The Good
It was a year ago almost to the week that we reported on a mass cyber hack against at least 130 social media celebrities. As we reported at the time, Twitter accounts belonging to the likes of Joe Biden, Barack Obama, Elon Musk, Bill Gates, Apple and Uber were all breached and used to pull off a Bitcoin scam that netted the hackers over $100,000 in less than 24 hours. This week, it looks as though cybercops have caught up with yet another of the alleged perpetrators.
Police in Spain arrested a 22-year old British man, Joseph O’Connor, on suspicion of being behind the attack. Three others, two from the U.S and another from the U.K, have already been charged in the case. O’Connor faces computer intrusion charges relating to the Twitter hack as well as similar intrusions of TikTok and Snapchat. The Department of Justice says he is also being charged with cyberstalking a juvenile.
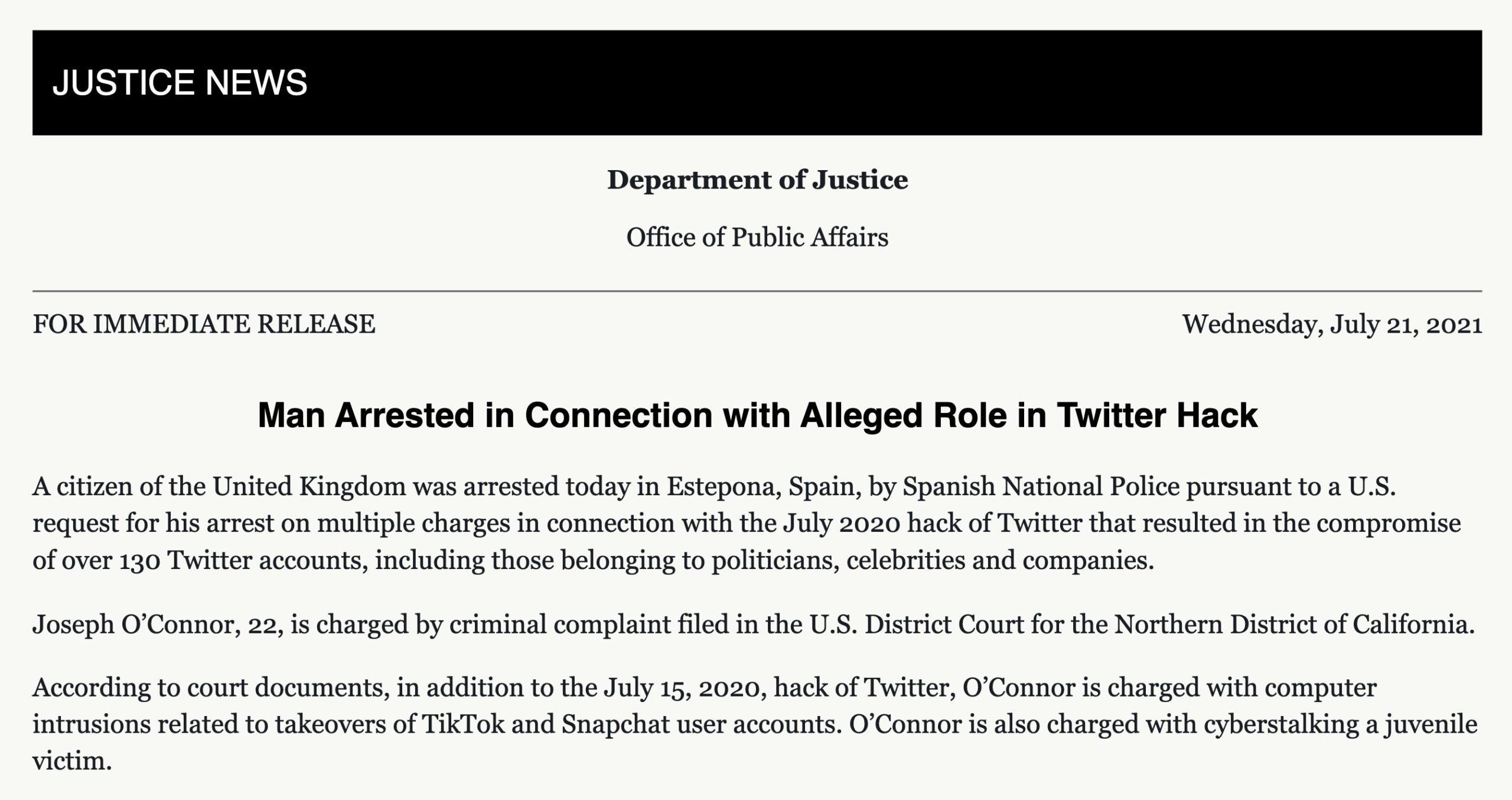
With the help of the U.K.’s National Crime Agency, the Spanish National Police arrested O’Connor on Wednesday after a request from U.S. authorities following a criminal complaint filed in the U.S. District Court for the Northern District of California. Once again, international law enforcement cooperation has proven vital in bringing those who perpetrate cyber crimes to justice.
