Released May 25, 2022, MITRE Engenuity ATT&CK® Evaluation Trials – Deception is an inaugural evaluation that expands the ATT&CK Evaluations landscape to evaluate vendors on their deception capabilities. The evaluation can dramatically increase analyst confidence in detection via high fidelity tripwires, causing the adversary to waste time, money, or capability, and potentially provide vendors critical new insights into adversary behavior.

What Did the ATT&CK Deception Evaluation Consist Of?
For this evaluation, MITRE chose to emulate APT29 threat group. APT29 is a threat group that has been attributed to the Russian government and has operated since at least 2008. This group reportedly compromised the Democratic National Committee starting in the summer of 2015. The evaluation seeks to answer two questions:
- Did the adversary encounter the deception ? (Observe)
- Did the adversary engage in the deception? (Engage)
- Observe: Determining whether the adversary encountered deception is pretty straightforward. The evaluation can determine by running the adversary technique and recording whether it sees something different from a scenario that did not deploy deception. For the Observe portion of the evaluation, the MITRE Engenuity team did not interact with the Deception.
- Engage: In order to fully capture the value of the vendor participants’ products, the MITRE Engenuity team executed a modified scripted plan that allowed deeper interaction with the deceptions. In the Engage portion of the Evaluation, the red team would go off-script and interact with deception if it was present. When the red team engaged, they would exhaust all interactions before going back to the script.
