The Good
This week Microsoft, along with an extensive list of partners, took steps to successfully cripple one of the most prolific malicious botnets of the last decade. The Necurs botnet has been responsible for much of the pharmaceutical, stock pump-and-dump, dating and other common spam lures since 2012, and operated at its peak between 2015 and 2017. It was also heavily leveraged to distribute prominent malware families including GameOver Zeus, FlawedAmmyy, Locky, Dridex, Scarab, Trickbot and many others.
The turning point came once Microsoft and industry partners were able to uncover the inner-workings of the Necurs DGA (Domain Generation Algorithm), the component of the network responsible for generating and registering C2 (Command-and-control) domains. According to Microsoft’s Digital Crime Unit, they were able to “accurately predict over six million unique domains that would be created in the next 25 months”. As a result, Microsoft were able to prevent these generated domains from being registered. In addition, a court order issued on March 5th allowed Microsoft to seize existing domains, effectively crippling the botnet’s current and future infrastructure.
This was a coordinated effort between Microsoft, ISPs, various domain registries, as well as law enforcement entities in India, Japan, France, Mexico, Colombia and many others. We know this is a long slow-burn of a fight, and there is always a chance that the botnet could rebound (ex: Kelihos), but this is a valiant and commendable effort. Cheers to all those involved and keep up the good fight.
The Bad
Alas, Microsoft are also in the bad news this week after the discovery of a critical and potentially wormable vulnerability in Microsoft’s SMBv3, CVE-2020-0796. Essentially, this is an RCE (remote code execution) flaw in Microsoft Server Message Block 3.1.1 (SMBv3) when handling certain requests. An attacker could exploit the flaw by transmitting a specially crafted packet and gain arbitrary code execution on the targeted server or client. The flaw affects Microsoft Windows 10 Versions 1903 & 1909 (including Windows Server) across supported architectures (x32, x64, ARM64). According to various advisories (published and pulled and republished in the last 36 hours) the issue comes down to a memory corruption condition stemming from a buffer overflow in affected SMB servers. Microsoft has provided an update here and a workaround in their updated advisory for those who cannot patch.
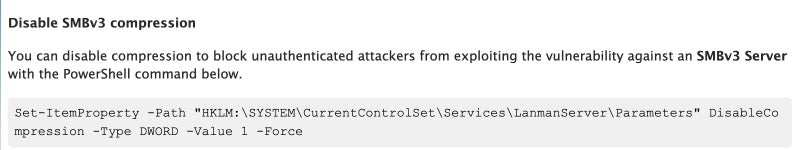
Set-ItemProperty -Path "HKLM:SYSTEMCurrentControlSetServicesLanmanServerParameters" DisableCompression -Type DWORD -Value 1 -Force
The Ugly
Now more than ever, we all need to be extra vigilant and aware of our information sources. We’ve already seen plenty of spam campaigns and blatant misinformation regarding Covid-19/Coronavirus, with the unscrupulous only too happy to try and cash in on a worried, information-hungry public. Sadly, but predictably, this week saw the emergence of an exploit kit playing on those same fears, the “Corona Virus Map Phish Method” kit, which is being sold in multiple underground forums.
The kit in question is offered for $200 as is, or $700 with the seller’s own code signing certificate. It comes with a preloader that can be attached to an email. The code loads a working map displaying infection data on the victim’s machine, as well as the buyer’s payload of choice. The payload can be embedded directly or called via embedded URL, and the whole package can be bundled and sent via email without triggering a block by popular email providers.