The Bad
There was already plenty of controversy swirling around the Tokyo Olympics – from Russia’s stealth involvement to whether the event should even be taking place given the ongoing pandemic – but of course, cyber attackers had to get in on the act, too.
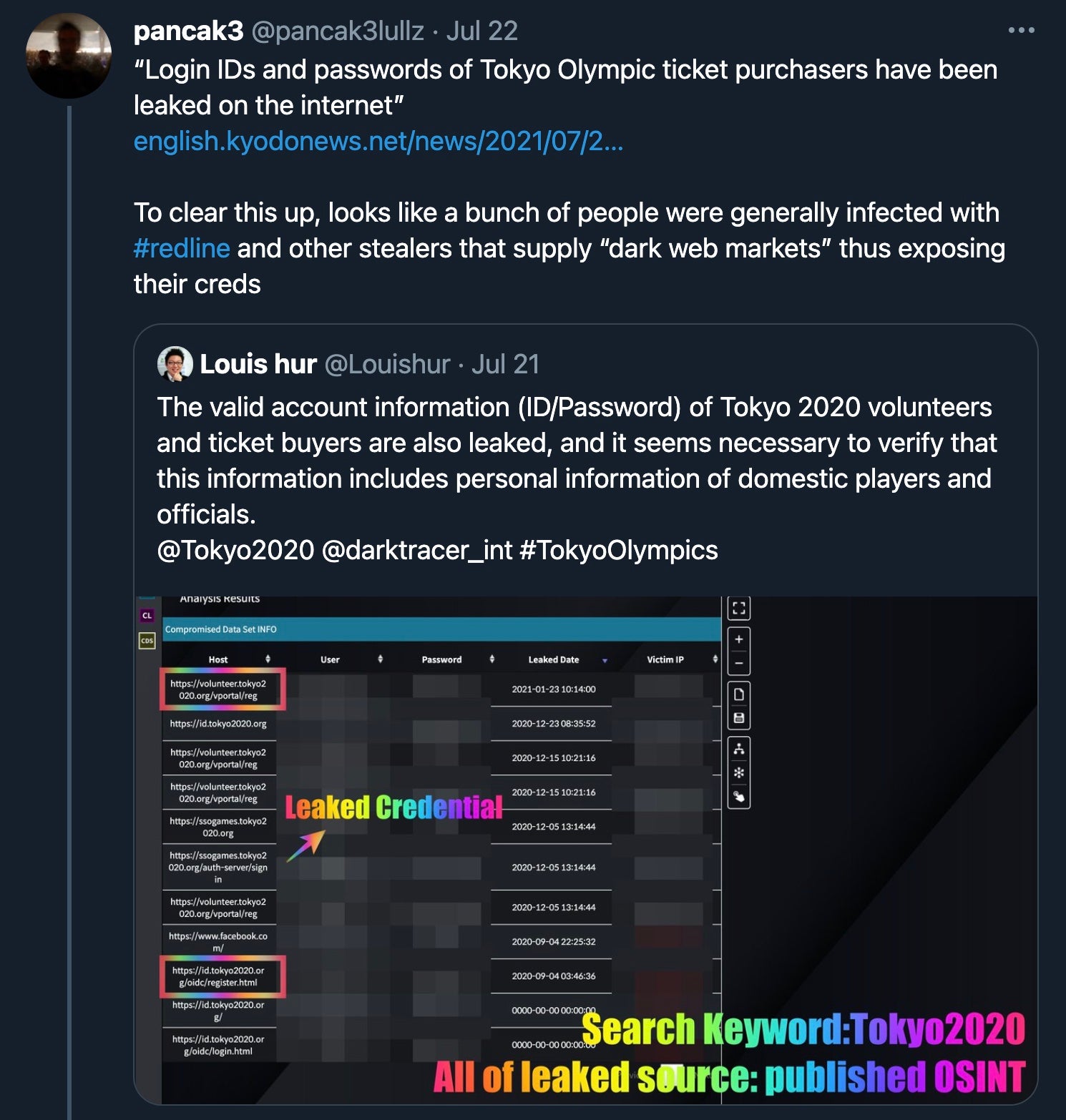
Initially, news broke early in the week apparently from a Japanese government source suggesting that login IDs and passwords for the Tokyo Olympic ticket portal had been posted to a Darknet “leaks” website following a breach. A spokesperson for the Tokyo 2020 Olympics International Communications Team later contradicted that claim, saying the government source was mistaken.
While it seems there had been some leaks, these were not related to a breach of the ticket portal. Rather, it appears some ticket holders as well as Olympic Village volunteers had been infected with malware and leaked their own credentials.
It seems these individuals were infected with infostealer malware that exfiltrated credentials stored in their browsers. The data was subsequently offered for sale on underground marketplaces.
While it’s certainly welcome to learn that a general breach of the Olympics ticket portal hasn’t taken place, there are concerns that threat actors are targeting the event. The FBI released an alert this week warning that cyber actors who wish to disrupt the event could use distributed denial of service (DDoS) attacks, ransomware, social engineering, phishing campaigns, or insider threats against entities associated with the Tokyo 2020 Summer Olympics. All involved are advised to remain vigilant and maintain best practices in their network and digital environments.
The Ugly
News has been breaking across mainstream media since Sunday regarding the use of iOS and Android spyware being sold to authoritarian regimes by private security contractor NSO. Apparently, the spyware platform known as “Pegasus” is meant to be used to target ‘persons of interest’ to governments and law enforcement agencies, but campaigners such as Amnesty International claim that the spyware is used by oppressive regimes to facilitate human rights violations around the world on a massive scale.
While opinion remains divided as to the true extent of the use of NSO’s spyware in the wild, there’s no doubt that there are genuine concerns that the spyware has been used to expose activists, journalists and politicians critical of certain governments.
Meanwhile, researchers claim that they have proof that the Pegasus spyware has successfully infected iPhone 11 and iPhone 12 models through iMessage zero-click attacks. Pegasus marketing material offers prospective clients unlimited access to targets’ mobile devices while “leaving no trace on the target devices”.
