The Good
Remember Gozi? Well, you’d be forgiven if you’d forgotten, but this particular piece of banking malware was rife around the turn of the decade, causing trouble in at least eight countries, including the US, the UK and several European nations. While the world of cyber security may have moved on, law enforcement didn’t forget. Back in 2016, the cops caught up with two of the malware as a service (MaaS) authors and this week, they nabbed a third.
On Tuesday, it was reported that Mihai Ionut Paunescu was arrested in Bogota, Colombia on charges relating to designing hosting systems that were used to share Gozi files with affiliates without being detected. Paunescu and pals allegedly charged criminals $500/week for use of their malware, which was used to steal bank account passwords and subsequently millions of dollars from victims. It’s not the first time Paunescu has been caught. In 2012, the Romanian national was arrested in his own country but escaped extradition. He’s unlikely to be so lucky this time around.
Meanwhile, more bad news for crims this week as Europol cyber cops took down DoubleVPN. The so-called ‘super secure’ service was a favorite on Russian and English-speaking cybercrime forums, where it was heavily recommended for those seeking to hide their identity and location while undertaking ransomware, phishing and other malicious activities.

Before it was taken down, the DoubleVPN website claimed that it kept no customer logs. However, according to the notice posted by authorities on the now seized site, the cops grabbed personal information and logs relating to all DoubleVPN customers. “DoubleVPN’s owners failed to provide the services they promised”, the notice ominously stated.
The Bad
APT28, aka the 85th GTsSS of the GRU, is rarely out of the news for long, and it’s an adversary we’re well used to dealing with. This week, the NSA, FBI and other U.S cybersecurity agencies revealed that the Russian military intelligence unit has been making a beeline for enterprise cloud environments since at least mid-2019.
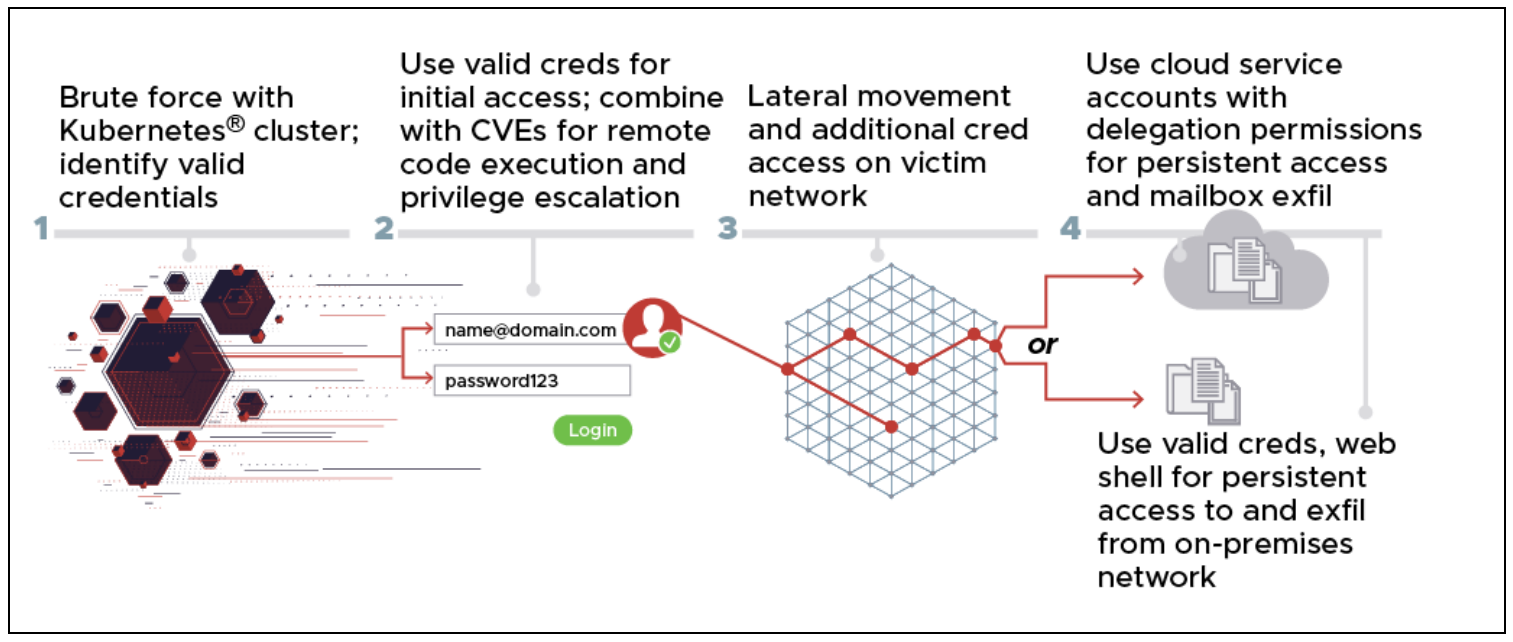
According to the advisory, the threat actor used a Kubernetes cluster as a springboard for attacking hundreds of private and public sector targets worldwide. Much of their activity took the form of anonymized brute force and password spraying attacks against organizations using Microsoft Office 365 cloud services, combined with exploiting known CVEs such as CVE 2020-0688 and CVE 2020-17144.
The attacks originating from the Kubernetes cluster were primarily routed through TOR and commercial VPN services, although the advisory notes that some were delivered directly from nodes in the cluster. Targets included government and military organizations, political organizations, energy companies, logistics companies as well as law firms, media and higher education institutions.
Authorities warn that the campaign is almost certainly ongoing. Organizations are urged to adopt and expand the use of MFA and ensure that access controls have time-out and lock-out features, use strong passwords and a Zero Trust security model. More information on specific TTPs and IoCs are available here.
The Ugly
Question: what do you get when you add a zero-day to a freshly minted exploit and the accidental release of both by security researchers? Answer: a very ugly day in cybersecurity. What is now being dubbed PrintNightmare is a remote code execution vulnerability in the Windows Print Spooler service. The service is enabled by default on Windows Server editions, with the exception of Windows Server Core, and is likely to affect the majority of enterprises.
Most importantly, the bug is not fixed in the latest Microsoft patch and CISA advises all enterprises to disable the Windows Print Spooler service in Domain controllers, Active Directory admin systems, and all other systems that do not print.* This can be effected with PowerShell via
Stop-Service -Name Spooler -Force Set-Service -Name Spooler -StartupType Disabled
Or more succinctly via Windows cmd with:
net stop spooler
On Thursday, Microsoft assigned the bug to CVE-2021-34527 and further advised admins to disable inbound remote printing through Group Policy. The OS vendor also said they were aware of in-the-wild attacks but gave no further details.
The bug came to light when Chinese cybersecurity outfit Sangfor released PoC code on Github for what they thought was a different vuln that had been included in Microsoft’s most recent Patch Tuesday. Researchers from the company intend to present at this year’s Black Hat about multiple Spooler vulns, but mistakenly released code related to a different vuln from that included in the patch. Subsequently, the PoC was removed from GitHub but not before others had cloned and forked the repo.
*Update: this story is still unfolding, and developments since we went to press suggest that disabling the Spooler may not be sufficient.