The Good | Global Crackdowns Target DPRK Fraud, Crypto Investment Rings & Russian Cybercrime Ecosystem
Raids on 29 laptop farms across 16 states have put a dent in a North Korean operation that placed IT workers using fake identities in remote jobs in over 100 U.S. companies.
Facilitated under the “DPRK RevGen: Domestic Enabler Initiative”, law enforcement agencies were able to arrest Zhenxing “Danny” Wang, and eight other actors, for a scheme that generated over $5 million for the DPRK and exposed sensitive data, including military technology. The investigation also yielded the seizure of hundreds of financial accounts, 21 fake websites, and 200 computers.
Currently, four North Korean nationals remain at large, with $5 million in rewards offered for information on their whereabouts.
Today, the FBI and @TheJusticeDept announced nationwide actions to disrupt North Korean schemes to defraud American companies through remote IT work, which included the arrest of a U.S. national who allegedly hosted a laptop farm for North Korean actors https://t.co/3IC28oaMFa pic.twitter.com/rsx0EPO0nu
— FBI (@FBI) June 30, 2025
Five other individuals were arrested in Madrid and the Canary Islands for laundering $540 million from crypto investment scams that defrauded over 5,000 victims. Supported by Europol and international partners, the operation uncovered a global network that relied on obfuscation channels throughout Asia, working to route illicit funds through cash withdrawals, bank transfers, and crypto accounts.
The U.S. Treasury’s OFAC sanctioned Russia-linked Aeza Group and its affiliates for providing bulletproof hosting (BPH) services to cybercriminals and ransomware groups.
Aeza’s infrastructure supported malware campaigns, dark web drug markets, and pro-Russian influence operations. Its members, several of whom were recently arrested, allegedly enabled global attacks on U.S. tech and defense firms. To date, Aeza has received over $350,000 in crypto tied to illicit activity.
These sanctions, coordinated with international partners, are part of a broader effort to disrupt ransomware ecosystems by targeting abuse-resistant infrastructure and its operators.
The Bad | U.S. Agencies Caution Critical Infrastructure Firms Against Iranian Cyber Threats
A new joint advisory this week from U.S. cyber agencies warns of potential cyberattacks by Iranian-affiliated threat actors on U.S. critical infrastructure.
While no active campaign has been detected so far, the agencies call for heightened vigilance given the ongoing tensions in the Middle East and past instances of cyber activity linked to Iran. In particular, organizations in the Defense Industrial Base (DIB), energy, water, and healthcare sectors were listed in the fact sheet as potential targets.

Iran-linked threat actors are known to exploit unpatched vulnerabilities and default credentials. In 2023, IRGC-affiliated actors compromised a Pennsylvania water facility by targeting Internet-exposed Unitronics programmable logic controllers (PLCs). These actors also commonly carry out DDoS attacks, website defacements, and ransomware campaigns, often against Israeli-linked entities, and have been known to collaborate with ransomware gangs like NoEscape, RansomHouse, and BlackCat.
Iran-based actors commonly start with reconnaissance tools like Shodan to locate vulnerable ICS devices, then exploit weak network segmentation to move laterally. They have also used RATs, keyloggers, PsExec, Mimikatz, and diagnostic tools to escalate access and evade detection. The advisory follows a DHS bulletin warning of potential ‘low-level’ cyberattacks by pro-Iranian hacktivists amid rising geopolitical conflicts.
CISA and partner agencies urge targeted industries to strengthen their cyber defenses by isolating operational technology (OT) and industrial control systems (ICS) from public networks, enforcing strong, unique passwords after replacing all defaults, enabling MFA, applying critical software patches, monitoring networks for abnormal activity, and establishing incident response plans with tested backup and recovery systems. For further guidance, organizations can consult CISA’s and the FBI’s webpages covering Iran-based cyber threats.
The Ugly | North Korean Threat Actors Target Web3 Firms with macOS Malware
New research from SentinelLABS reports that Web3 and crypto-related businesses are being targeted by North Korean state-sponsored threat actors. Using lures and a fake Zoom update request, the attackers deliver multiple payloads including binaries written in C++, and unusually, Nim.
Dubbed ‘NimDoor’, the attack chain begins when targets are lured via Telegram into accepting an invite to a business meeting. A malicious script is triggered by the meeting invite warning the victim that a “Zoom SDK update” is needed. Running the script kicks of the complex infection chain.
The researchers detail how NimDoor deploys two key binaries: a loader with the misspelled name GoogIe LLC (using an uppercase ‘i’ rather than lowercase ‘L’) and a trojan called CoreKitAgent. GoogIe LLC gathers system details and writes a config file that helps establish persistence through a LaunchAgent.
The trojan uses a novel signal-based persistence mechanism. Instead of writing out persistence components during its active lifecycle, CoreKitAgent waits until it is terminated by either a system reboot or the user. The malware catches signal interupts that are typically used to tell programs to clean up before termination. CoreKitAgent uses these signals to write out copies of itself, the loader and a LaunchAgent that is activated when the system restarts or the user logs in to their account.
