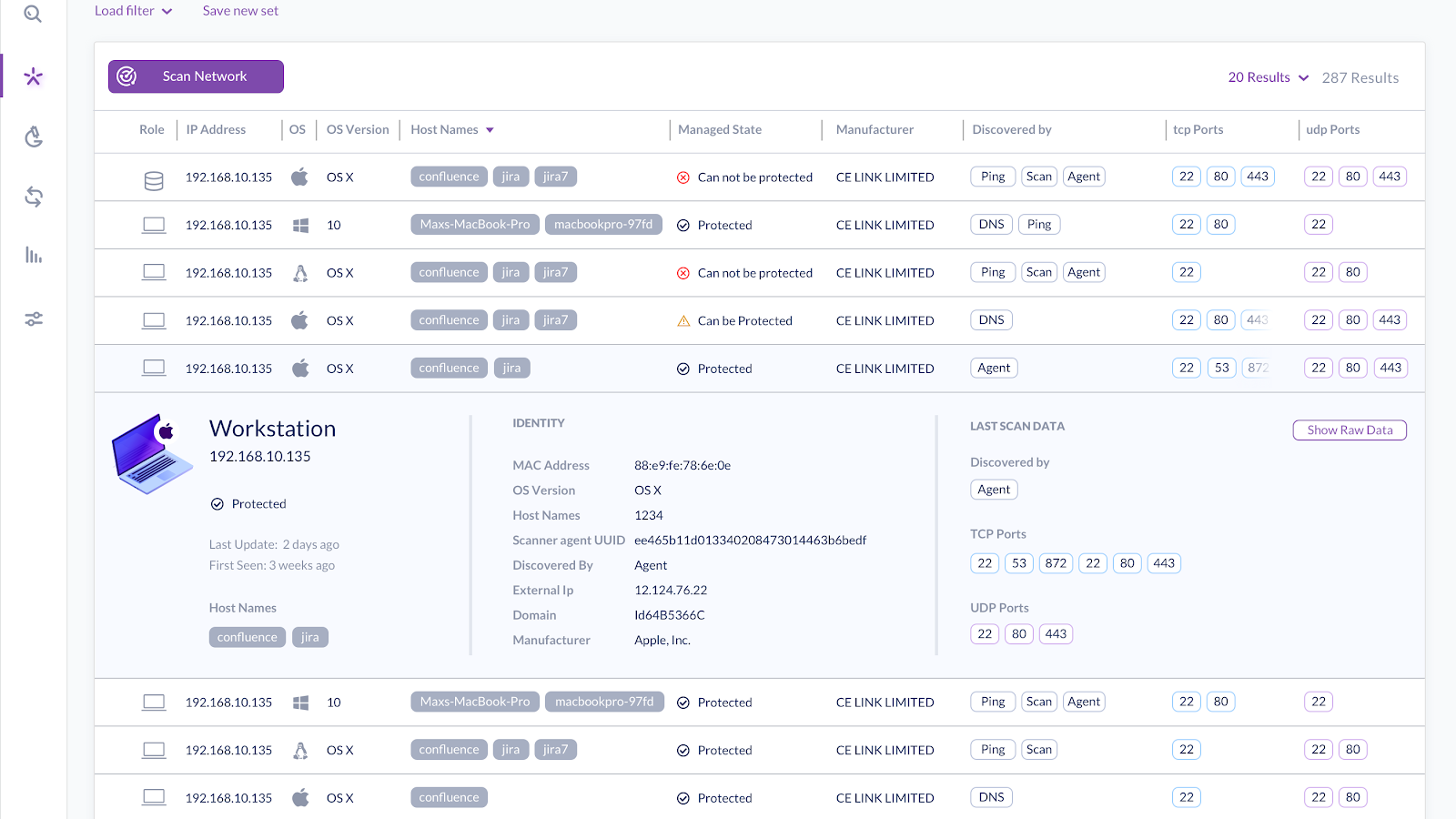
Ranger creates visibility into your network by using distributed passive and active mapping techniques to discover running services, unmanaged endpoints, IoT devices, and mobiles.

Why Does Enterprise Need This?
The number of devices running on networks is increasing as people bring their personal phones, laptops, and smart devices into the workplace. Additionally, more and more Internet of Things (IoT), Operational Technology (OT), and smart appliances are being added to the network. All these devices are becoming increasingly intelligent and complex. This complexity can lead to bugs, and bugs can lead to vulnerabilities. This means it’s increasingly important for network administrators to have a way of keeping inventory of what’s on their network. Ranger generates this inventory automatically and maintains itself over time.
Ranger also makes it easy to find unmanaged endpoints. You want to make sure every device joining your network is protected, but this can be tricky with an increasing number of devices and limited IT personnel. With Ranger, a list of unmanaged endpoints is just a few clicks away.
How Does Ranger Work?
Ranger turns existing SentinelOne agents into a distributed sensor network which combines passive and active reconnaissance techniques to build a map of everything on the network.
Since it’s not enough to simply know you have a device on your network, Ranger also tries to fingerprint the operating system and the device’s role. This means you can easily look at all of your printers, mobile devices, Linux servers, and so on. Fingerprinting also allows us to be very confident when we say an endpoint is unmanaged because we won’t be alerting on incompatible devices such as VoIP devices, IP cameras, printers, and so on.
It’s well known that Firewalls and IDS systems respond poorly to normal network and vulnerability scanning attempts, and many IoT devices cannot handle the strain of being scanned normally. We deal with this problem in a variety of ways. First, our passive techniques are quite good at finding all hosts on the same subnet as our agents. Second, we don’t use a single endpoint to do all of the mapping — the work is intelligently divided amongst all agents. This means no one particular endpoint is noisy or suspicious. Finally, our probes are incredibly lightweight. Nmap takes 10x to 20x more traffic and Nessus requires 100x to 500x! This is because our probes are very targeted and precise.
What We Tried
There’s no general solution for scanning networks. Each one is a unique snowflake and can be arbitrarily complex. Because of this, we wanted to try a bunch of different approaches and see what worked, what didn’t, and where the pain was. We knew from the beginning it was key to leverage existing agent deployments. It’s so hard and expensive for large enterprises to roll out a new agent, and many enterprises are experiencing “agent fatigue” and are looking to consolidate agents as much as possible.
Before we had an agent built, we experimented by modifying our network to redirect all traffic through a Suricata tap. The benefit of this was that it was very simple to collect data and we didn’t need to build an agent. However, we quickly ran into problems as the amount of traffic was overwhelming the Suricata box, even on a small network. We could also only see endpoints which talked with the internet. In the end, we gave up on this approach and moved everything to an agent.
The next difficulty we had was deciding how to prioritize implementing passive and active network mapping techniques. There are thousands of ports worth probing and dozens of protocols a device might speak. We spent a lot of time winnowing down the ports to only the most informative and implementing the protocols which were the most useful.
How Is Ranger Different?
The main difference is that we use our existing agents as sensors. This means you don’t have to install yet another agent for Ranger to work.
Other products on the market require adding physical appliances to the network and directing traffic there. This can be annoying to scale especially for large and busy networks.
Some products require you to capture the traffic yourself and upload the logs to a server for processing. This is probably the easiest solution to implement, but it puts a heavy burden on the user to collect enough information to get a clear view of the network. If you have many different sites and networks, you’ll have to monitor traffic at all of them.
Conclusion
Ranger gives you a window into your network, and this will be increasingly important and valuable as more devices start living on the network. And you don’t need to install anything new to use this feature — it’s all part of the existing SentinelOne agent.
SentinelOne Ranger is now in alpha and expected to be available to all our customers during summer 2019.