
The Good
After 8 years of waiting, corporate whisteblower James Glen finally received settlement this week from Cisco Systems, who were found to have made false claims regarding video surveillance software the tech giant sold to US government buyers including Los Angeles International Airport, Washington D.C police and the US Army, Navy, Air Force and Marine Corps. Glen exposed vulnerabilities in Cisco’s Video Surveillance Manager which could allow hackers to compromise an organization’s entire network. Despite being told of the vulnerability in 2008, Cisco failed to fix the flaws until 2013 and had continued to ship the flawed software to government buyers in the meantime. The company were handed down a fine in excess of US $8m for the lawsuit filed in 2011. The case is believed to be the first successful prosecution of a cybersecurity company under the False Claims Act. Industry watchers believe it may serve as a precedent and open the way to further similar lawsuits of cyber security vendors peddling products with known vulnerabilities.
More good news for privacy watchdogs this week as Apple announced that it would halt the practice of using human contractors to listen in to user Siri recordings. The practice had been revealed last Friday by a British newspaper. Citing contractors who had undertaken the work for Apple, the newspaper revealed that staff regularly heard snippets of confidential conversations that Siri had inadvertently picked up. Apple now say they have suspended the practice and are conducting “a thorough review”. Good to see Apple move on this in an uncharacteristically speedy and transparent fashion.
The Bad
The big, bad news story of the week is, of course, the Capital One leak of over 100 million consumer records by ex-Amazon employee-turned-hacker Paige A Thompson. Since our report on Wednesday, further claims are emerging that Thompson, known online by her handle ‘erratic’, may have compromised other organizations aside from Capital One. These could possibly include Ford, InfoBlox, UniCredit, and the Ohio Department of Transportation. Interestingly, and perhaps reassuringly for Amazon if true given the hack could undermine a lucrative Pentagon contract, the Ohio DoT is not an AWS customer.
In related news, CEOs beware as politicians try to use the incident to win backing for a bill that would see business leaders jailed for data breaches.
The warnings keep coming – Microsoft (twice), Homeland Security and the NSA have each issued separate advisories in the last few months – but reports suggest that the BlueKeep vulnerability still remains largely unpatched. Have organizations really learned nothing since Eternalblue, WannaCry and NotPetya? Now, Metasploit developers Rapid7 say they’re observing a significant increase in malicious RDP (Remote Desktop Protocol) activity, suggesting attackers are stepping up scans for vulnerable devices.
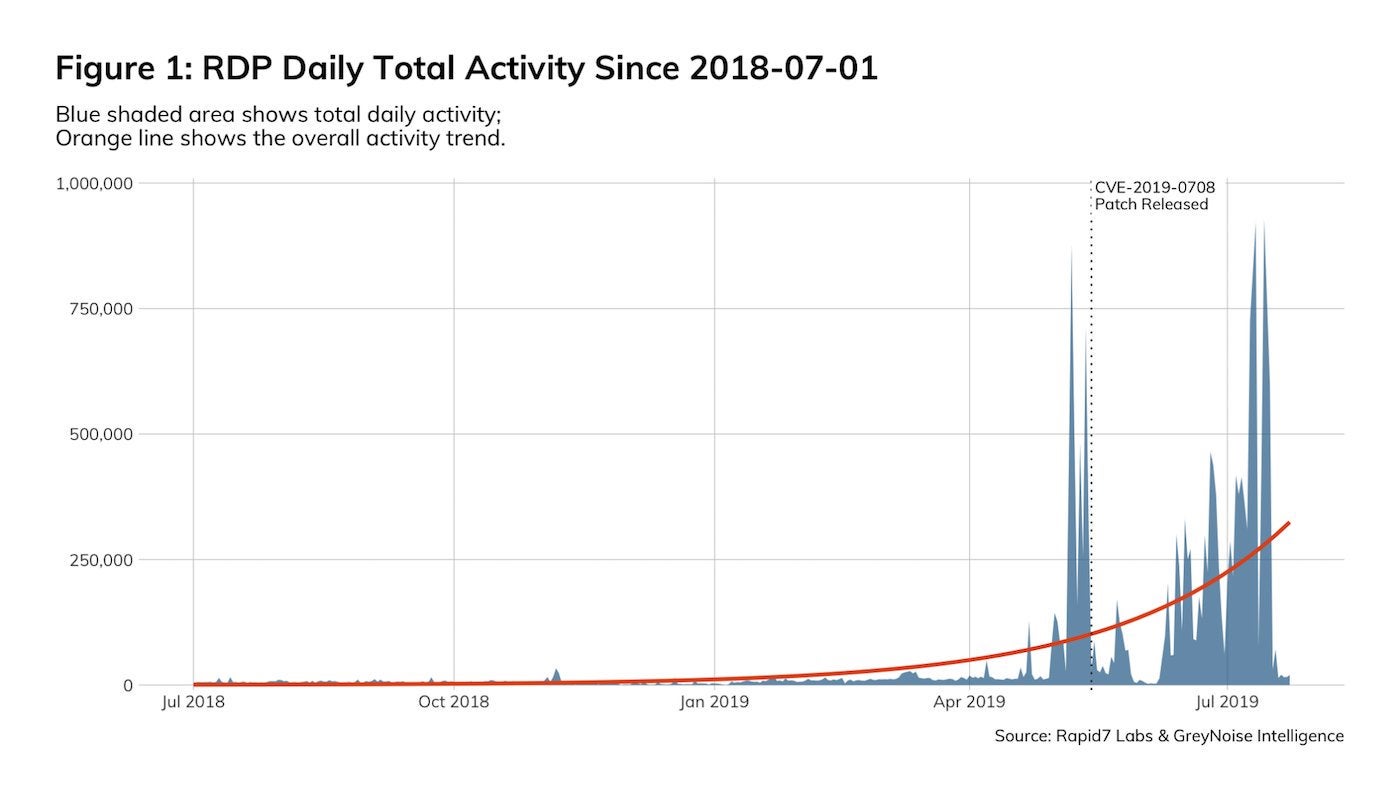
Rapid7 are also readying a MetaSploit exploit module for BlueKeep to “help defenders and penetration testers demonstrate and validate risk”. Aside from the nearly 1m devices vulnerable to the wormable BlueKeep vulnerability that are exposed on the public internet, security researchers point out that this number does not take into account the unknown number of vulnerable devices on internal networks. Is your organization prepared for the first BlueKeep-powered ransomware?
The Ugly
It’s curious how privacy problems keep coming back to bite Apple, despite their public positioning as the company that takes user privacy seriously. We’ve spoken before on the dangers of Bluetooth, but now researchers have found that Apple’s Bluetooth LE protocol used in recent versions of iOS are leaking data to anyone close enough to listen in on it. Exposed data includes the current status of the device, device name, Wifi status, battery info and, in some circumstances, possibly even the cell phone number.

New cybersecurity laws in China are set to hit US tech firms as Beijing looks to increase regulation on network equipment, data storage and ‘critical information infrastructure’ procured from overseas companies. Cisco and Dell, among others, could find it increasingly difficult or expensive to do business on mainland China, particularly as the exact nature of the cybersecurity laws appears to be deliberately vague while the US and China remain locked in a tit-for-tat trade war. Some suggest that China’s new cybersecurity laws may be more or less draconian for US companies depending on how things shake out in the current spat over tariffs.

