What do the Target attack, Stuxnet worm and ATM malware all have in common? That’s right, they are all examples of supply chain attacks. Businesses are becoming increasingly vulnerable to software supply chain attacks. Learn what they are and how to defend against them.

We’re all familiar with the need to defend the enterprise against adversaries, but it’s important to understand that friends can also become foes. In this post, however, we won’t be talking about insider threats, but vulnerabilities that come from trusted vendors. Software supply chain attacks are on the rise, and they exploit the vulnerable underbelly of many businesses: third-party software that may have been validated in the past but not at the time of an attack.
What Are Supply Chain Attacks?
Rather than attacking an organization directly, a software supply chain attack targets the vendors of apps and other code used by the organization. Typically, the bad actors will look to exploit some weakness in the vendor’s development cycle and attempt to inject malicious code into a signed and certified application. By contaminating update servers or development tools, inserting code into executables or simply replacing real packages with fake ones, adversaries can gain access to victims further along the supply chain.
Two notorious examples that gained much attention were the 2013-4 attack on Target, in which 40 million customers’ credit and debit cards became susceptible to fraud after the POS system in over 1800 stores was infected with malware, and the Stuxnet worm – the world’s first recorded use of a cyber weapon – that impacted the Iranian Bushehr Nuclear Power plant via malicious USB sticks. Other notable cases of supply chain attacks have hit ATMs in Eastern Europe, the US, India and China, allowing criminals to drain the machines of cash and then remove the malware. The malware could only be installed by a person or process with insider access.
Software supply chain attacks pose great danger since they can be difficult to detect by legacy AV solutions. With many 3rd-party software offerings being dependent on external libraries themselves, the compromise could be hidden several layers removed from the intended target.
Why Are Supply Chain Attacks Increasing?
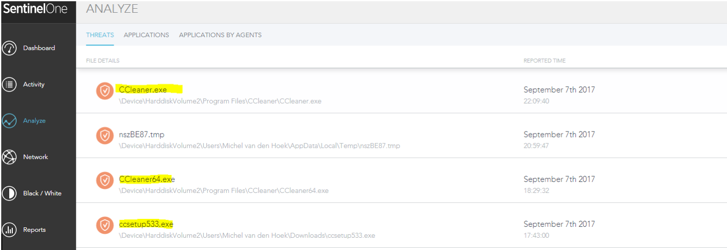
There’s one simple answer to this question: greater rewards for less work. From the attacker’s point of view, the rewards of a single-hack on widely-used software compared to just striking at one corporate target can be huge. It could net hundreds, thousands or even millions of victims: in September 2017, SentinelOne detected and blocked a threat from what should have been a safe application. The customer, initially thinking the detection must be a false positive, reported that one particular version of CCleaner was being detected as malicious. As soon became widely-known, this was no false positive. A few weeks previously the attackers had replaced the original version on the official website with a backdoored version. While the SentinelOne customer was automatically protected, the malicious software had already been downloaded by 2.27 million users worldwide by the time the threat became public.
How Easy Are Supply Chain Attacks?
The motivation for supply chain attacks is clearly there for attackers, but how easy are they to pull off?
That all depends on the security hygiene of an enterprise’s third-party vendors. It only takes one chink in the armour of any single dependency to result in a devastating compromise. Banks and businesses in the Ukraine found this out the hard way in 2017, when developer Intellect Service lost control of the update servers for their popular M.E.Doc accounting software. That software was used by some 80% of the Ukraine’s financial services and had around 1 million installations. Hackers penetrated the company’s network and redirected update requests to a malicious server that delivered malware to victims.
How Widespread Are Software Supply Chain Attacks?
Supply chain attacks have hit all major platforms in recent years. Apple’s Mac and iOS platforms were spectacularly hit in 2015 with XcodeGhost, an infected version of Apple’s Xcode development environment. By providing developers with a tainted version of Apple’s IDE, attackers were able to insert malicious code in any app that was built with it. Over 4000 apps were known to be infected with the code. Even after the threat became public, hundreds of enterprises still carried infected software some two months later.
Other notable supply chain attacks include compromises of video conversion tool HandBrake and bitTorrent client Transmission, with the latter being hacked twice through its update mechanism.
More attractive than attacking applications directly, libraries and packages are also ripe for exploitation. A frightening proof of concept about how vulnerable npm packages are in early 2018 turned out to have a real-life example when the popular event-stream code library was usurped by a malicious developer. Among event-stream’s 2 million or so downloaders are a number of Fortune 500 companies.
In a more recent example, the popular Python PyPI repository has also been targeted by malicious coders. In October 2018, a cryptocurrency clipboard hijacker called “colourama” was discovered in PyPI that was typo-squatting the legitimate “colorama” package. The malware targets Windows machines and looks for bitcoin addresses copied to the clipboard. If found, the code replaces the address on the clipboard with an address belonging to the attacker.
How Can Enterprise Defend Against Supply Chain Attacks?
Software supply chain attacks rely on exploiting the trust between vendors and users. When attackers compromise software that is signed and certified, users are exposed if they do not have adequate protection. The basic principle to help avoid becoming a victim of a software supply chain attack is to have security software that doesn’t rely on reputation for detection. For that reason, be sure to avoid or replace security solutions that rely heavily on whitelisting with a modern, behavioural AI solution that can recognize novel threats at machine-speed.
NextGen AV solutions like SentinelOne provide defense-in-depth with a focus on what processes on your network are doing rather than what they are or where they come from. In this way, like the SentinelOne customer protected against the CCleaner supply chain attack we mentioned earlier, your organization can be sure that if a process that is supposedly trusted starts behaving maliciously, you can block and remove it before an attack gets started.


