The Good | AI Is Helping Level the Playing Field Against Advanced Cyber Threats
Artificial intelligence (AI) is helping security teams detect and detain sophisticated intrusions in real time, even across siloed or sprawling digital environments. While advanced persistent threat (APT) groups continue to pose a serious risk to organizations, experts are pointing to a bright spot: cyber defenders are getting faster, smarter, and more capable by harnessing the power of AI.
“Your ability to respond quickly is really important,” said Alex Stamos, CISO at SentinelOne. According to Stamos, most companies struggle with fragmented visibility across their cloud and on-premise systems, leaving gaps and blind spots that attackers can exploit. “Very few companies have visibility across their cloud infrastructure and their on-premise tech in a way where they see all of it at the same time,” he explained.
Using AI allows organizations to efficiently bridge that gap by correlating activity across multiple environments and flagging anomalies, such as unusual login behavior or credential misuse, that would be nearly impossible to spot manually. Stamos emphasizes that AI’s true power comes from centralized telemetry. “You need to gather as much security telemetry as possible and have it in one data lake that can be queried quickly in real time.”
AI-powered tools can rapidly sift through massive amounts of telemetry to detect lateral movement or chained vulnerabilities – all common tactics among APT and ransomware groups. While only a few hundred large organizations currently operate at this level, Stamos says the blueprint is clear: Unify telemetry, query in real time, and scale up defensive capabilities using AI. Although cyber threats continue to develop, AI is paving the way for security defenders to match the speed and scale of even the most well-funded or complex threat actors today.
Learn about SentinelOne’s advanced AI security analyst here.
The Bad | Russia-Linked Actors Exploit Microsoft OAuth to Target Ukrainian Allies
