The Good
Browsers are the means by which almost all of us interact with the internet and are one of the few applications on any device that a user is almost guaranteed to use. Given their central role in our digital lives, anything that improves browser security is more than good news. This week saw two major browsers roll out updates with added security features.
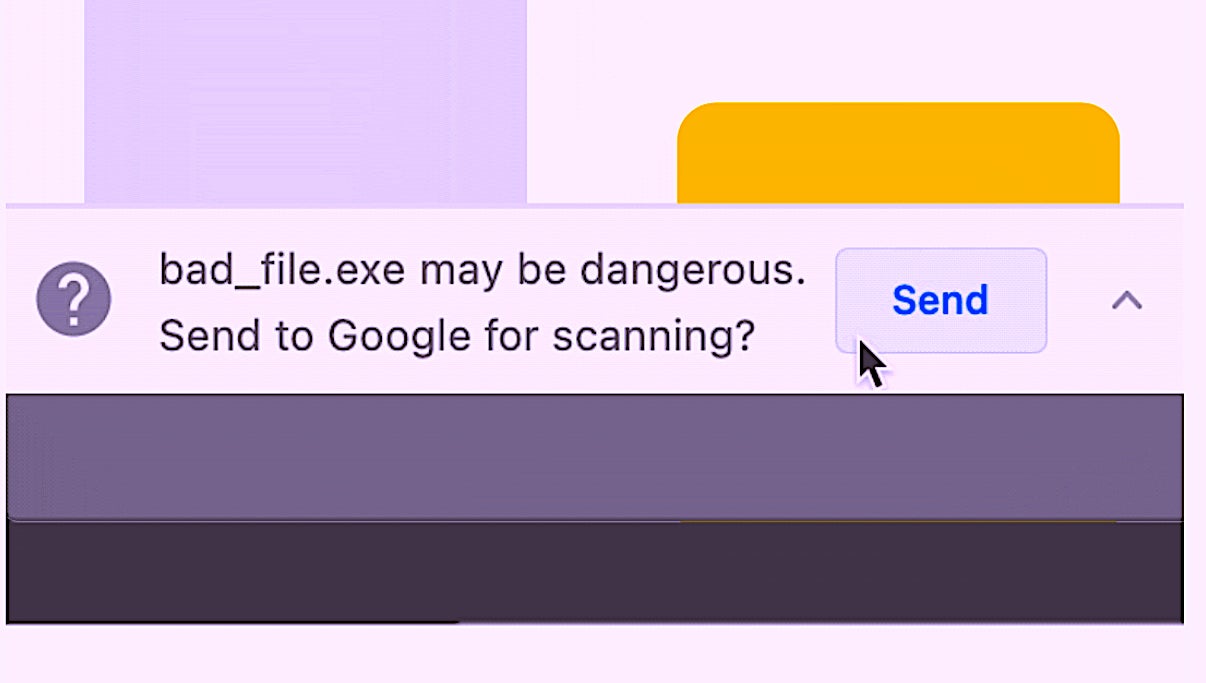
Google’s Chrome browser is being given a new download protection feature that not only allows it to scan files for malware but to send the file to Google to be scanned for deeper analysis in real time. On top of that, Chrome 91’s Enhanced Safe Browsing feature offers additional protection when installing extensions from the Chrome Web store, a known vector for all sorts of adware and other malicious software. New developers will also not be given automatic trust by Enhanced Safe Browsing either, preventing malware authors circumventing detections just by spinning up a new developer identity.
This week also saw the release of Firefox 89. While the new ‘Proton’ UI was the headline news, it may have slipped under the radar that the new version extends protection against cross-site cookie tracking to Private Browsing windows by default. Mozilla claims that “Firefox’s Private Browsing windows have the most advanced privacy protections of any major browser’s private browsing mode.” Good to know.
