The Good | The White House Unveils Cybersecure Labeling Program for IoT Devices
A U.S.-wide cybersecurity certification and labeling program launched this week to guide consumers in choosing tech products that are less vulnerable to attack. The latest from the Biden-Harris administration, the “U.S. Cyber Trust Mark” is expected to enhance cybersecurity measures across popular smart devices used in homes, schools, offices, and more. The program is a collaborative one involving voluntary industry participation, oversight from the FCC, and stringent cyber standards set by NIST.
Today, the Biden-Harris Administration is launching the U.S. Cyber Trust Mark – a cybersecurity certification and labeling program that will help Americans more easily choose smart devices that are safer and less vulnerable to cyberattacks. pic.twitter.com/sBzUImz5TK
— The White House (@WhiteHouse) July 18, 2023
The U.S. Cyber Trust Mark enables consumers to identify which internet and Bluetooth-connected devices are cybersecure, including common items like fitness trackers, baby monitors, home security systems, and smart appliances. Suppliers that meet the program’s security requirements will bear a “Cyber Trust” label as early as next year. So far, participants include Amazon, Best Buy, Google, LG Electronics USA, Logitech, and Samsung.
Use of Internet of Things (IoT) devices has soared within the past decade. In 2023, there are an estimated 15 billion internet-connected devices in use globally, with that number expected to explode up to 29 billion by 2030. This widespread adoption makes IoT devices a lucrative target for cyberattackers. Seen as vulnerable entry points into private networks, IoT devices entice attackers to exploit, disrupt, or compromise systems and privacy.
FCC officials say that the mark will give consumers peace of mind and help them make more informed purchases. Additionally, program-approved devices will include QR codes allowing users to easily access any updates in applicable security information. The new program from the White House follows similar cybersafety labeling initiatives such as Singapore’s SG Cyber Safe Programme and the Cyber Essentials certification and trademark program from the U.K.’s National Cyber Security Center.
The Bad | Design Flaw In Google Cloud Increases Chances of Supply Chain Attacks
Security researchers this week discovered a critical design flaw in the Google Cloud Build service that could allow attackers to escalate privileges and tamper with production environments. Dubbed ‘Bad.Build’, the flaw gives attackers nearly full, unauthorized access to Google’s Artifact Registry code repositories.

With this kind of access, attackers would be able to impersonate the account’s continuous integration and delivery (CI/CD) service and run API calls. After taking control over the application images, attackers could then inject malicious code, poisoning customer’s environments with malicious applications and opening them up for potential supply chain attacks.
In their report, researchers warned that the impact of this flaw could be diverse as it applies to any organization using the registry as their main or secondary image repository. Disruption of this could, in turn, spread malware to a wider pool of users or lead to DoS attacks and data theft.
The Google Security Team has since revoked the logging.privateLogEntries.list permission from the default Cloud Build Service Account. However, the researchers claim that is a partial fix that does not address the flaw in the Artifact Registry and continues to leave users at risk of privilege escalation abuse and possible supply chain attacks. They recommend that users apply the principle of least privilege (PoLP) and implement cloud-centric security measures capable of detecting and responding to any identified anomalies in the behavior of the default Google Cloud Build service account.
The Ugly | Security Researchers Link JumpCloud Attack to North Korean State-Backed Threat Actor
Following a state-backed breach of Colorado-based software firm, JumpCloud, SentinelLabs researchers published findings linking the attack to a North Korean APT. The incident was first discovered earlier this month, after the company’s systems were targeted in a spear phishing attack. After discovery, JumpCloud forced a rotation of all admin API keys and notified customers to generate new keys. The company has since rebuilt the compromised infrastructure and shared IoCs with the community.
Review of the IoCs led SentinelLabs to associate the cluster of threat activity to a DPRK-sponsored APT who have been observed leveraging a supply chain targeting approach in previous campaigns. SentinelLabs mapped out the threat actor’s infrastructure to show the links between details of the intrusion to the underlying patterns, comprising domains and IP addresses, noted in similar campaigns. After correlating specific domains recently shared by GitHub to forensic analysis from JumpCloud’s ongoing investigation, SentinelLabs found clear links to NPM and ‘package’ themed infrastructure characteristic of other DPRK-linked campaigns they track.