How Did SentinelOne Perform on the ATT&CK Deception Evaluation?
As evidenced from the results of all four years of the ATT&CK Enterprise Evaluations, SentinelOne Singularity XDR platform already excels at visibility and detection. With SentinelOne’s Hologram deception solution tested in this evaluation, SentinelOne also protects the enterprise against sophisticated Identity-based attacks.
According to MITRE Engenuity’s published results, SentinelOne observed and/or engaged with most detections, identifying 17 unique techniques, including 11 techniques that targeted identities specifically. SentinelOne’s Singularity XDR platform – and specifically its Hologram deception technology – was recognized for its ability to:
- Deliver Real-time Protection Against Active Directory (AD) Compromise.
A security compromise of AD can essentially undermine the integrity of the entire enterprise enabling adversaries to steal credentials and gain access to critical systems.SentinelOne protects AD privileged credentials from theft by hiding them from attackers and replacing them with decoys. During the MITRE Deception evaluation, when the MITRE red team tried to get access to the system to get account information and credentials (T1033 T1082 T1087), the solution returned decoy credentials to them every time.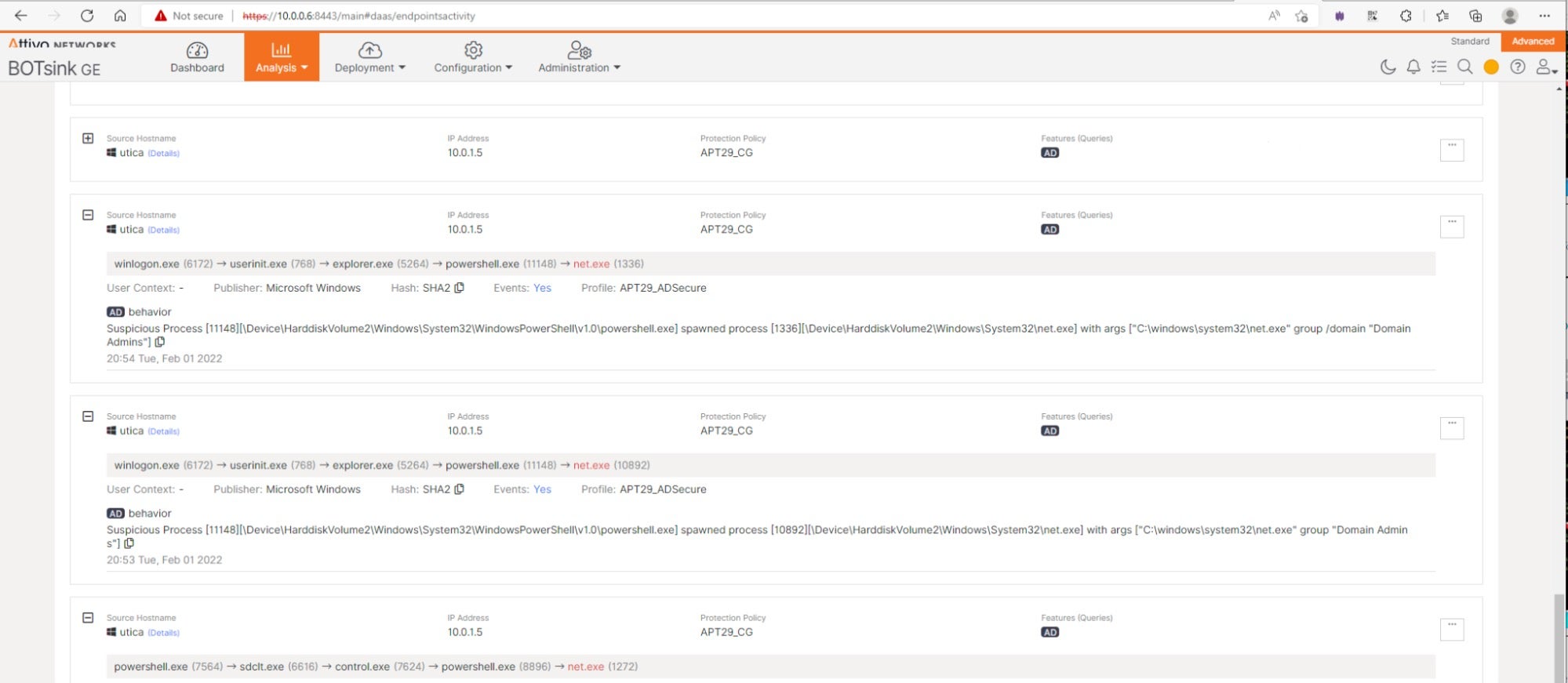
Console output showing the attempted credential enumeration This enables the security team to protect in real-time against advanced attacks targeting Active Directory.
