The Good
Big technology companies have been the source of many privacy scandals. Some have been accused of disregarding their users’ rights and peddling the immense information they gather about their users’ (us) activities and whereabouts. This week, however, the two largest tech giants that control the phones in our pockets have both announced new features that should improve user privacy safeguards.
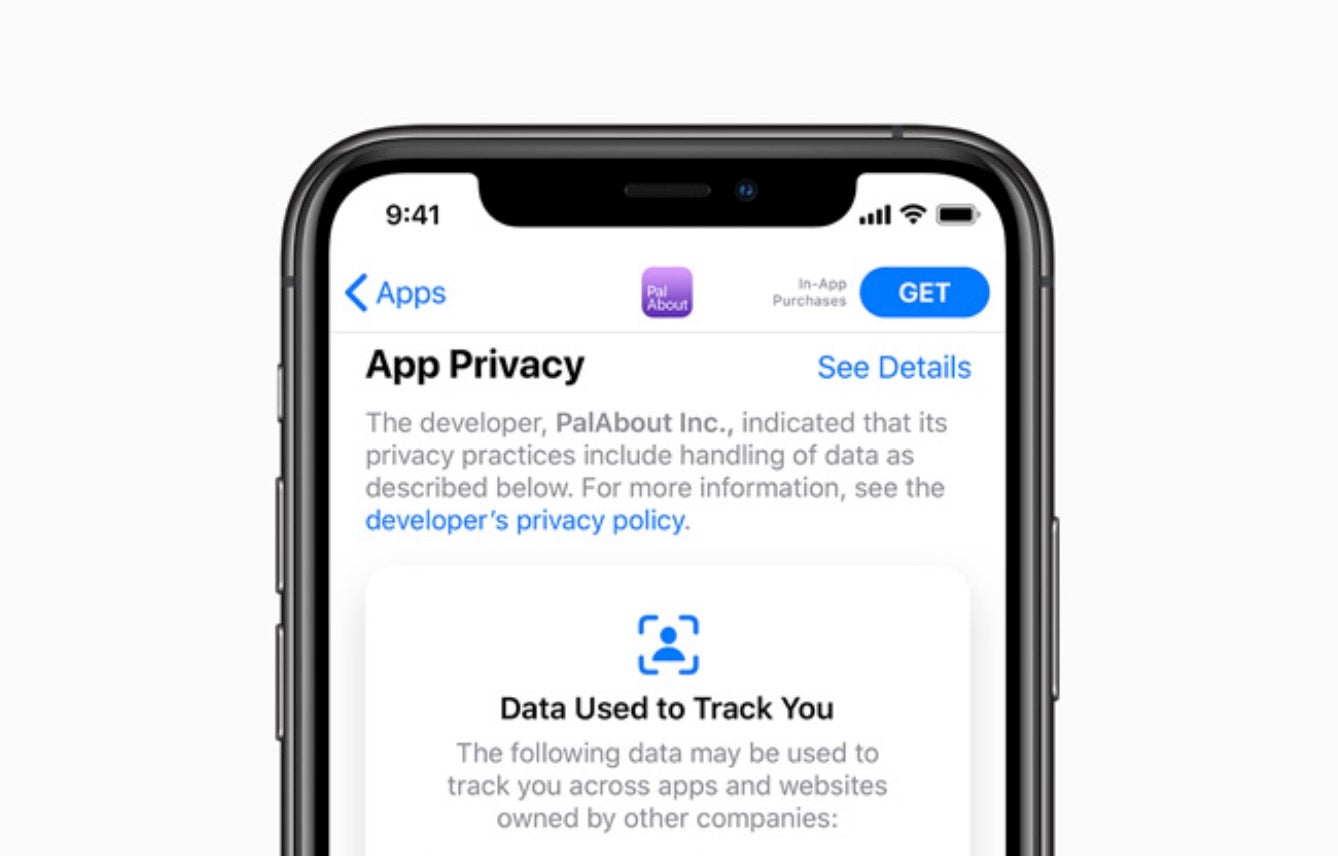
First up, Apple announced new privacy features for its devices at its annual Worldwide Developers Conference. One important new feature coming to iOS 14 displays an orange dot indicator on the status bar whenever the iPhone’s camera or microphone is turned on. iOS 14 will also limit the location information shared with apps, making it possible to only share your approximate location with certain apps rather than your precise location. Apple also introduced a new privacy labeling system, resembling those in food products. Erik Neuenschwander, Apple’s user privacy manager said:
Labels will indicate app permissions to inform people how much data an app requests before they download them in two categories: “Data Linked To You” and “Data Used to Track You.” Apple also updated user tracking on iOS 14, meaning that only users who give explicit permission to an app can be shown targeted ads, share location data with advertisers, share advertising ID or any other identifiers with third parties
Meanwhile, Google followed up with its own privacy update. Google CEO, Sundar Pichai, announced that new Google accounts will auto-delete activity and location every 18 months by default. YouTube history will also auto-delete every 36 months. This will not affect existing accounts, which will still need to proactively turn on the “Auto-delete” feature. Google is also introducing “Incognito Mode” in its Search, Maps, and YouTube mobile apps. In addition, the company is updating its Security Checkup feature to include a Password Checkup mechanism. This will allow users a “one stop shop” for reviewing and improving their security and privacy settings, and ensure their passwords have not been previously exposed in a data breach.