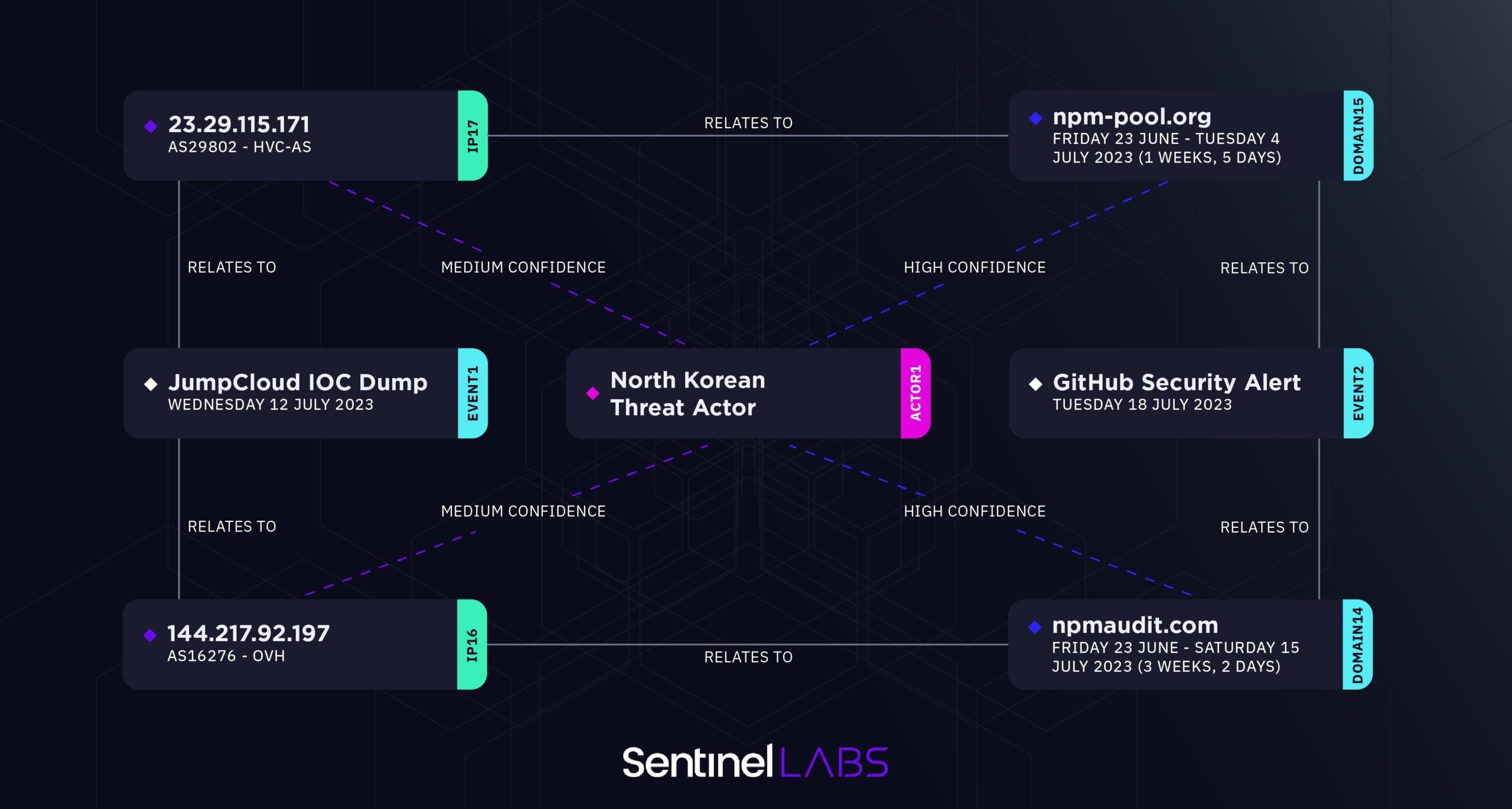
While JumpCloud emphasized that the intrusion was highly targeted and limited to specific customers only, it is evident that North Korean threat actors are continuously exploring new methods of infiltration, many of which seem to lean towards targeting supply chains. Numbers gathered in 2022 point to supply chain attacks as the leading cause of data breaches; 40% more than malware which had been, until recently, viewed as the core of most attacks. As more actors conduct supply chain attacks to pivot into high-value networks, researchers urge organizations to share threat intelligence, invest in advanced endpoint protection, and establish strong authentication and access controls.