Non-government organizations (NGOs) and key individuals connected to Ukraine and human rights efforts are actively being targeted by Russia-linked threat actors. In these attacks, security researchers note that actors are compromising Microsoft 365 accounts through a new tactic that abuses Microsoft’s OAuth 2.0 Authentication workflows.
Since March 2025, groups tracked as UTA0352 and UTA0355 have impersonated European officials or Ukrainian diplomats, contacting targets via Signal and WhatsApp. The attackers were observed inviting victims to supposed private video meetings before sharing OAuth phishing URLs disguised as meeting links. In the most recent attacks, communications even originated from compromised Ukrainian government accounts.
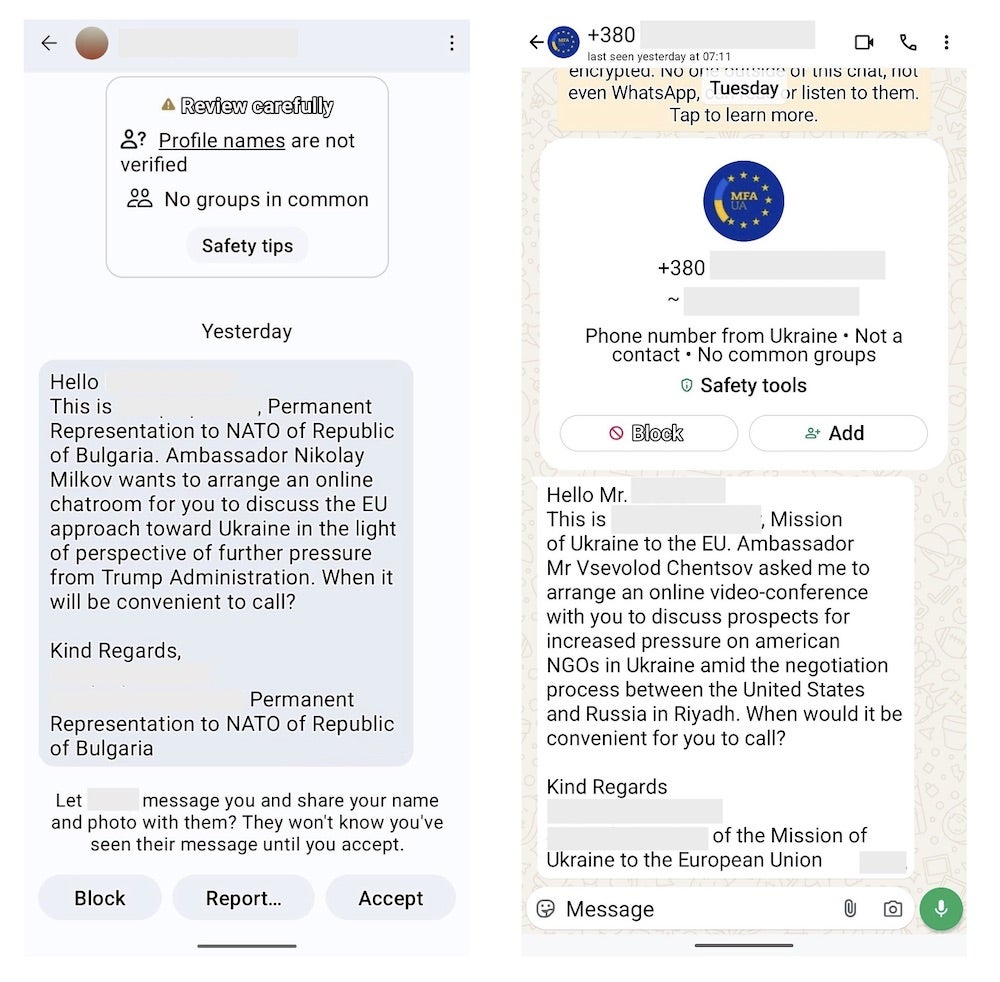
These phishing URLs redirect to legitimate Microsoft login portals, and upon authentication, users are sent to an in-browser version of Visual Studio Code (insiders.vscode[.]dev) where Microsoft OAuth codes are displayed. Victims are lured into sharing the codes, believing it’s necessary to join the meeting. It is these authorization codes, valid for 60 days, that grant attackers access to the target’s Microsoft 365 resources.
In a related campaign, UTA0355 uses the OAuth code to register a new device to the victim’s Microsoft Entra ID (formerly Azure AD). Attackers then trick users into approving two-factor authentication requests, which allows email access and persistent account compromise. All activity is routed through geo-matched proxy networks, complicating detection. Making these attacks even more difficult to block is that no attacker-controlled infrastructure is used – only legitimate Microsoft services.
To defend against such threats, researchers remind admins to closely monitor logins tied to Visual Studio Code’s client_id in order to block access to insiders.vscode.dev. Organizations can also implement conditional access controls to restrict logins to managed devices only.
The Ugly | Cybercrime Losses Soar to $16.6 Billion in 2024, FBI Reports
The FBI’s Internet Crime Complaint Center (IC3) has clocked the amount of cybercrime losses at a whopping $16.6 billion in 2024 – 33% up from last year. In their latest report, the FBI documented nearly 860,000 complaints with 256,256 involving financial losses, averaging out to $19,372 per case.
