The Good
The European Union Agency for Law Enforcement Cooperation (Europol) has successfully shut down one of the fastest-spreading mobile malware strains in today’s cyber landscape.
According to a statement from Europol, the European Cybercrime Centre (EC3) coordinated with 11 law enforcement agencies around the world to respond to a global campaign involving FluBot, an Android-based malware that was first sighted in December 2020.
🚨 Takedown of SMS-based FluBot spyware 🚨
🔹 International law enforcement operation involving 11 countries 🌍🚔
🔹 Fastest-spreading mobile malware to date ⏩📱
🔹 The Android malware has now been rendered inactive ✋🛑More ➡️ https://t.co/YcMC5XRS6o pic.twitter.com/ksPuSHk6aW
— Europol (@Europol) June 1, 2022
The FluBot malware spreads through SMS, masquerading as package tracking or voicemail notifications. When an Android user clicks the link in these text messages, they’re prompted to install FluBot, which is disguised as another application.
Once installed, the FluBot app will ask for accessibility permissions, which are used to disable a phone’s security and exfiltrate credentials for the user’s banking accounts and cryptocurrency wallets. The malware then spreads even further by accessing an infected device’s contact list and sending malicious messages to each entry.
After its initial sighting in 2020, FluBot quickly spread through a large number of devices in Spain and Finland. As the malware spread through Europe and Australia, Europol brought in law enforcement agencies from multiple impacted nations (Australia, Belgium, Finland, Hungary, Ireland, the Netherlands, Spain, Sweden, Switzerland, and the United States) to create a joint strategy and offer digital forensic support.
Earlier in May, the Dutch police completed the final takedown and took control of FluBot’s infrastructure, making the malware strain inactive.
Although Europol is still looking for the threat actors behind the campaign, operations like these show that an international infrastructure to proactively respond to malware is still coming together. Concerned users can follow Europol’s guidance on identifying and resetting phones infected with FluBot here.
The Bad
This week, cyber criminals wiped hundreds of unsecured Elasticsearch databases and sent ransom notes to admins demanding 0.012 Bitcoin in exchange for their data.
According to a report, the threat actors responsible have already wiped over 450 indexes, and analysts have identified over 1,200 Elasticsearch databases containing the ransom note.
The attackers use an automated script to handle most of the work, including parsing vulnerable databases, deleting the indexes and dropping a ransom note.
In the ransom note, the attackers demand approximately $620 worth of Bitcoin within seven days. If the initial deadline isn’t met, victims have an additional week to submit a payment before the attackers permanently delete their data.
Although the individual ransoms are only around $620, all 450 ransom payments totals up to almost $280,000. However, at the time of publication, the Bitcoin wallets in the ransom note appear to be empty.
Analysts believe that even if victims paid the ransom, it’s unlikely they would be able to recover their databases. Although an attacker could have exfiltrated the data, researchers pointed out that storing this data would be “prohibitively expensive.”
To mitigate the risk of falling victim to one of these attacks, security experts emphasize that like other cloud resources, Elasticsearch databases should not be Internet-facing unless it’s necessary for day-to-day operations. Enforcing multi-factor authentication (MFA) and adopting strong cloud security measures are also essential.
While these attacks aren’t unique, such widespread campaigns also provide an alarming reminder that organizations should review their cloud security policies to ensure they’re properly protected.
The Ugly
Security researchers have identified and are working to quickly respond to a critical zero-day vulnerability in Microsoft Windows’ Support Diagnostic Tool (ms-msdt), tracked as CVE-2022-30190 and dubbed “Follina”.
Follina allows threat actors to execute arbitrary code on a vulnerable machine by calling the tool’s ms-msdt protocol, and impacts all Windows versions currently supported by Microsoft.
While the most commonly observed approaches abuse Microsoft .doc and .rtf files to call the ms-msdt protocol and execute malicious code, other execution methods such as using WGET are continuing to emerge as the zero-day gains traction.
In recent weeks, researchers identified the first public sample of a malicious Word document designed to abuse this vulnerability, and observed both a Belarus-based threat actor exploiting the flaw through Word’s ability to load HTML to execute PowerShell code, and a Chinese APT using a C2 domain (tibet-gov.web[.]app) to execute their code.
