The Winter Olympics this year is being held in Pyeongchang, South Korea. It’s been reported that some of their non-critical computer systems were attacked by malware during the opening ceremony. Luckily, officials were able to completely recover within around 12 hours. The malware has been dubbed “Olympic Destroyer“, which is a fitting name since the goal of the malware seems to be pure destruction.
Whenever we see an important malware outbreak, we always try and see if SentinelOne would have protected against the threat. We are pleased to say that we do indeed detect Olympic Destroyer and SentinelOne customers are protected.
SentinelOne uses multiple detection mechanisms which can be grouped into two types: those which look at the file and those which observe how the machine behaves. For example, our Static AI engine looks at the file and uses some pretty fancy machine learning to classify if the file is malicious or not. This is great because it can eliminate malware before it has a chance to execute, and in our tests, Static AI detected the Olympic Destroyer sample soon after it’s dropped on the desktop. Below is a video showing the detection:
Subscribe to our YouTube channel
Digging Deeper
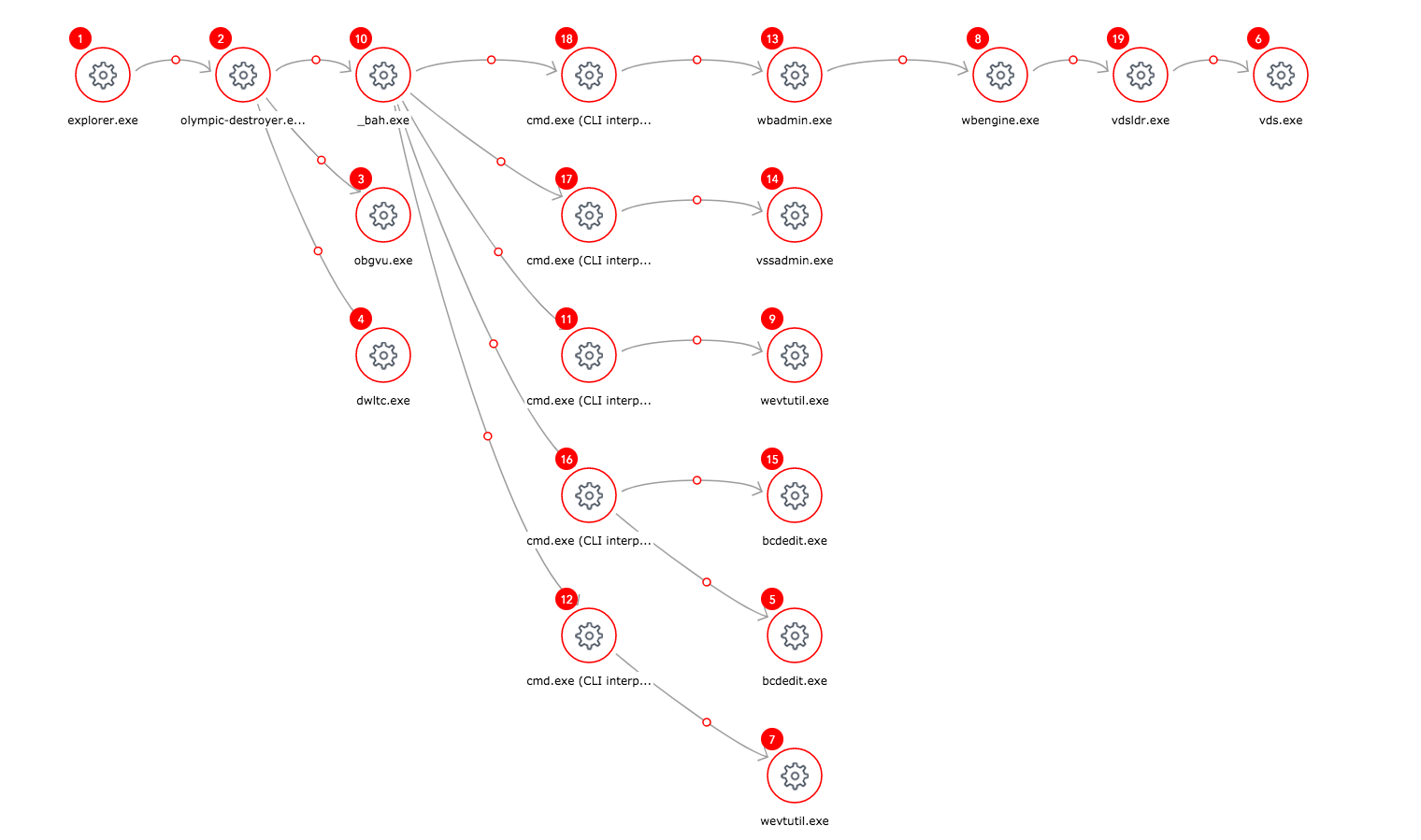