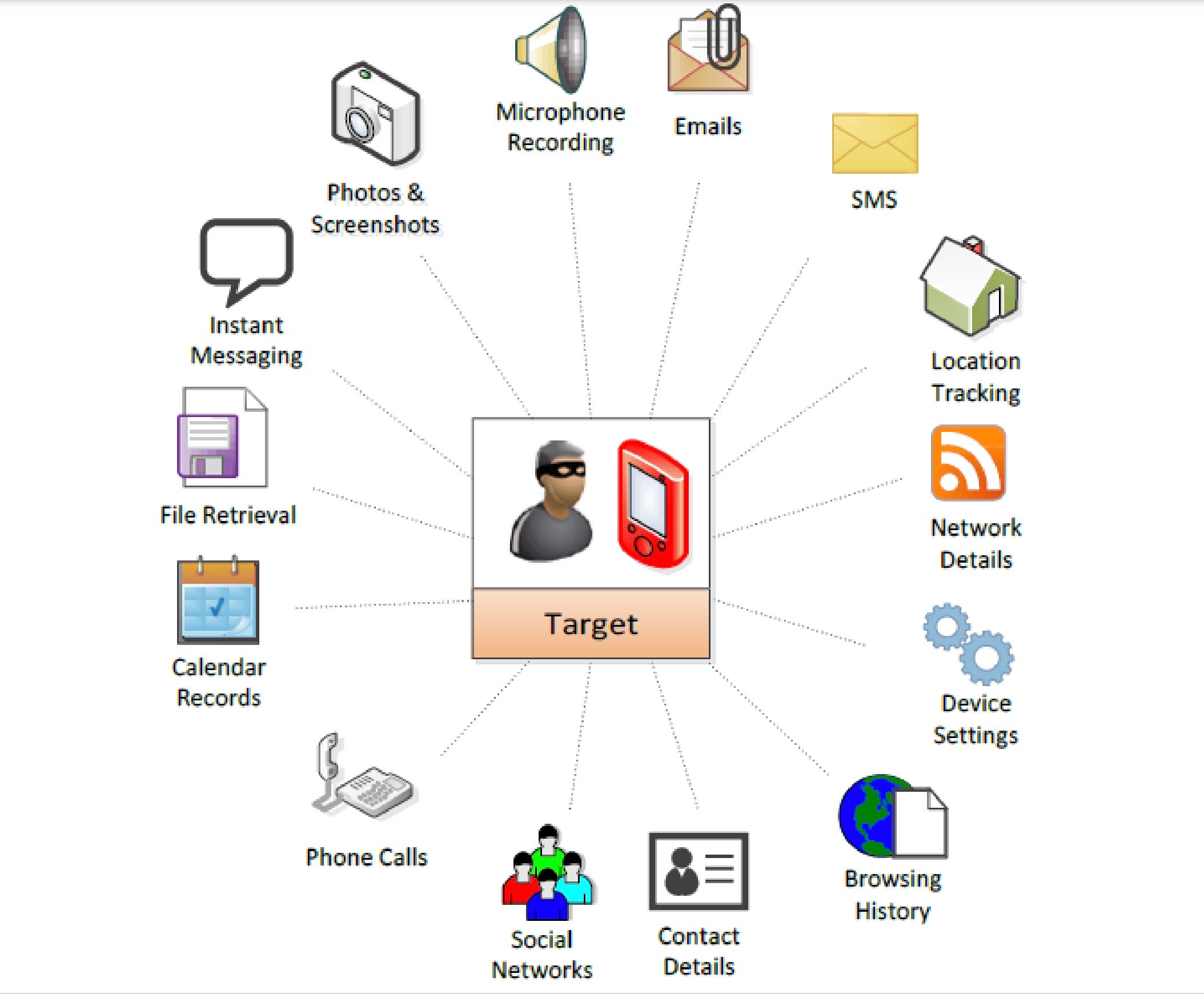
NSO, for its part, disputes the claims made in the most recent revelations, arguing that the number of targets is substantially lower than the 50,000 claimed by campaigners, and that the company vets all its clients to ensure abuses do not occur.
Amidst all of this is another ongoing debate about Apple’s approach to security. The famously-secretive device manufacturer argues that iPhone security is enhanced by its opaque, proprietary operating system and Apple’s tight reign on application distribution. Many security researchers and privacy activists, on the other hand, say that such a ‘security by obscurity’ approach only serves to abet criminals by making it impossible for users to detect whether their devices have been compromised.
It’s a debate that’s not going to go away any time soon. Readers might like to reflect on whether they would be happy using desktop and laptop computers that, by design, were unable to run any third-party security software. If one feels nervous at the prospect of leaving computer security entirely in the hands of an OS vendor, it’s hard to imagine why we should be comfortable doing the same with our phones.