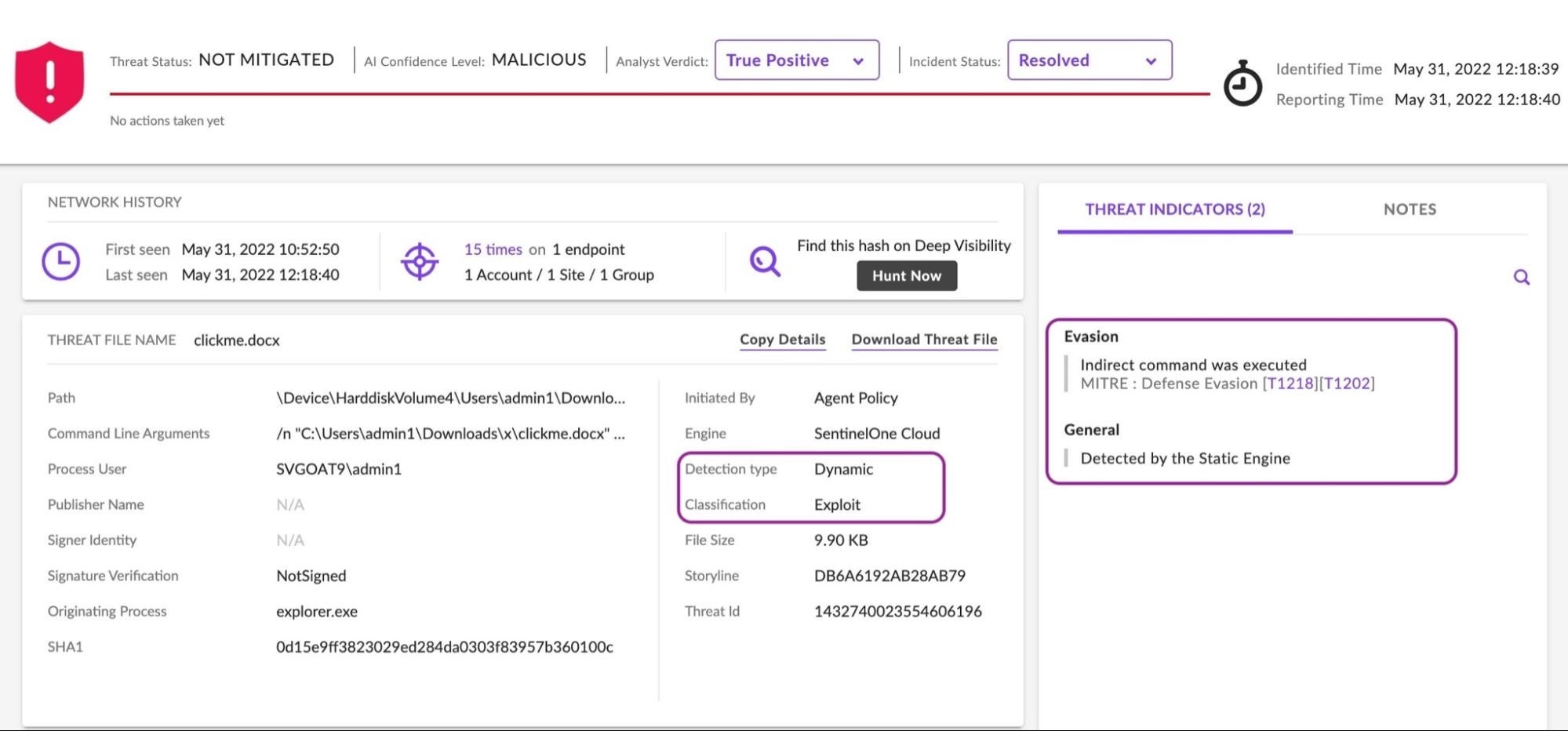
Follina has the potential to impact unprepared organizations in a not dissimilar way to the recent log4j vulnerability. As in that case, security teams are strongly advised to be proactive and to determine the risk and take appropriate mitigation steps without delay.



