The Good
Are cyberattacks on cyberattackers (aka ‘hacking back’) good news or bad news? While that question elicits mixed responses among security professionals, we can’t help but feel that when darknet criminals start to ask “are darkweb forums safe anymore?” this must be a good thing for the security of the rest of us. This week has seen the latest in a series of attacks on darknet forums where criminals regularly sell malware, credit card details, account credentials and leaked or stolen data.
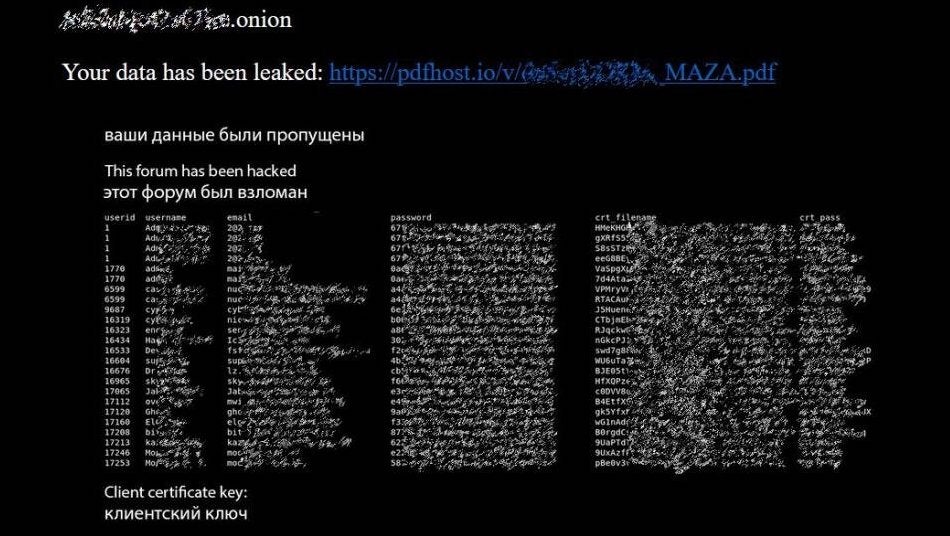
Mazafuka (aka ‘Maza’) is a darknet criminal forum that’s been around so long many cyber pros were surprised to hear it was still in existence this week, when news broke that the Russian cybercrime forum had been the victim of a hack. Almost 3,000 user records containing user IDs, names, passwords and other social media contact info were leaked, with the latter likely of huge interest to LEAs around the world.
Several weeks previously, another Russian-speaking hacker forum ‘Verified’ was forcibly taken over by unknown intruders. Hacktivists, deep-cover law enforcement or a rival gang are all possibilities, although in a public post the attackers claimed to be “like-minded” and insisted they only wanted to develop and improve the site. Whether the shady users of the site will trust this new enforced management remains to be seen. These attacks followed in the wake of similar hacks on carding forum ‘Club2Crd’ and darknet website ‘Dread’ last month.
If such hacks are disrupting the ability of cyber criminals to profit from their misdeeds, we reckon it’s worth counting as good news. And besides, whether you take pleasure in the bad guys getting a taste of their own medicine or not, it just goes to show you can never take cybersecurity for granted, whichever side of the law you are on.
The Bad
A Chinese APT group that Microsoft have dubbed ‘Hafnium’ (otherwise known as the chemical element Hf) have been fingered for ITW attacks targeting Microsoft Exchange Server, it was revealed this week. The Redwood tech giant was forced to release an out-of-band security update to patch seven vulnerabilities affecting MS Exchange products as old as 2013.
Microsoft said that they were aware of active exploits in the wild leveraging four of the patched vulnerabilities. CISA also released an advisory the following day warning that attackers could use the flaws to gain persistent system access and control of an enterprise network, stating that this “poses an unacceptable risk to Federal Civilian Executive Branch agencies and requires emergency action”.

In a separate post, Microsoft said the state-sponsored Hafnium group had been utilizing the zero day vulnerabilities to steal data from U.S. organizations, specifically via CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, and CVE-2021-27065.
SentinelOne has released its own advisory, technical review, IoCs and guidance for SentinelOne customers here.
The Ugly
Nobody expected the hack of the year (decade? century?), aka the SolarWinds breach, to go away anytime soon, and so it’s not entirely a surprise to hear that Microsoft have reported three new strains of malware likely associated with the APT espionage campaign, widely-believed to be of Russian intelligence origin.
In a report yesterday, Microsoft researchers dubbed the three new strains Sibot, GoldFinder and GoldMax (the latter is also being tracked as SUNSHUTTLE by FireEye). While we’re on naming conventions, Microsoft have also chosen to label the APT behind the entire campaign as ‘Nobelium’ (which happens to be a synthetic, radioactive chemical element with the atomic number of 102, in case you were wondering!); the significance of the name choices was not explained.
