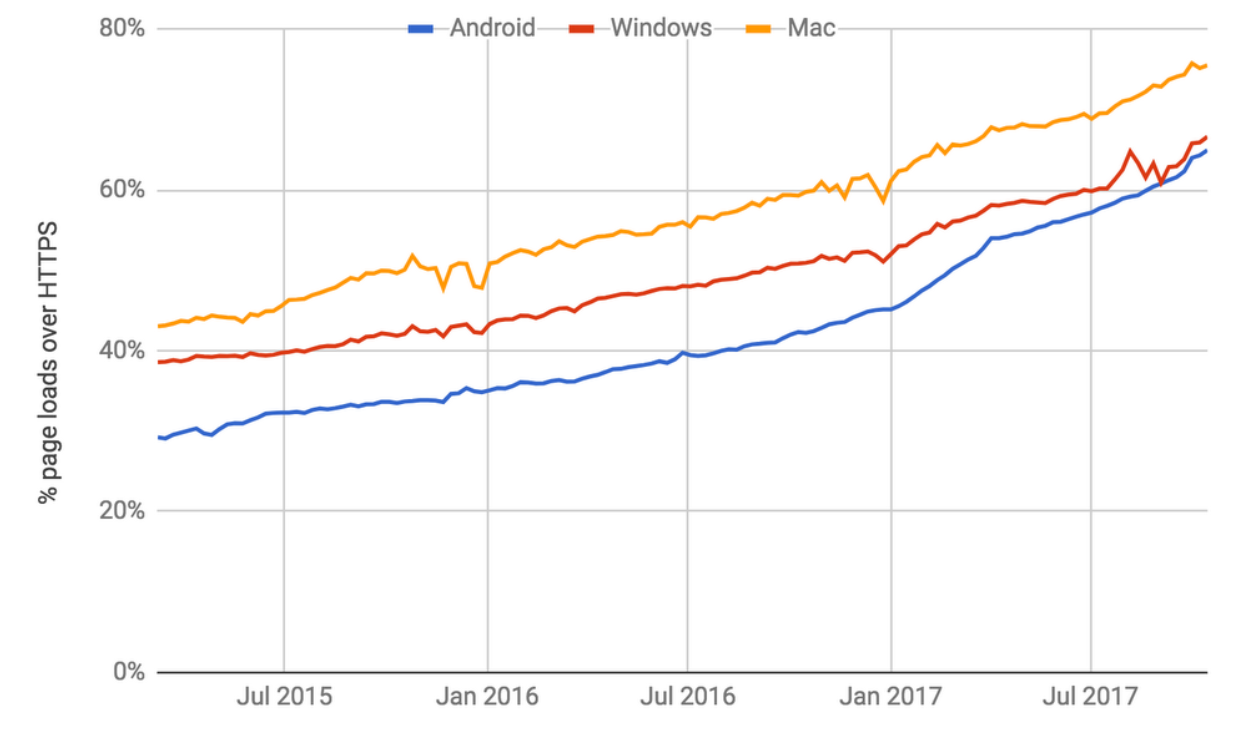
As of today, most of the network traffic is encrypted. This improves privacy but eliminates the option for network product to see the traffic. Google played a significant role, has pressure on websites to adopt HTTPS and recently announced Jigsaw – allowing anyone to set up and run their own ‘homebrew’ VPN. According to Google:
- Over 68% of Chrome traffic on both Android and Windows is now protected
- Over 78% of Chrome traffic on both Chrome OS and Mac is now protected
- 81 of the top 100 sites on the web use HTTPS by default
The Bad Guys Know Network Security Products Cannot See Encrypted Traffic
Despite being one of the oldest tricks on the web, phishing continues to be a significant problem for organizations. Your users are your assets, but also part of the security problem.
As per our study of 500 business leaders over the US, UK, Germany, and France uncovered how Ransomware effects their business we can see several trends:
- 66% of the enterprises experienced ransomware originating from either a phishing, email or social networks.