- Mislead Attackers To Protect Critical Assets With Data Cloaking.Attackers steal and destroy information as part of their attacks, whether they seek to move deeper into the network or hold data for ransom. Preventing them from seeing or accessing local file and account information can prevent lateral movement, discovery, and data theft or destruction.
SentinelOne steers adversaries away by misdirection, showing decoys indistinguishable from production assets. During the MITRE Deception evaluation, when the red team tried to monitor system activity and queried for the computer name, SentinelOne reported decoy hostname “Newburgh” instead of the actual hostname “Utica” (T1082). When the red team tried to manipulate the software and engage with the file by browsing to it, SentinelOne hid the file from the directory listing (T1560).
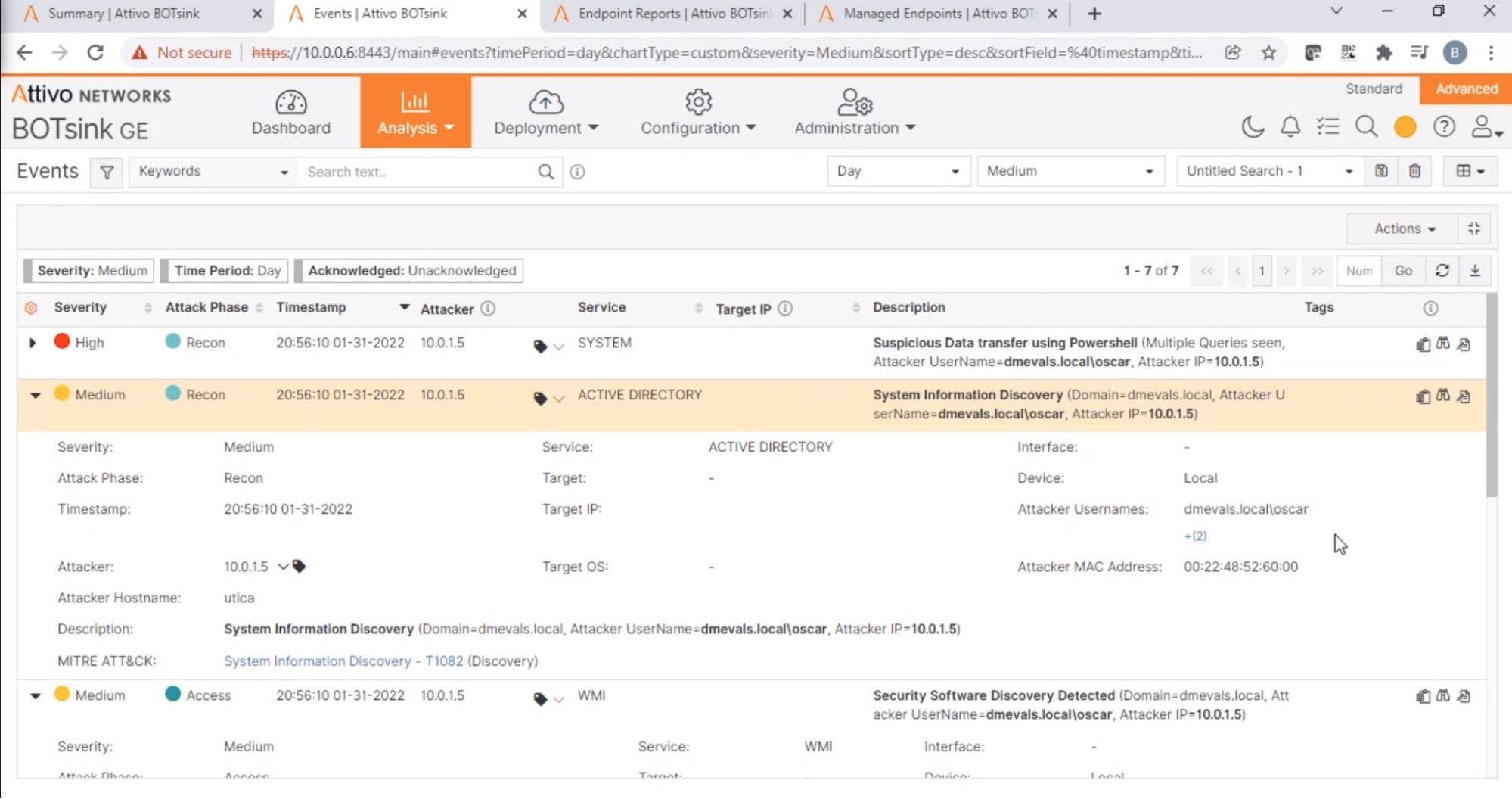
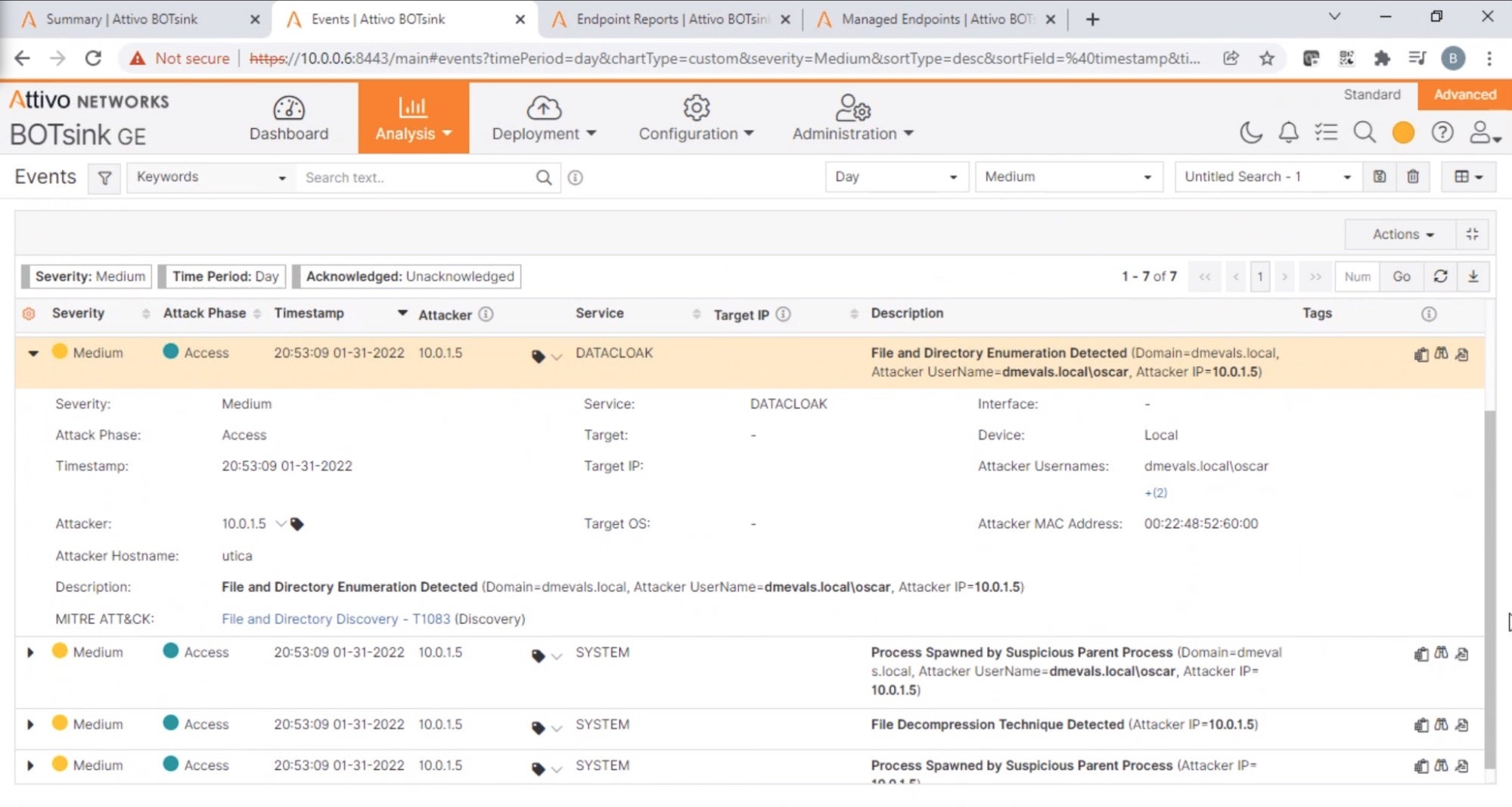
Console output showing the attempted discovery activities By preventing attackers from seeing or exploiting critical data, organizations can disrupt discovery or lateral movement activities and limit the damage from ransomware attacks.
- Stop Lateral Movement and Privilege Escalation By Preventing Pass-The-Ticket Attacks.Pass-The-Ticket attacks, such as a Golden Ticket attack or a Silver Ticket Attack, are powerful techniques adversaries employ for post-exploitation lateral movements and privilege escalation. Using these techniques, attackers can gain unlimited access to any endpoint on the network or service, potentially causing catastrophic consequences.