While static detection mechanisms like Static AI are important and useful, we also wanted to know if our Dynamic Behavior Tracking (DBT) engine would detect the malware. DBT monitors how the system behaves and looks for any malicious activity, so it can detect file-less attacks, exploits, and in general, it’s much harder for malware to hide from it. To test DBT, we intentionally disabled Static AI to allow the malware to execute. Happily, the DBT engine detected the malware within a few seconds after running it, and SentinelOne was able to completely prevent any damage. Since the malware executed for a few seconds, our agent was able to collect a lot of interesting forensics information. For example, you could see the original sample drops several payloads, tries to delete shadow backups copies, clear event logs, and so on. Below is a screenshot showing the “attack storyline”:
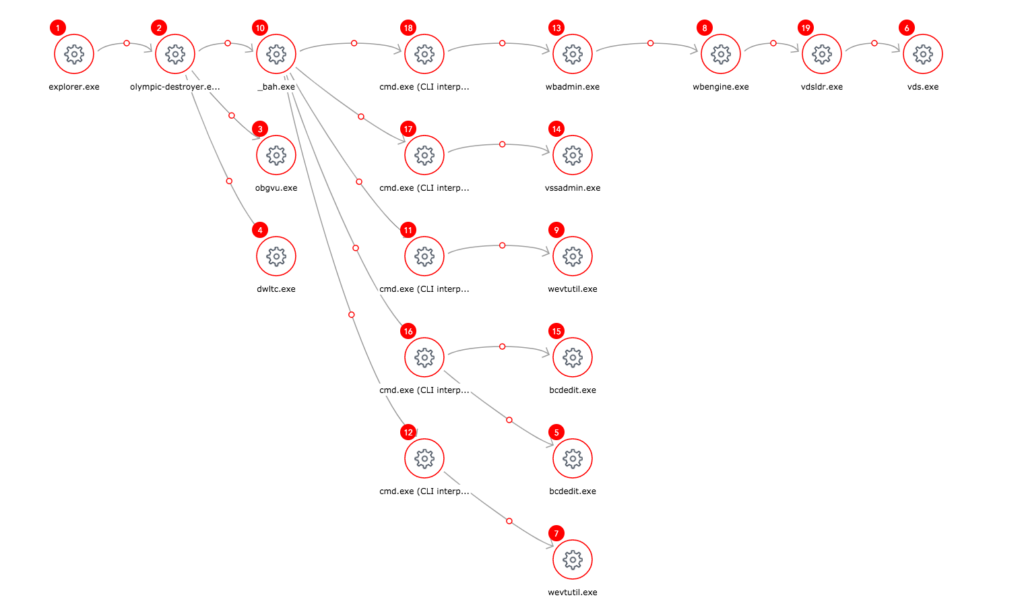
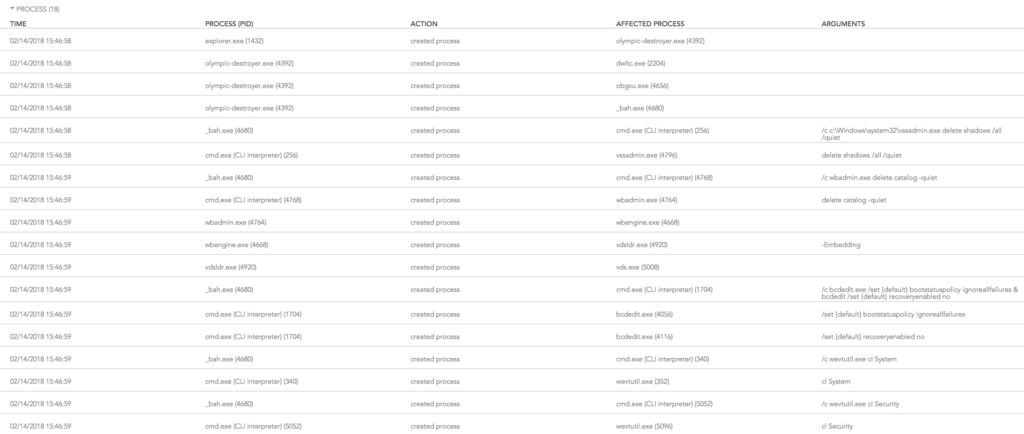
From the above picture, Olympic-destroyer.exe starts a few of it’s randomly named payloads: _bah.exe, obgvu.exe, dwltc.exe. Below is a screenshot showing some of the process creation information gathered from running the sample:
From this, you can see all of the executables started as a result of double clicking olympic-destroyer.exe along with the exact command line arguments. You can see the malware attempt to delete multiple types of backups, disable Windows recovery, and clear event logs.