- 44% of the undertakings experienced from Drive-by-download caused by clicking on a compromised website.
Phishing sites are trying to trick users into entering credentials, personal information, and so on. For this, they want to avoid the “not secured” indication.
SentinelOne will automatically mitigate malicious attempts incident by incident, while Deep Visibility will get to the root of these. By looking into the encrypted traffic, you can see as no other solution can, the chain of events leading to the compromise attempts are revealed.
Demo
In the following video, you can see how to identify phishing attempts on your users.
Subscribe to SentinelOne YouTube channel
Step by step
The starting point would be a twit stating:
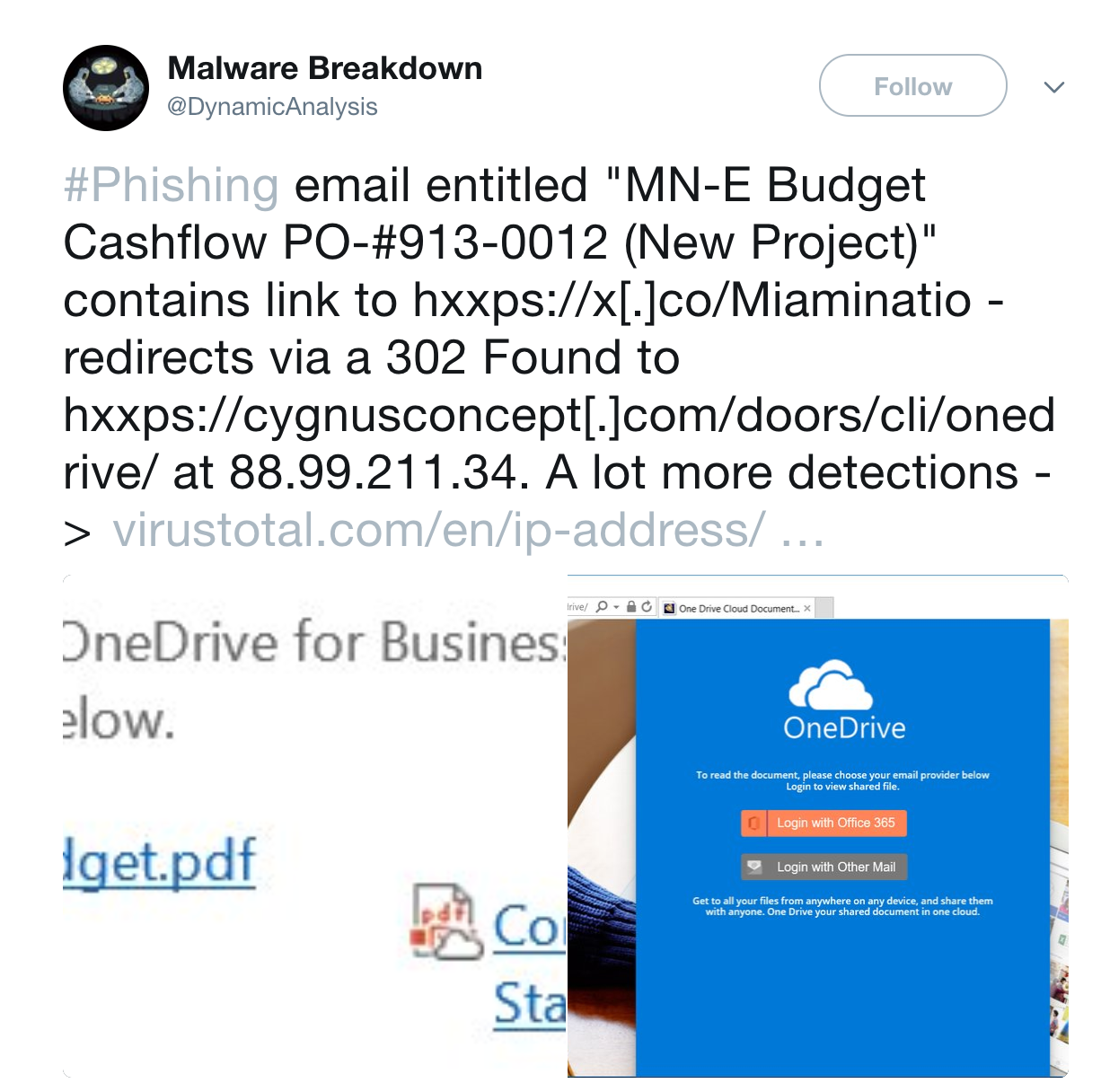
Now, you might want to look if there is any evidence of this campaign inside your network. A simple search would show you 21 entries of this encrypted URL.
