
The Good
The cybersecurity skills shortage is something we’re all concerned about, so it’s good news this week to hear of the launch of the U.S. National High School Cybersecurity Talent Discover Program. The online program involves students playing an aptitude game, CyberStart, which assesses the player’s ability in various skills relevant to the cybersecurity industry. The program is open to both boys and girls in every state, although girls participating in GirlsGoCyberStart must first excel there before being admitted to the boys program. Despite the gender distinction, previous versions of the program were widely praised by parents for encouraging girls to think of cybersecurity as a potential career path.

The Bad
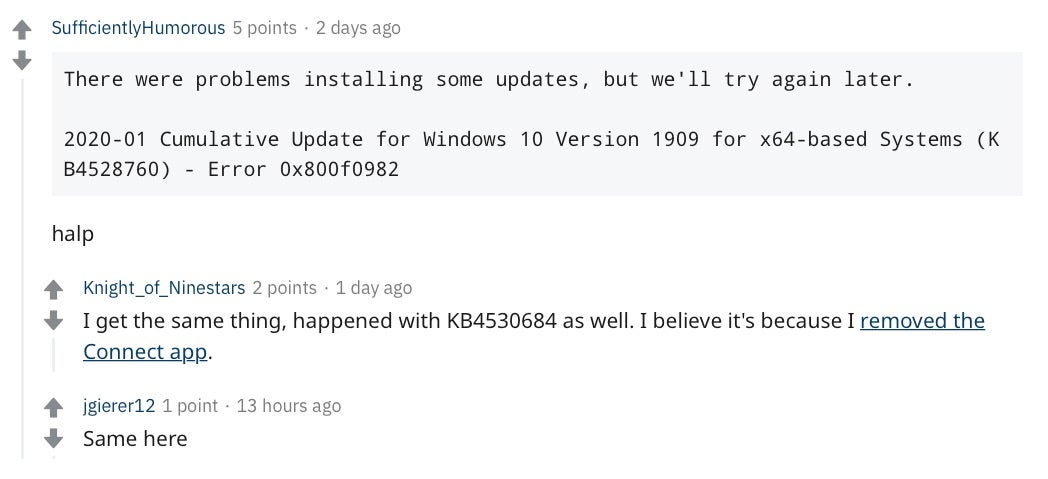
There’s no other contender for this week’s bad news: yep, it’s CVE-2020-0601, also going by nicknames like CurveBall and ChainOfFools. The bug in Windows CryptoAPI (Crypt32.dll) allows an attacker to use a fake security certificate to sign malware as trusted code, communicate over HTTPS and pass off malicious files and emails as benign. According to the NSA, who reported the bug to Microsoft, the flaw affects Windows 10, Windows Server 2016, Windows Server 2019 and applications that rely on the Windows OS to provide trust services. Complicating matters further, reports on Reddit suggest that the patch released by Microsoft on Tuesday is failing to install for some users, leaving those users without a path to mitigation. SentinelOne yesterday reassured its customers that any attempt to exploit the bug will be detected by its behavioral engine.
The Ugly
At the end of last year, we noted that Citrix disclosed CVE-2019-19781, an arbitrary code execution bug in its NetScaler Application Delivery Controller (ADC) networking product, and provided mitigation steps for the vulnerability. Unfortunately, the mitigation steps may have provided the clue needed by attackers to develop an exploit. Even less pretty, it seems that researchers have been squabbling among themselves about responsible disclosure, and dumps first by Project Zero India and then trustedsec on github have pretty much armed attackers everywhere with the tools needed to exploit an estimated 130,000 vulnerable devices.
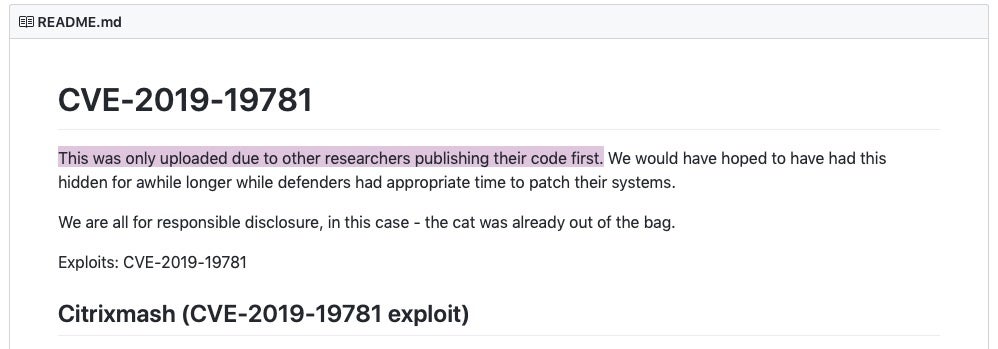
Social media has unceremoniously hash tagged this flaw as #shitrix and reports of active exploits in the wild are already coming in. Citrix have still not provided an actual patch for the bug, and the mitigation steps previously reported are said to be unreliable. Urgh!