During the MITRE Deception Evaluation, when the red team created a ticket, the terminal output of klist reported no cached tickets. SentinelOne detected a Kerberos attack, and hid the contents of the klist command from the output (T1550).
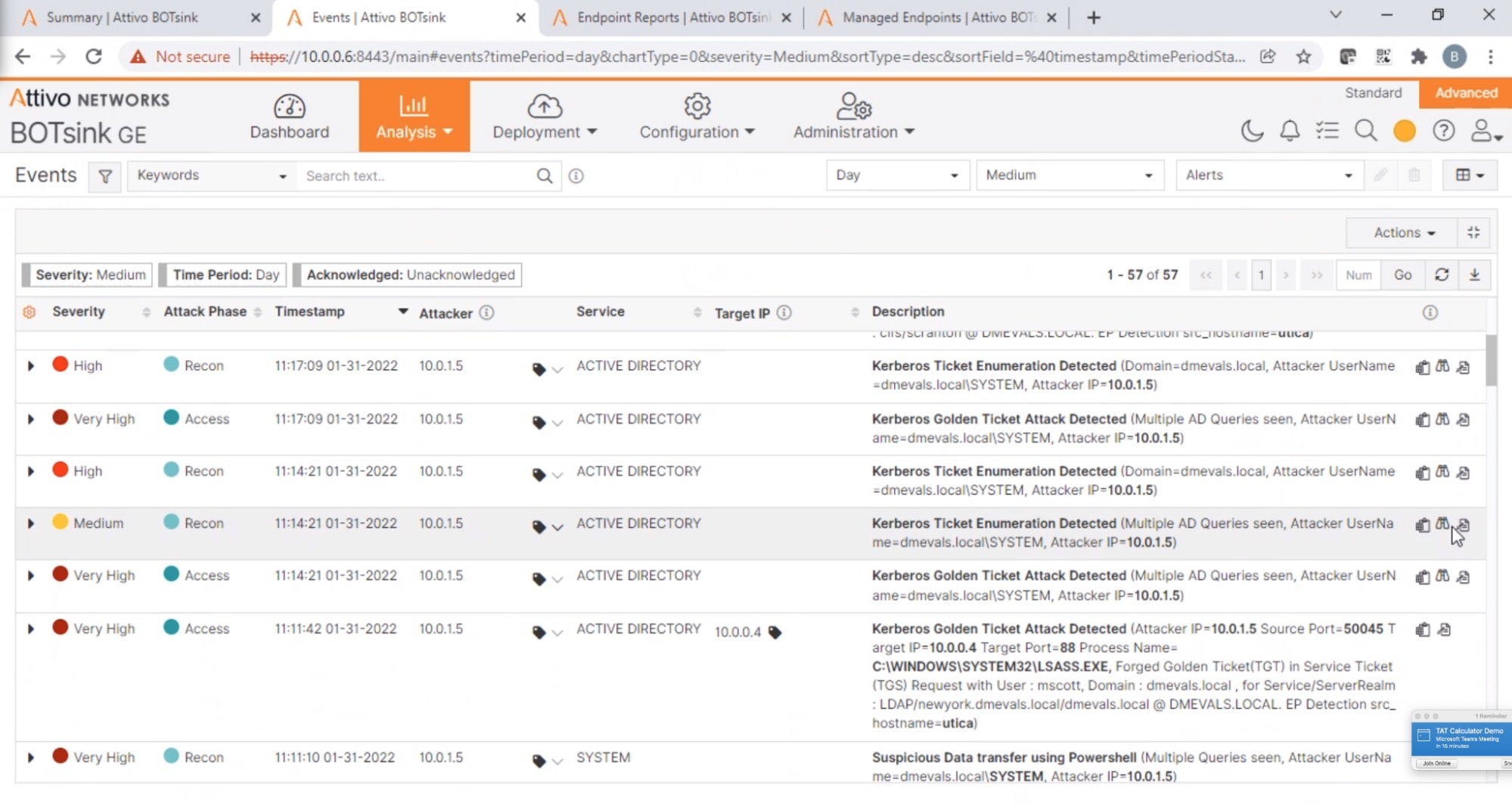
Console output showing the Pass-the-Ticket attack attempt SentinelOne denies the red team from using the Golden Ticket, even though Mimikatz generated and loaded it successfully. SentinelOne detects forged Kerberos Golden and Silver tickets and prevents lateral movement and privilege escalation when the red team uses the forged Kerberos tickets.
- Maximize Security Insight Into the Adversary Behavior.
SentinelOne’s deception technology not only serves to detect and respond to active attackers in a customer environment but also to inform and strengthen security programs in the longer term. By misdirecting attacks using SentinelOne, defenders can gain ingestible, actionable TTP information and high-confidence, substantiated attack forensics that can support investigations and develop threat intelligence. SentinelOne even lets you visualize attacks, see how they progressed over time, and map their associated events to the MITRE ATT&CK D3FEND™ matrix.
Mapping to MITRE Engage Matrix
The MITRE Engage Matrix is a framework for planning and discussing adversary engagement operations that empower organizations to engage their adversaries and achieve their cybersecurity goals. MITRE Engage seeks to help defenders by lowering the barrier to entry while raising the ceiling of expertise to use adversary engagement technologies. SentinelOne provides the most extensive capabilities to implement the activities outlined in the Engage Matrix, covering 38 of the 41 areas in the Operations phase.