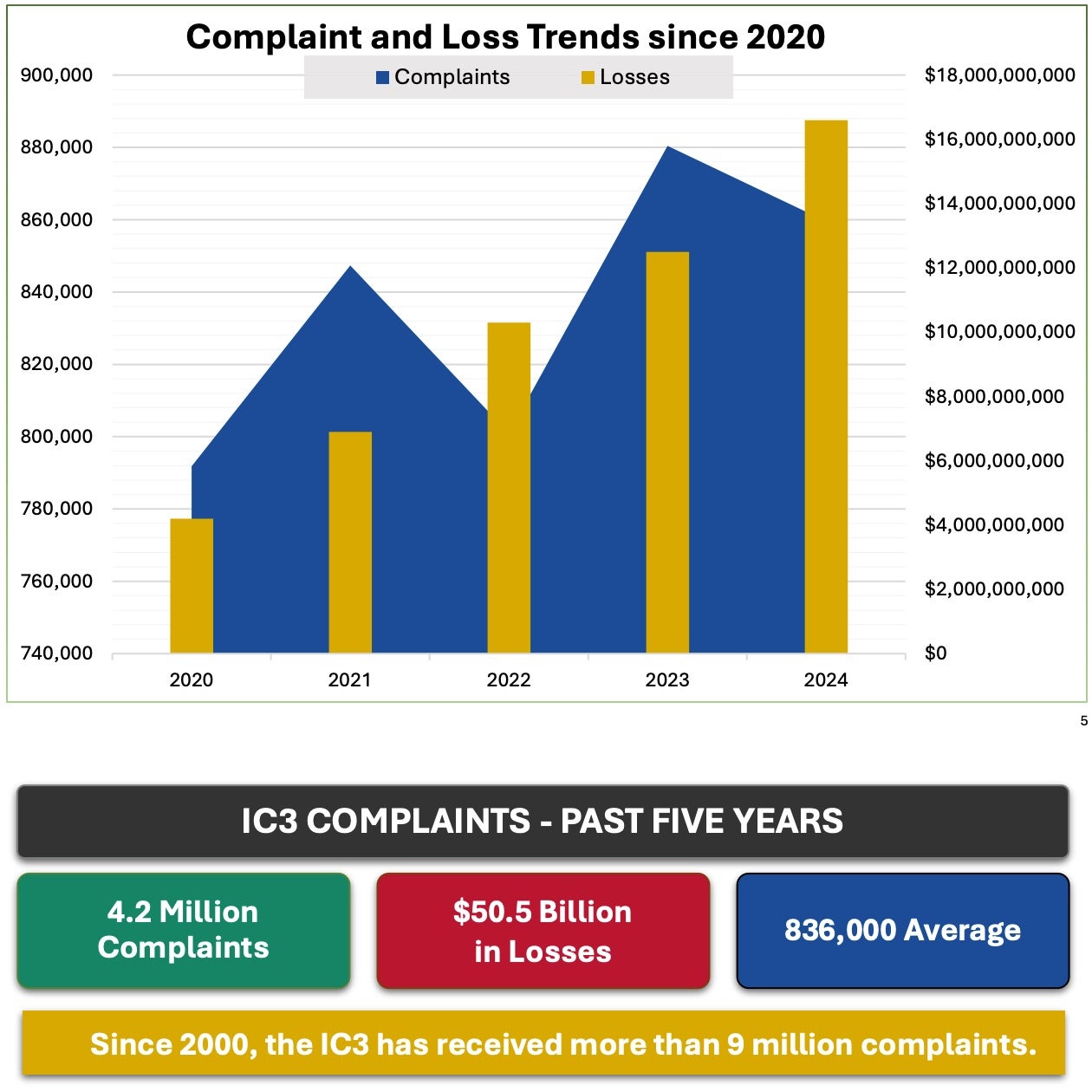
Overall, cyber-based fraud accounted for almost 83% of all total damages, which calls to attention how effective social engineering techniques, like phishing and extortion, continue to be. These two techniques together represented 280,000 complaints.
Despite only documenting 3,156 ransomware complaints, ransomware attacks were identified as the most pervasive threat to critical infrastructure, rising 9% year-over-year. Top ransomware groups included Akira, LockBit, RansomHub, Fog, and Play. Reported ransomware losses reached $12.5 million, excluding collateral damage such as business downtime or costs associated with recovering critical data.
Data breaches were also called out as a major threat, with 263,455 complaints and nearly $1.7 billion in losses – second only to phishing. In particular, IC3 noted a surge in incidents targeting enterprises, especially those within the critical infrastructure industries.
While the numbers keep skyrocketing, the FBI does caution that these reports likely underrepresent the true scale of cybercrime, as many victims don’t report incidents. The agency urges individuals and organizations to file complaints to help build an international database of active threat actors for more accurate tracking.
As the threat landscape shifts and evolves, organizations need to keep up a proactive approach to security, leaning on ‘assume breach’ strategies and performing regular testing of their security controls and policies.


