The Good
The world’s largest illegal marketplace on the dark web, DarkMarket, has been taken offline in an international operation led by German police and law enforcement agencies from Australia, Denmark, Moldova, Ukraine, the United Kingdom, and the USA (DEA, FBI, and IRS), with the support of Europol. The site had close to half a million users, over 2400 sellers, and had handled hundreds of thousands of transactions involving the trade of drugs, counterfeit money, stolen or counterfeit credit card details, anonymous SIM cards and malware. It is estimated that the site handled transactions equal to €140 million.

The takedown was made possible due to the arrest of an Australian citizen involved in the operation of DarkMarket near the German-Danish border over the weekend. The investigation allowed officers to locate and close the marketplace, and seize the criminal infrastructure of more than 20 servers in Moldova and Ukraine. The servers seized contained the data of many other users, sellers and operators and is expected to lead to additional arrests.
The Bad
The move to working from home has left many organizations vulnerable. Allowing employees to access organizational networks and cloud assets requires security tools and discipline that is often lacking, and attackers have taken notice.
The US Cybersecurity and Infrastructure Security Agency (CISA) has released an Analysis Report saying it is aware of several recent successful cyberattacks against various organizations’ cloud services. According to CISA, threat actors are using several vectors to exploit poor cyber hygiene practices within a victims’ cloud services configuration.
Gaining access into secured cloud environment requires the use of a variety of tactics and techniques – phishing, brute force login attempts, and possibly a “pass-the-cookie” attack – to attempt to exploit weaknesses in the victim organizations’ cloud security practices.
CISA noted that across several different incident reports, attackers tried to gain access by harvesting user credentials through malicious links. If that tactic failed, they tried harder, generating emails that spoofed a legitimate file hosting service account login. When they obtained the user’s credentials, they would send emails from the victim’s accounts to other employees and obtain their credentials as well. In some cases that wasn’t necessary: one organization allowing employees to connect via VPN left port 80 open…and in return received an aggressive brute force attack.
CISA noted that sometimes attackers simply followed the email-trail, exploiting the fact that employees set up email forwarding rules to automate sending work emails to their personal email accounts. In one case, attackers modified an existing email rule on a user’s account and redirected the emails to an account controlled by the actors.
CISA said that the activity could not be tied to any single threat actor, but they believe it is unrelated to the recent APT group said to be behind the recent SolarWinds breach.
The Ugly
Irresponsibility when it comes to holding customer data reached a new high this week. After social media giants banned President Trump’s accounts indefinitely, many of his supporters flocked to alternative social media platform Parler, which offered to host content without moderation, however heinous. Parler had been known to host extremists of all kinds, and has now been forced off Amazon’s hosting service and had its apps banned from various App Stores.
However, it seems the developers behind the platform were not particularly concerned about securing their users’ privacy, either. Before Parler went down, a hacktivist known as “@donk_enby” found a way to download and save nearly all the messages, photos, and videos in the order they were posted.
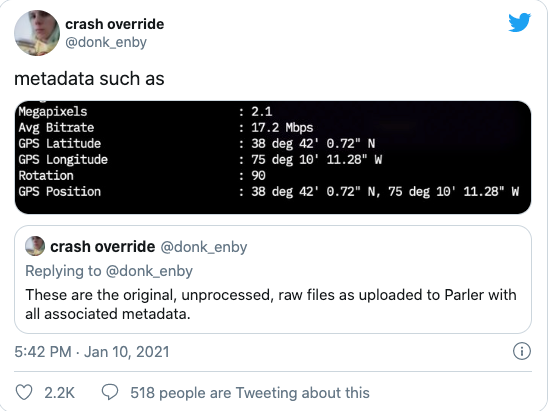
Capturing 99.9% of Parler’s entire content didn’t require any particular “leet” hacking skills, either. The site used an insecure direct object reference, or IDOR, which allows anyone to guess the pattern an application uses to refer to its stored data. Simply put, the posts on Parler were listed in chronological order: increasing a value in a Parler post’s URL by one gives you access to the next post on the site. In addition, Parler didn’t require authentication to view public posts and didn’t implement any mechanism to limit scraping like “rate limiting” that would prevent someone from accessing many posts in a short space of time. One cybersecurity expert decried the site’s architecture as “like a Computer Science 101 bad homework assignment”.
Now, many users fear that this data could be used against them in the aftermath of the Capitol Hill assault. Other hacktivists have already started sifting through the data and correlating messages, time and geolocation to pinpoint the location of the perpetrators in the riot (indeed, some posted from within the Capitol building). This is, of course, good news for law enforcement, but as a case study in how to host and secure potentially sensitive user data, it serves as an object lesson in how to fail, and fail big.