Why SentinelOne? Why Should It Matter To You?
Top Coverage for Both Enterprise ATT&CK + Deception ATT&CK Frameworks
As a leader across MITRE Enterprise ATT&CK Evaluations for the third consecutive year and a leader in the inaugural MITRE ATT&CK Deception Evaluation Trial, SentinelOne once again demonstrate its commitment to push the boundaries to help enterprises gain control of their dynamic attack surface.
As the first and only XDR vendor to participate and lead the ATT&CK Deception Evaluation, Singularity XDR platform demonstrates the most powerful, autonomous XDR platform, reducing the enterprise attack surface across human, device, and cloud attack surfaces. The solution provides an effective combination of prevention, protection, detection, and deception capabilities to stop attackers early whether they are attempting to establish a beachhead inside the network or compromising identity data to move laterally, escalate privileges, and acquire targets.
SentinelOne is an enthusiastic supporter of what MITRE does, bringing transparent and open evaluation methodologies to the security industry and participating in all the evaluations has become an essential practice that we have used to improve our products further.
To learn more about SentinelOne’s results on the ATT&CK® Deception Evaluations, visit https://www.sentinelone.com/lp/mitre-deception/
To learn more about SentinelOne’s results on the fourth round of ATT&CK® Enterprise Evaluations, visit: https://www.sentinelone.com/lp/mitre/.


