The Good
This week, the Justice Department announced that they had disrupted the activities of a group of North Korean state-sponsored threat actors that targeted healthcare facilities in 2021, successfully seizing and returning approximately $500,000 of ransom money to the victims.
In a keynote address at the International Conference on Cyber Security, U.S. Deputy Attorney General Lisa Monaco walked through the two incidents in which a ransomware group affiliated with the North Korean government targeted healthcare organizations based in Colorado and Kansas with Maui ransomware.
According to Monaco, the FBI and DOJ first encountered Maui ransomware during the Kansas-based incident. The state-sponsored threat actors encrypted the Kansas hospital’s servers and left a ransom note warning hospital administrators that the ransom would double if it was not paid in 48 hours.
However, when the hospital paid the ransom to give their patients the care they needed quickly, they also notified the FBI, which worked with the DOJ to trace the ransom payments using tactics from their investigations on the Colonial Pipeline attack. Law enforcement traced the funds back to Chinese money launderers that frequently aid North Korean threat actors in transferring funds and from this discovery, identified relevant breaches with the Colorado-based medical provider and potential victims overseas.
According to the Deputy Attorney General, recovery of the funds and identification of the Maui ransomware strain directly resulted from the Kansas’ hospital’s rapid disclosure. We hope this major victory encourages other enterprises and organizations to disclose incidents and contribute to ongoing investigations.
The Bad
Researchers have released new information surrounding the Conti ransomware gang’s attack on the Costa Rican government.
A report from investigators broke down each action the threat actors behind Conti ransomware took over five days to compromise Costa Rica’s government.
First, the cybercriminals gained access to the Costa Rican Ministry of Finance’s systems over a VPN connection, using credentials that were exfiltrated from a previous malware attack. After setting up and executing over 10 Cobalt Strike beacons and gaining local network domain administrator access, Conti ransomware operators scanned the Costa Rican government’s network, moved laterally and exfiltrated credentials using Mimikatz. To establish persistence, the threat actors also downloaded Atera’s remote access tool on less active environments before completing data exfiltration.
How Conti ransomware hacked and encrypted the Costa Rican government – @Ionut_Ilascuhttps://t.co/82GVgUFsnH
— BleepingComputer (@BleepinComputer) July 21, 2022