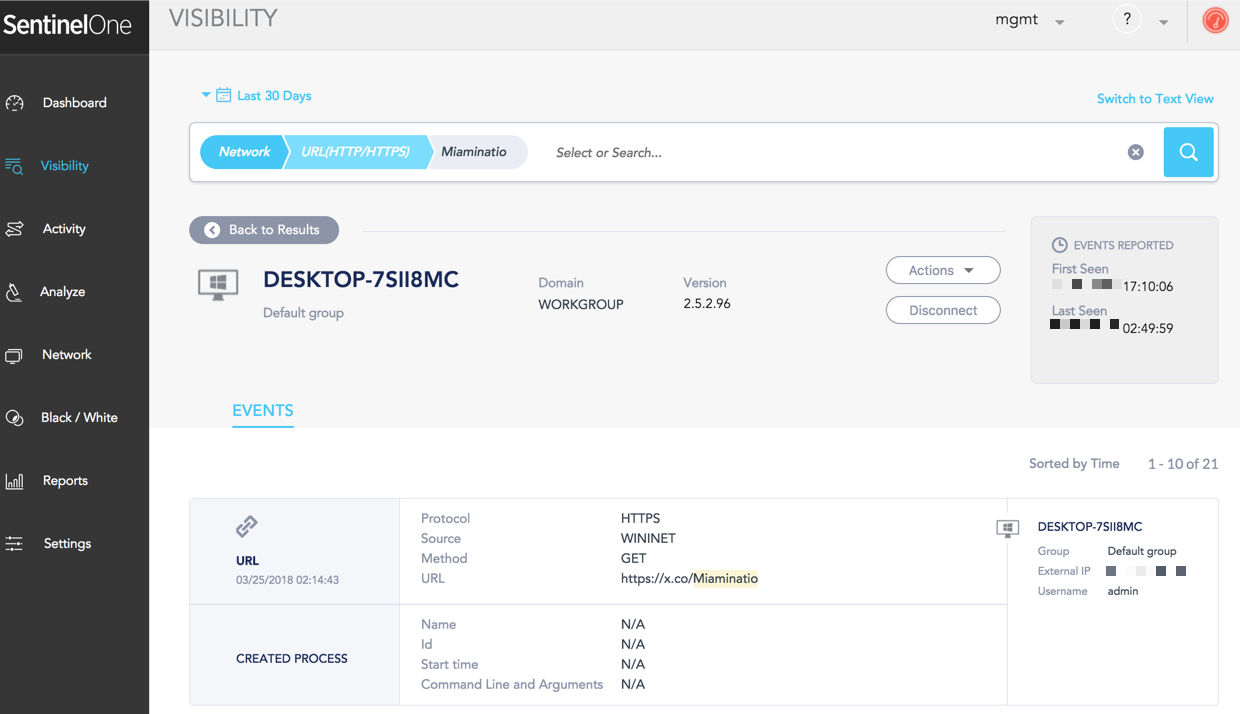
Determination
SentinelOne Deep visibility is a simple way to have visibility on your assets, including the increasing blind spots of encrypted traffic. It will allow your team to understand better the security incidents, monitor phishing attempts on your users, identity data leakage ensure cross assets and all these is a simple and straightforward interface that allows you to automate and connect it to other products on your portfolio.

