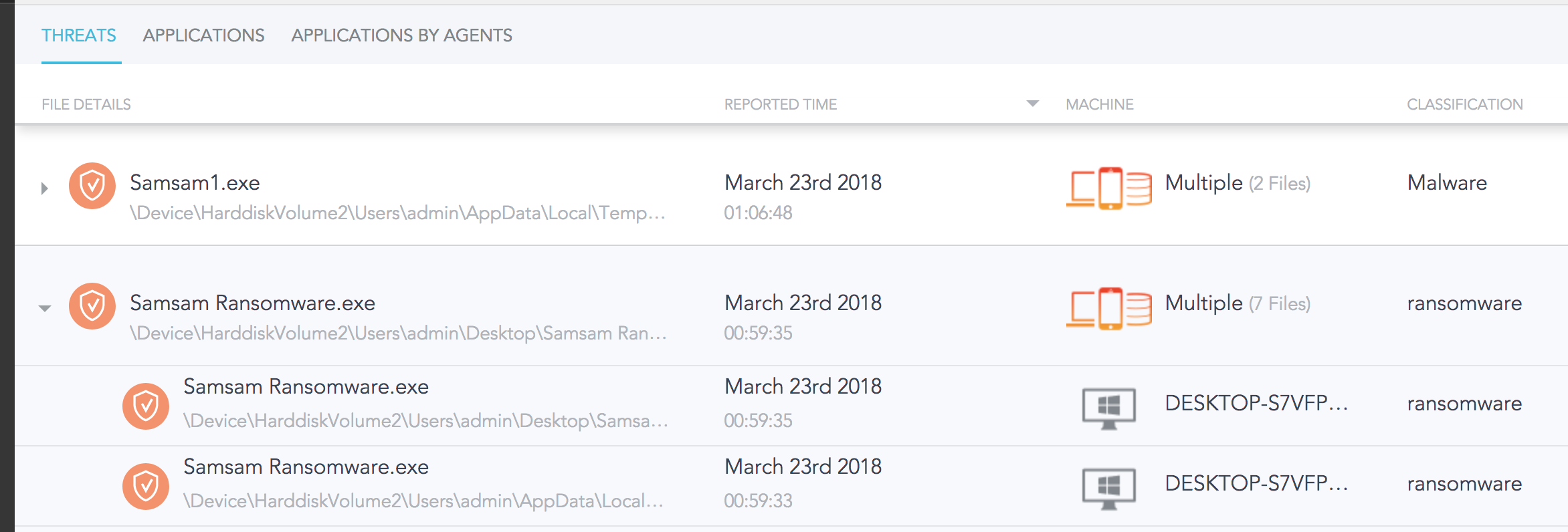
SentinelOne detects Samsam Ransomware both pre-execution and on-execution. On default policy, it will not be allowed to run. If set to Detect mode, SentinelOne detects behaviors specifically used by ransomware. Namely, scanning the hard drive for files, and replacing them with encrypted versions. Given that Samsam is deployed using an exploit, SentinelOne would detect the attack during this phase. By the Attack Storyline, we see Samsam being detected by the SentinelOne agent, preventing files from being unrecoverable encrypted. Moreover, SentinelOne would detect any lateral movement from the compromised server to other servers on the network if an exploit were to be undetected. SentinelOne’s early detection would catch the Samsam attack before the ransomware is able to run. In addition, Samsam deletes shadow copies, making it impossible for an IT Administrator to revert files and applications to their unencrypted state. SentinelOne recognizes this behavior and detects when Samsam is trying to delete shadow copies. Should something slip through the cracks, SentinelOne is able to remediate infected files and roll them back to their pre-encrypted state.
Demo
Subscribe to our YouTube channel
Analysis
SentinelOne detects Samsam Ransomware both pre-execution and on-execution. On default policy, it will not be allowed to run. If set to Detect mode, SentinelOne detects behaviors specifically used by ransomware. Namely, scanning the hard drive for files, and replacing them with encrypted versions. Given that Samsam is deployed using an exploit, SentinelOne would detect the attack during this phase. By the Attack Storyline, we see Samsam being detected by the SentinelOne agent, preventing files from being unrecoverable encrypted. Moreover, SentinelOne would detect any lateral movement from the compromised server to other servers on the network if an exploit were to be undetected. SentinelOne’s early detection would catch the Samsam attack before the ransomware is able to run. In addition, Samsam deletes shadow copies, making it impossible for an IT Administrator to revert files and applications to their unencrypted state. SentinelOne recognizes this behavior and detects when Samsam is trying to delete shadow copies. Should something slip through the cracks, SentinelOne is able to remediate infected files and roll them back to their pre-encrypted state.