The Conti gang demanded that the Costa Rican government pay a $10 million ransom, which the gang then doubled after the government declined to pay. Because the Conti operators had successfully targeted multiple government offices, the breach triggered a national emergency that took over a month to remediate and was Conti’s final attack using its current branding. After this attack, the ransomware gang shut down their leak sites, and its members scattered to other groups of threat actors.
In the fallout of Conti’s final operation, we’re left with a sobering reminder that although a ransomware gang can shut down, it’s more than likely that the threat actors and technology behind these devastating attacks can emerge under a new name to target innocent people and organizations again.
The Ugly
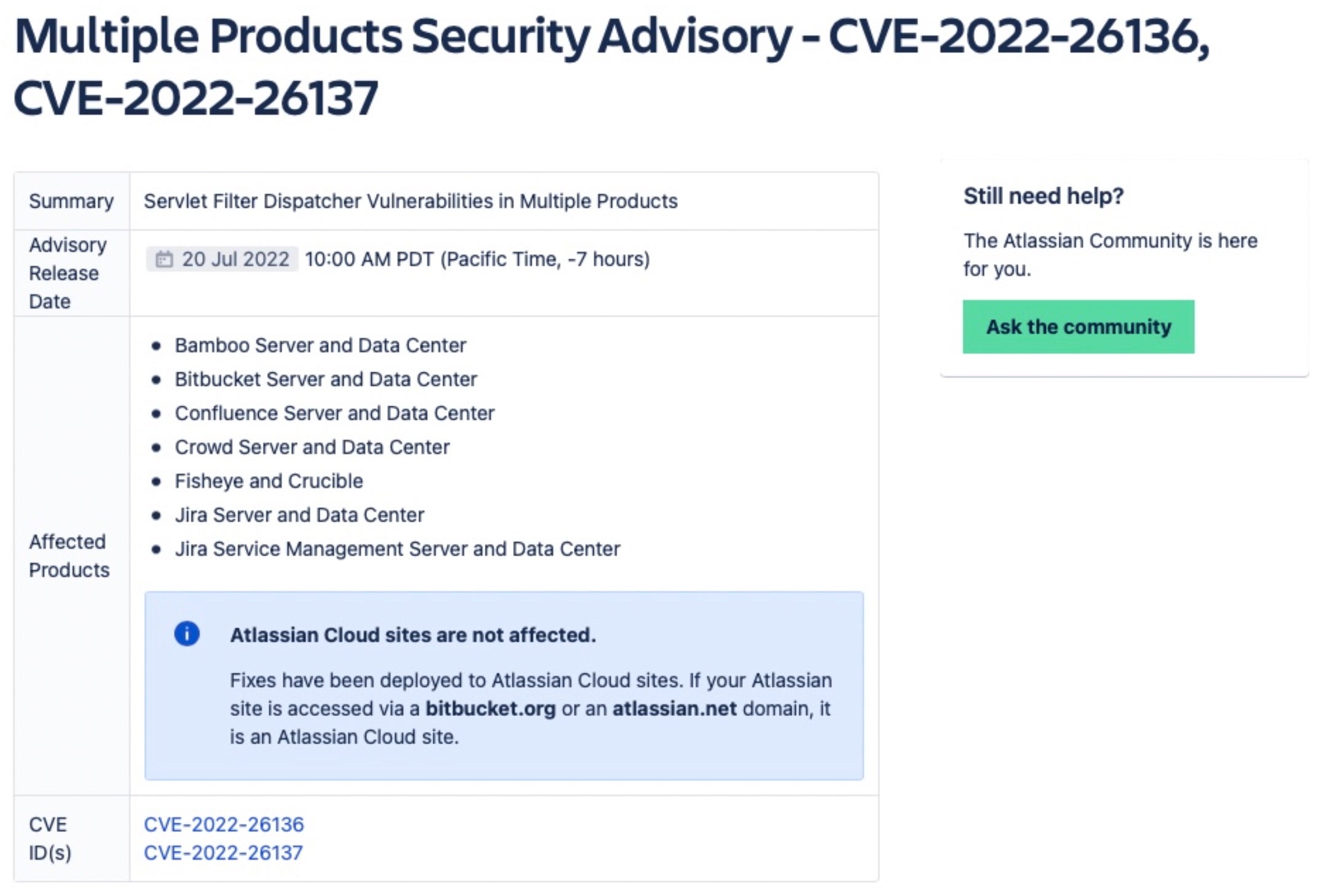
This week, Atlassian disclosed three vulnerabilities, two of which are considered critical flaws that impact almost all of their products.
In two security advisories published on July 20th, the popular software firm disclosed “Servlet Filter dispatcher vulnerabilities” that impact users of Bamboo, Bitbucket, Confluence, Crucible, Fisheye, and Jira.
The first critical vulnerability, tracked as CVE-2022-26136, allows threat actors to bypass custom servlet filters for third-party applications to use in enforcing authentication. Attackers can exploit this vulnerability to trick users into sending a malicious HTTP request which bypasses a servlet filter designed to validate Atlassian’s “Gadget” modules. These HTTP requests are capable of executing arbitrary JavaScript in a victim’s browser.
The second critical vulnerability, CVE-2022-26137, could allow a remote, unauthenticated attacker to invoke additional servlet filters when an application processes requests. Atlassian’s advisory also warned that attackers could bypass servlet filters related to cross-origin resource sharing (CORS) requests and access a vulnerable application using the victim’s permissions.
The final flaw impacts Confluence users. Questions for Confluence, one of the platform’s apps, creates a Confluence user account when a user enables it on Confluence Server or Data Center. This account uses hardcoded credentials and is designed to support cloud migrations. According to Atlassian’s advisory, the hardcoded credentials were leaked on Twitter and an unauthenticated attacker could use the information to access the app’s user account and any content accessible to members of the “confluence-users” group.
While Atlassian discloses more information about these vulnerabilities and rolls out patches, we would urge enterprise customers to follow the mitigation recommendations outlined in the company’s advisories.