Threat Hunters Power Up with Conversational AI
This was the week that was RSAC 2023, so good news abounded aplenty as vendors across the cybersecurity space made announcements and reveals about new features, services and products designed to help defenders keep their enterprises safe.
Among these, SentinelOne’s Purple AI is set to be a gamechanger as it brings LLM-powered conversational AI to the Singularity platform, allowing threat hunters to replace complex, structured query language with simple questions, from the specific to the vague. “Am I infected with SmoothOperator?”, “Which endpoints are exposed to Log4J?”, “What are the most suspicious events in my environment in the last 24 hours?”.
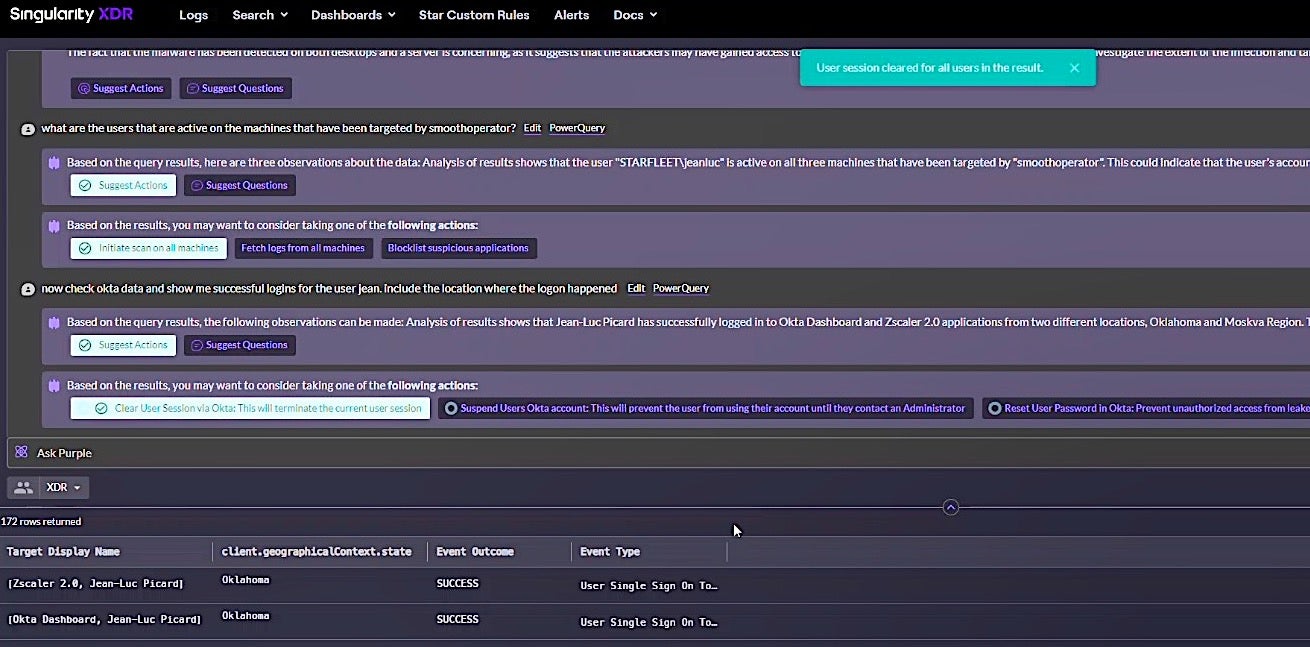
The AI returns results along with identified behavior and recommendations for further action. Coupled with XDR to unite a business’ diverse data sources, the AI can help threat hunting teams to overcome the major challenges of threat hunting: time and skill-level. With many SOC teams struggling with alert fatigue and a skills shortage, PurpleAI will provide a much needed tonic for the troops.
RSAC 2023 also saw SentinelOne announce an exclusive partnership with CNAP specialists Wiz. Combining SentinelOne’s Cloud Workload Protection with Wiz’s Cloud Native Application Platform is expected to bring huge benefits to enterprise customers needing to manage and secure cloud infrastructure. For more on what happened at RSAC this week, see our dedicated posts on Days 1, 2, 3 and 4.
PaperCut Vulnerability Leveraged to Deliver Ransomware
PaperCut servers with known vulnerabilities CVE-2023-27350 and CVE-2023-27351 are being exploited to deliver Cl0p and LockBit ransomware, it was discovered this week. The print management software is widely used in enterprises to monitor and control printing tasks.
The vulnerabilities may have been weaponized as early as April 13, five days prior to the first reported suspicious activity linked to exploitation of unpatched PaperCut servers. The vulnerabilities in PaperCut NG and MF products expose the servers to unauthenticated remote code execution attacks and can also allow unauthorized attackers to steal credentials and PII.

In one in the wild case, attackers compromised a target with PowerShell scripts to deliver LockBit ransomware. Meanwhile, Microsoft reported that a Cl0p-affiliated ransomware gang was conducting multi-stage attacks on vulnerable PaperCut servers that begin with PowerShell delivering a TrueBot payload and then use Cobalt Strike for lateral movement and data exfiltration.
Needless to say, organizations deploying PaperCut are urged to ensure that all instances are updated as a matter of urgency.
RTM Locker Ransomware Targets Virtual Machine Servers
Recent weeks have seen a number of examples of how threat actors continue to explore new opportunities for compromise and seek new targets to exploit. In this regard, we’ve seen LockBit experimenting with macOS ransomware, and an increase in payloads targeting Linux, which of course is widely used in servers as well as devices common in the enterprise, from routers and printers to IoT ‘smart’ appliances and security cameras.
The latest development is a variant of the RTM Locker ransomware that specifically targets Linux, NAS and, significantly, virtual machines on VMware ESXi hosts. ESXi servers have become increasingly popular with the rise of cloud computing and cloud infrastructure as a means to deploy and manage enterprise level virtual computers, making them attractive targets for threat actors.
The new variant of RTM Locker is said to be based on leaked Babuk ransomware source code. On execution, it kills all running VM clients on the ESXi host and begins encrypting files. Locked files are appended with a .RTM extension and a ransom note entitled !!!Warning!!! is dropped on the compromised server. The ransomware uses asymmetric encryption, meaning decryption is only possible with possession of the private key held by an attacker.
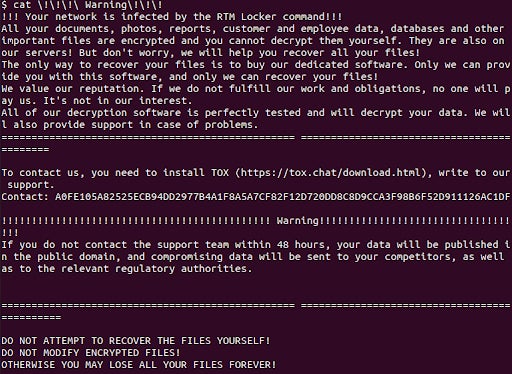
The hardcoded ransomware note shows that the victims need to install the encrypted chat client Tox in order to negotiate payment of the ransom. Exactly how active the RTM group is at the moment is open to debate, but the developers have been seen advertising for affiliates in darknet forums with translations available in English, Russian and Chinese languages.