The Bad
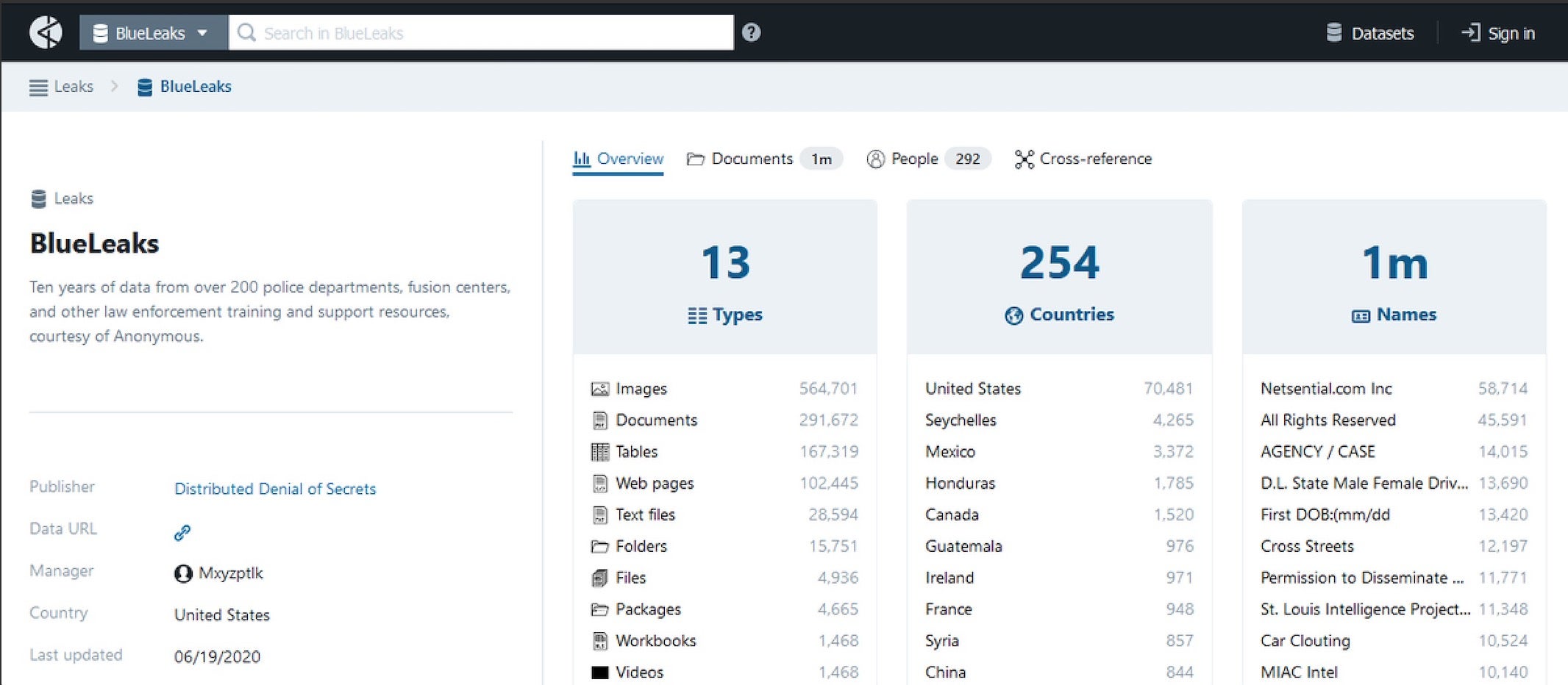
The recent political and cultural turmoil in the US has already caused several cyber incidents involving DDoS attacks and social media harassments. But these were rather small scale and benign in nature, until a mega-breach occurred this week involving a million files containing 269-gigabytes worth of police data, including emails, audio, video, and intelligence documents.
The data was obtained and leaked by information-freedom activists known as “Distributed Denial of Secrets”, or DDoSecrets. Sources suggest it was stolen from a web development firm called Netsential. The data trove was then published on a dedicated, searchable portal dubbed “Blueleaks”. The breach contains data from more than 200 state, local, and federal agencies, including intelligence fusion centers. Although the DDoSecrets group said it tried to remove sensitive information prior to publishing, it still contains such information as bank account routing numbers, personally identifiable information, images of criminal suspects and details about law enforcement officers.
Such a massive data breach and subsequent exposure is not just an embarrassment to law enforcement agencies, eroding the already shaken confidence of the public in them. It could potentially also help to single out and target specific members of law enforcement agencies and their families, both online and in the real world.
The Ugly
Data breaches are bad, no question, but when these breaches expose the details of victims of abuse, it becomes seriously ugly. Security and Privacy researchers Noam Rotem and Ran Locar recently discovered a data breach originating from the domestic violence prevention app called “Aspire News App”, operated by a non-profit founded by American TV personalities Robin McGraw and her husband “Dr. Phil” McGraw.
This app, “Aspire News”, can be installed on a user’s phone, where it appears to be yet another news app. However, it also features an emergency help section with resources for domestic abuse victims, a “panic button” to allow them to send an emergency distress message to a trusted contact. These messages can be sent via voice recording and include the victim’s details, home address, the nature of their emergency, and their current location. This is a clever way to allow victims to report abuse and call for help.
Unfortunately, these voice messages were stored on a misconfigured Amazon Web Services (AWS) S3 bucket, allowing them to be viewed and downloaded by external parties. This extremely sensitive data includes:
- Victims’ full names and home addresses
- Details of their emergencies and/or personal circumstances
- Abusers’ names and personal details
While the organization behind Aspire News App secured the misconfigured repository within 24 hours of being contacted by the researchers, this isn’t the first time misconfigured AWS buckets have been the difference between good intentions and serious privacy breaches. Given the media exposure and high public profile that comes with critical data breaches, it’s concerning that here we are midway through 2020 and we still need to reinforce this message: data security is serious business, folks!