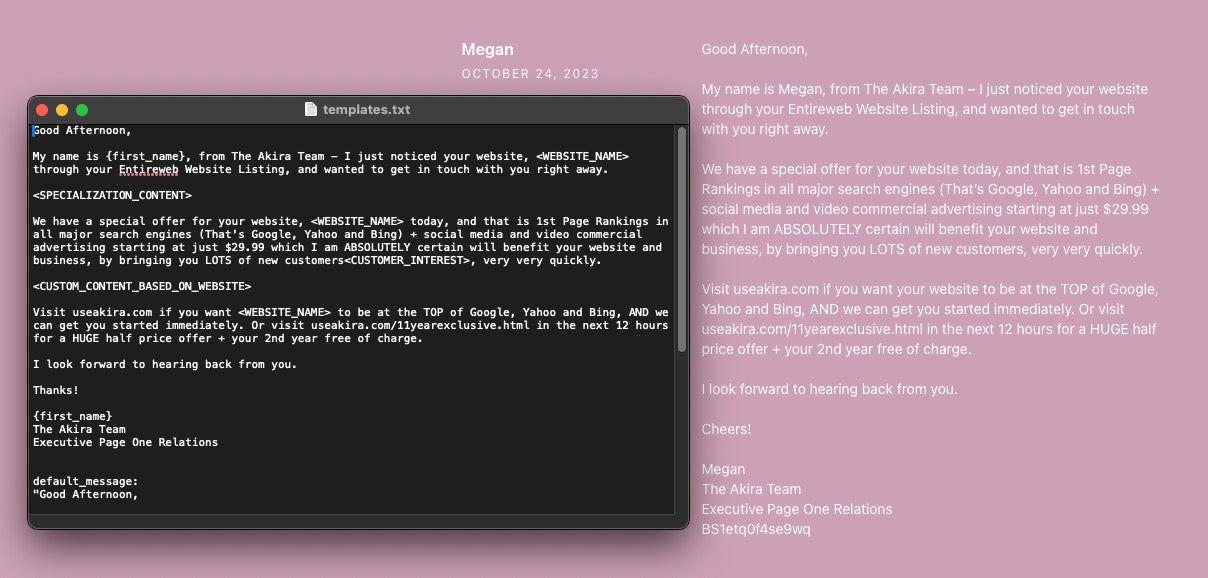
The Good | Police Detain Five SmokeLoader Malware Customers in New Phase of Operation Endgame
Law enforcement is intensifying its efforts to target the customers behind major malware loaders like IcedID, Bumblebee, Pikabot, TrickBot, SystemBC, and SmokeLoader – all of which were dismantled last year as part of Operation Endgame. This week, Europol confirmed that authorities have now detained at least five individuals linked to the SmokeLoader botnet, operated by a cybercriminal using the alias “Superstar”.

Investigations revealed that Superstar provided SmokeLoader as a pay-per-install service, allowing clients to gain unauthorized access to infected machines so they could deploy ransomware, perform keylogging and cryptomining, and access webcams. One seized customer database helped investigators identify and locate these clients, eventually linking online aliases to real-world identities.
Europol reported that customers faced various legal consequences, including arrests, house searches, and interrogations. Several customers were reselling SmokeLoader services at a markup, further complicating the criminal web and broadening the investigation’s scope. Authorities from across the U.S., Canada, Czech Republic, Denmark, France, Germany, and the Netherlands have all been involved in this coordinated crackdown.
As investigations continue, Europol has launched a dedicated website to share updates and encourage tips from the public. They’ve also released a new series of videos illustrating their ongoing efforts to track down suspects, affiliates, and customers.
This follow-up to Operation Endgame is crucial because it cracks down on not only the supply chain of malware but also the demand side of criminal operations. Holding users of these services accountable sends a strong message that anonymity won’t protect perpetrators and that law enforcement is committed to long-term disruption of cybercrime ecosystems.
The Bad | AI-Powered AkiraBot Spams SMB Websites At Scale & Bypasses CAPTCHAs
SentinelLABS has uncovered AkiraBot, an AI-powered, Python-based framework that’s been used to spam over 400,000 websites since September 2024. Of these, at least 80,000 have been successfully spammed via contact forms, comment sections, and chat widgets – primarily on small to medium-sized business websites.
Initially operating under the name “Shopbot” (likely referencing Shopify), AkiraBot has since expanded its reach to popular platforms like Wix, Squarespace, and Reamaze. Currently, it features a graphical interface so users can select their target websites and customize the scale of their spam campaigns.
AkiraBot uses OpenAI’s GPT-4o-mini model to generate specially-tailored spam messages, usually promoting questionable SEO services such as Akira or ServicewrapGO. Not only does the bot craft outreach content by analyzing the purpose and structure of each website it’s targeting, it also bypasses spam filters by creating tailored spam content each time.
AkiraBot is also capable of defeating CAPTCHA services like hCAPTCHA, reCAPTCHA, and Cloudflare Turnstile. Logs of its spam activities are recorded in a file called submissions.csv, while performance metrics – including CAPTCHA bypass success – are shared via a Telegram channel. OpenAI has since revoked the threat actors’ API key and associated assets.
AkiraBot is the most recent example of how artificial intelligence (AI) can be weaponized and abused to automate and scale spam attacks. There is a rising and urgent need for improved defenses as adversaries increasingly exploit large language models (LLMs) in their cybercrime operations. SentinelLABS emphasizes that the bot’s sophisticated bypass techniques show a high level of motivation and effort from its creators, and it’s likely that the campaign will continue to evolve. An extended list of indicators of compromise can be found here.
The Ugly | Russia-Linked Gamaredon Uses Infected Drives to Target Western Military Missions in Ukraine
An attack campaign that began in February has been targeting a Western military mission in Ukraine, employing removable drives as an initial infection vector and using malicious .LNK shortcut files to deliver a PowerShell-based version of the GammaSteel infostealer.
Shuckworm has intensified its cyberattacks on a foreign military mission in Ukraine, employing an updated GammaSteel tool for data exfiltration, with operations beginning in February 2025 and utilizing various obfuscation techniques. #CyberSecurity #Ukra… https://t.co/XdDsHuf6Mh
— Cyber_OSINT (@Cyber_O51NT) April 10, 2025
Attributed to GRU-backed hacking outfit Gamaredon (aka Shuckworm), the infection chain starts by adding a new registry value under UserAssist, indicating the attack likely originated from a USB drive. It then runs two heavily obfuscated files: one responsible for handling command and control (C2) communications via legitimate services like Cloudflare, Teletype, and Telegram, while another spreads the malware to network and removable drives using .LNK files, hiding folders and system files in the process.
Once a foothold is established, Gamaredon deploys a reconnaissance PowerShell script to capture screenshots, list out antivirus software, gather system information, and enumerate files and processes. It then uses GammaSteel to steal sensitive documents such as .doc, .pdf, .xls, and .txt files from common user directories.
Exfiltration is handled through PowerShell web requests, with a fallback to cURL over Tor to transfer stolen data should the exfiltration fail. Finally, the attackers achieve persistence by adding a key to the Windows Registry under HKCU\Software\Microsoft\Windows\CurrentVersion\Run.
While Gamaredon is considered less technically advanced than other Russian actors, researchers note that its notable use of obfuscation, legitimate services, and incremental improvements reflects a deliberate push for both stealth and persistence. The campaign confirms the group’s ongoing espionage efforts and its continued focus on Ukraine, while spreading risks to Western networks in the region.