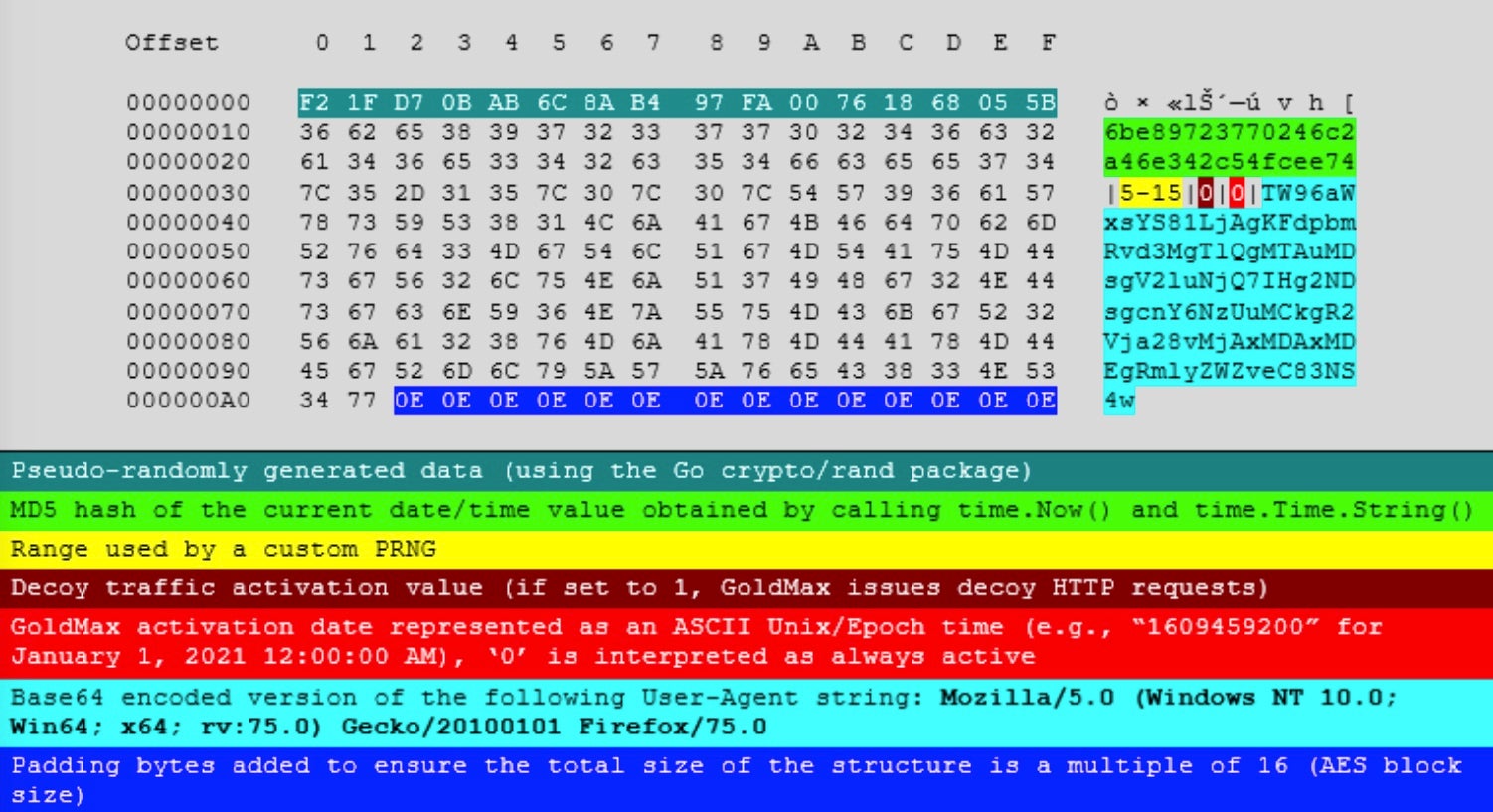
Sibot refers to three variants of a VBScript that download a malicious DLL from a compromised website, while GoldFinder and GoldMax are both malware tools written in Go (Golang).
GoldFinder appears to be a custom HTTP tracer tool for logging the route a packet takes to reach the attacker’s C2 server. The threat actors can use the tool to identify proxy servers and network security devices, aiding discovery of other potential points of ingress. GoldMax functions as a backdoor and allows the attacker to securely communicate with a C2 and to launch commands on the victim’s device. Comprehensive details and IoCs are available here.
The significance of finding further late-stage malware tools in compromised systems should not be underestimated. The full impact of the SolarWinds breach is still unfolding, and enterprise security teams are encouraged to remain vigilant and proactive in following up on these developments.