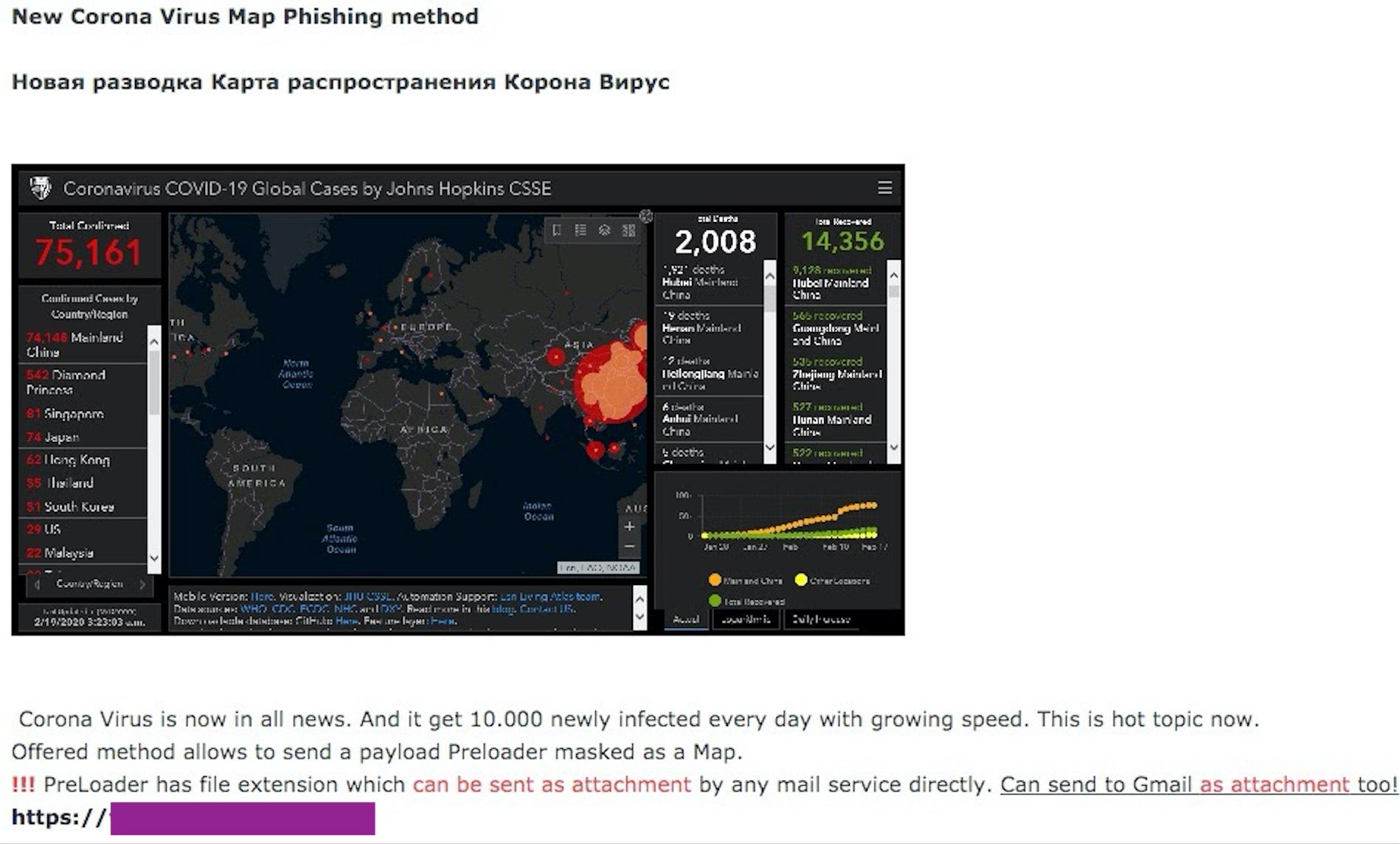
One of the sites hosting a malicious map was highlighted in HC3’s (Health Sector Cybersecurity Coordination Center) March 10 alert, Fake Online Coronavirus Map Delivers Well-known Malware. In the scenario covered in the alert, the site was used to drop the AZORult trojan. That highlighted example is a web-centric attack, but it should be noted that we have seen pointers to these malicious sites spread via email and social media threads as well.
Using this against the unassuming public is shameful, but at the same time, unfortunately, it reportedly works on “all Windows (XP-Win10, 32bit and 64bit)” and only requires some (any) version of Java to function. Aside from sidestepping email provider detections, the kit is built to evade Windows Defender and bypass UAC out of the box. SentinelOne customers can rest assured that the SentinelOne agent detects and effectively blocks the “Corona Virus Map Phish” kit, as demonstrated in the video below.


