It was published recently that a malware campaign tried to infect 400,000 users in 12 hours on March 6, 2018. The malware is a variant of Dofoil, carrying a cryptocurrency miner.
It usually comes to the infected machine through malicious spam email with a DOC or ZIP file attachment. It then connects to the C&C server to get commands, download and execute malicious files.
As published by bleepingcomputer, the malicious code spins off a second explorer.exe process that downloads and runs cryptocurrency miner that pretends to be a legitimate Windows file.
The good news is that SentinelOne customers are fully protected from Dofoil. Within milliseconds, SentinelOne technology detects Dofoil as harmful, classifies and prevents it from executing.
Demo
On this demo, you can see how SentinelOne version 2.5 with a default policy is capable of preventing three different samples of Dofoil, Even when offline.
Once the device is offline, we have copied the malicious samples to the desktop, and immediately the agent quarantined the files, blocking and preventing any chance for the Trojan ever to run and do harm.
Subscribe to our YouTube channel
Later, we allowed it to run to see how SentinelOne behavioral AI detects it. Here is how far it could go before mitigated.
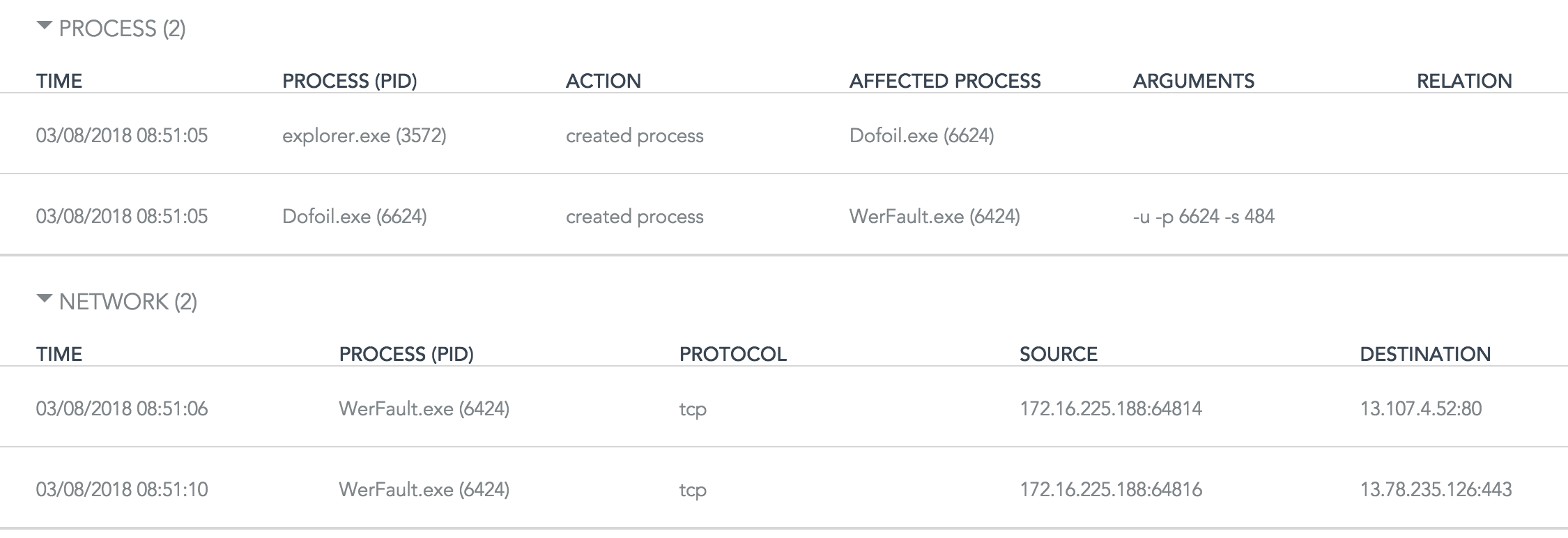
On the detection, we observed the following indicators

The SentinelOne Console has classified the samples, as seen here. This feature is available starting Banff management version that is now in EA.
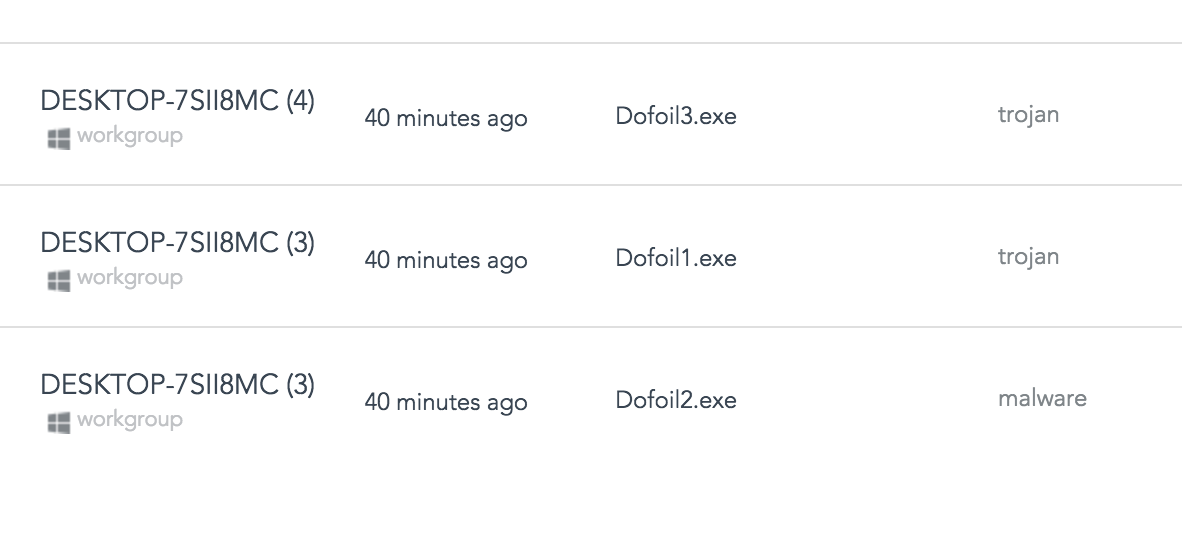
Conclusion
When so many devices getting infected so quick, it is clear that what’s needed is an automated solution that is capable of preventing it milliseconds. The cost to the business of having so many devices infected is enormous. If SentinelOne already protects you, we got you covered.