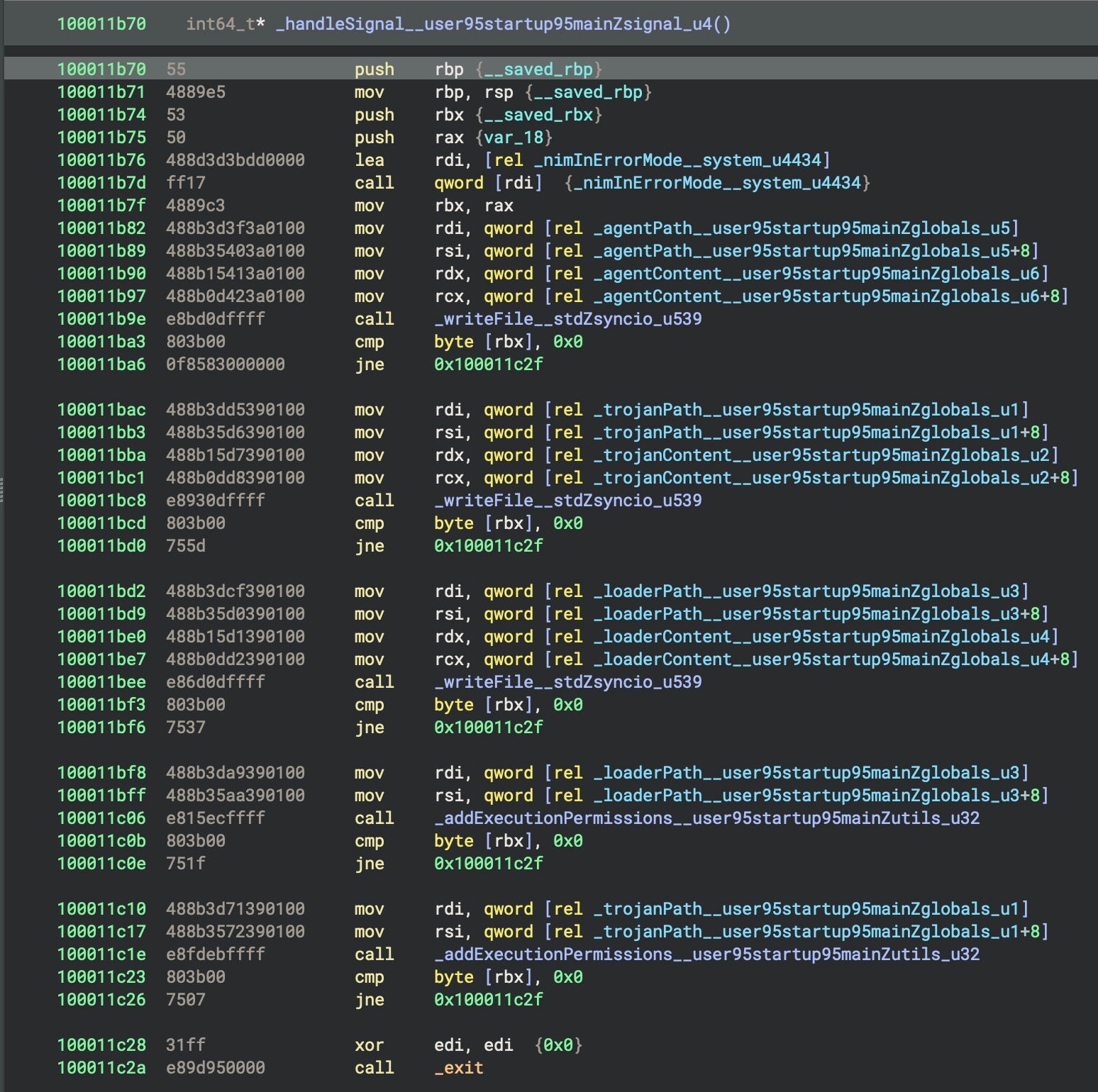
In addition, the malware executes a hex-encoded AppleScript that beacons out to one of two hardcoded command and control (C2) servers every 30 seconds. The beacon posts a list of running programs from the victim’s machine and executes any script received in response from the C2, effectively operating as a backdoor.
Meanwhile, a second part of the attack chain launches another Nim-based trojan which communicates over WebSockets (WSS) and downloads two bash scripts. The scripts steal browser data, shell history, Keychains, and Telegram databases, exfiltrating the data to other attacker-controlled infrastructure.
DPRK-aligned actors are increasingly taking advantage of macOS’s built-in scripting capabilities to enhance stealth and evade detection. At the same time, the adoption of lesser-known languages like Nim and Crystal (seen just earlier this year) allows attackers to craft multi-stage payloads that are less familiar to analysts. These choices reflect a trend toward blending in with native system behavior while leveraging novel tooling to complicate the work of security analysts.