The Bad
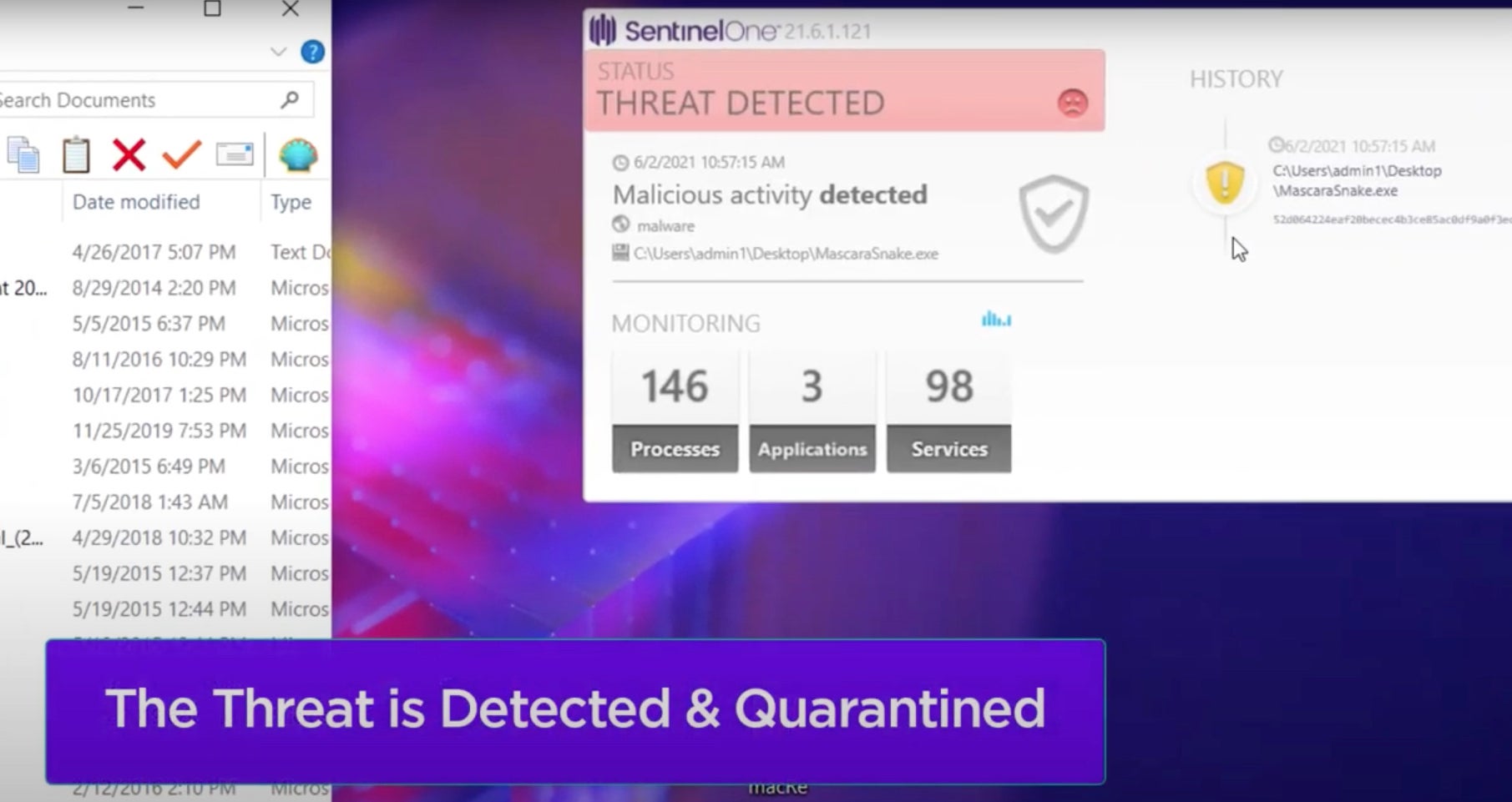
This week’s raft of ransomware attacks includes incidents affecting the Steamship Authority of Massachusetts, FujiFilm, and JBS. While details of the first two are still incoming, according to the FBI, the REvil ransomware family is behind the recent attack on JBS. “We have attributed the JBS attack to REvil and Sodinokibi and are working diligently to bring the threat actors to justice”, the Bureau tweeted on Thursday.
The ransomware attack affected operations in North America and Australia, igniting fears of product shortages and price increases. The REvil ransomware group has been in operation (in current form) since mid 2019. Their ransomware is distributed via multiple methods including Exploit Kits, exploitation, and partnerships with other malware ‘frameworks’. SentinelOne customers have been protected from REvil since the onset of their activity.
SentinelLabs’ senior threat researcher Jim Walter noted that REvil were something of a ‘pioneer’ in the modern ransomware threatscape, “being one of the early adopters of publicly blogging victims and leaning heavily into the ‘double-extortion’ side of things.” Copied by many ransomware operators that followed, Walter said that the actors behind REvil were “early experimenters with auctioning off stolen data. Some auctions were successful, some were not, but potentially data stolen from select victims would have been available to the highest bidder.”
The Ugly
If there’s anyone still out there that doesn’t understand that computer crime is now such big business that it is effectively run in the same way as legitimate businesses, this week’s latest news from the criminal underground should serve to ram home the point.
In a bid to boost knowledge on ways to steal private keys and cryptocurrency wallets, members of a cybercrime forum are being offered over $100,000 in prize money in a competition calling for research papers on cryptocurrency-related topics.
Among the papers submitted were entries showing how to create a phishing website to harvest cryptocurrency wallet keys and seed phrases and how to manipulate cryptocurrency services’ APIs to steal private keys. Incentivising innovation through cash prizes not only shows how developed cybercrime is as an industry but also just how much stolen cash is floating around for investment in further crime.
So, you think you can tell what counts as a computer crime? In other controversial news this week, the U.S. Supreme Court has overturned a lower court’s verdict concerning the meaning and scope of the Computer Fraud and Abuse Act (CFAA). The decision limits the scope of the Act and essentially does not consider it a crime under the CFAA if, for example, a malicious insider abuses their own credentials to steal corporate IP (they may, of course, be guilty of committing offenses under other statutes in so doing).
This is not necessarily a bad thing: the new ruling would not have resulted in convictions such as that handed down to internet activist and campaigner Aaron Swartz, for example, and allays concerns of government overreach in using the CFAA to criminalize trivial computer misuses. However, the decision will undoubtedly prove contentious and could see a re-write of the CFAA as a result.