The Good
Let’s introduce this week’s good news with a pop quiz: What do four Russians, two Chinese and three organizations based in China, North Korea and Russia all have in common? No, they’re not all part of some multinational cybercrime gang, although they have all been accused of being involved in various cybercrime activities. The thread that ties all these actors together is that they are the first names to appear on a list of EU sanctions aimed directly at hacking crews.
Two Chinese individuals, Gao Qiang and Zhang Shilong, along with a Chinese company, Huaying Haitai, have been sanctioned for their suspected role in hacking MSPs as part of Operation Cloud Hopper and for being members of APT10, an advanced persistent threat group that has repeatedly targeted pharmaceutical, aerospace and defense industries. Meanwhile, Russian nationals Alexey Valeryevich Minin, Aleksei Sergeyvich Morenets, Evgenii Mikhaylovich Serebriakov, and Oleg Mikhaylovich Sotnikov were included in the sanctions list for their participation in APT28 and an attempted intrusion of the OPCW (Organisation for the Prohibition of Chemical Weapons) in 2018.

© iStock/pixinoo
The two remaining organizations added to the sanctions list are the GRU’s Main Center for Special Technologies (GTsST), thought responsible for releasing NotPetya ransomware on the world, and Chosun Expo, a North Korean business said to have financed the development and outbreak of WannaCry ransomware. Chosun Expo is also believed to be supporting the Lazarus group’s activities.
Those on the list will be subject to asset freezes and travel bans, and they will also be prevented from doing business with any individual or company within the EU. The great benefits of economic sanctions are that they neither require irrefutable proof in a court of law nor the physical apprehension of the suspects. The sanctions will restrict those named in their ability to operate within the EU and hit the bad guys where it hurts most: in their wallets.
The Bad
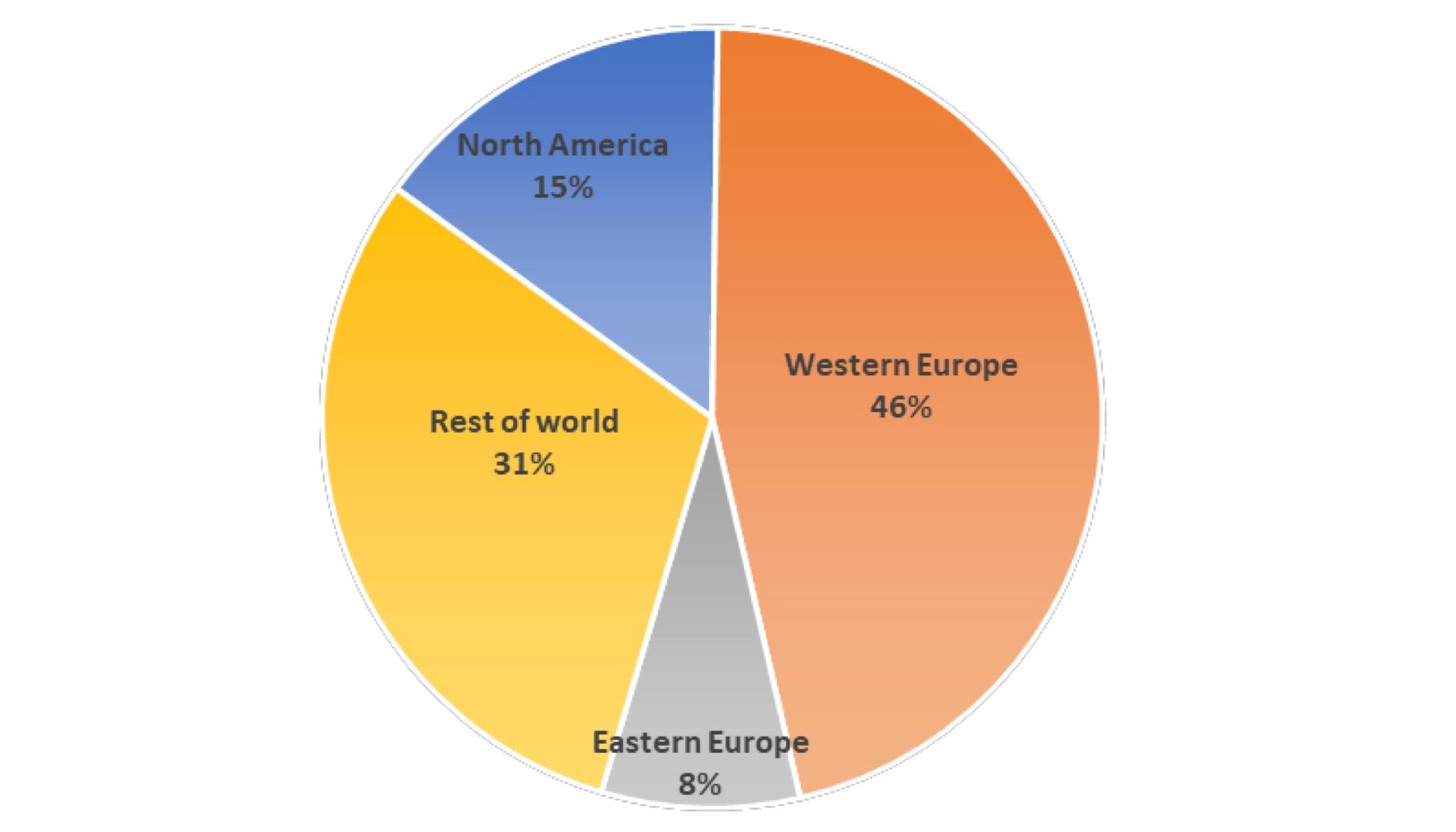
A joint alert from the UK’s National Cyber Security Centre (NCSC) and the Cybersecurity and Infrastructure Security Agency (CISA) in the United States has warned that a strain of malware known as ‘QSnatch’ or ‘Derek’ is infecting tens of thousands of QNAP NAS devices worldwide. Almost half the known infections are in Western Europe, but a significant number, almost 8000, are in the US and just under 4000 are in the UK.
Analysis shows that the malware has a number of functionalities, including a password logger, credential scraper, backdoor and data exfiltration. Persistence is achieved through preventing updates and modifying the NAS’ hosts file so that updates are never installed. It is not yet known how devices become infected, but QSnatch is said to be injected into the device’s firmware during the initial infection stage.
Although the alert stresses that the attacker infrastructure does not seem to be currently active, the malware remains a threat to unpatched devices. Organizations are urged to ensure their devices are fully patched, and those still running a vulnerable version are advised to do a full factory reset. More details on mitigation can be found here.
The Ugly
With genuine news stories repeatedly labelled “fake news” and fake news increasingly being redistributed on social media platforms as trustworthy, uncovering online disinformation is getting harder by the day, and disinformation campaigns appear to be getting uglier.
This week, it has been reported that one particular threat actor group has gone the proverbial extra mile by hacking the content management systems of news websites and posting their own fake stories. These have included fabricated content claiming a US armored car ran over and killed a Lithuanian child and that the first COVID-19 patient in Lithuania was a US soldier engaged in “events with child and youth participation.”
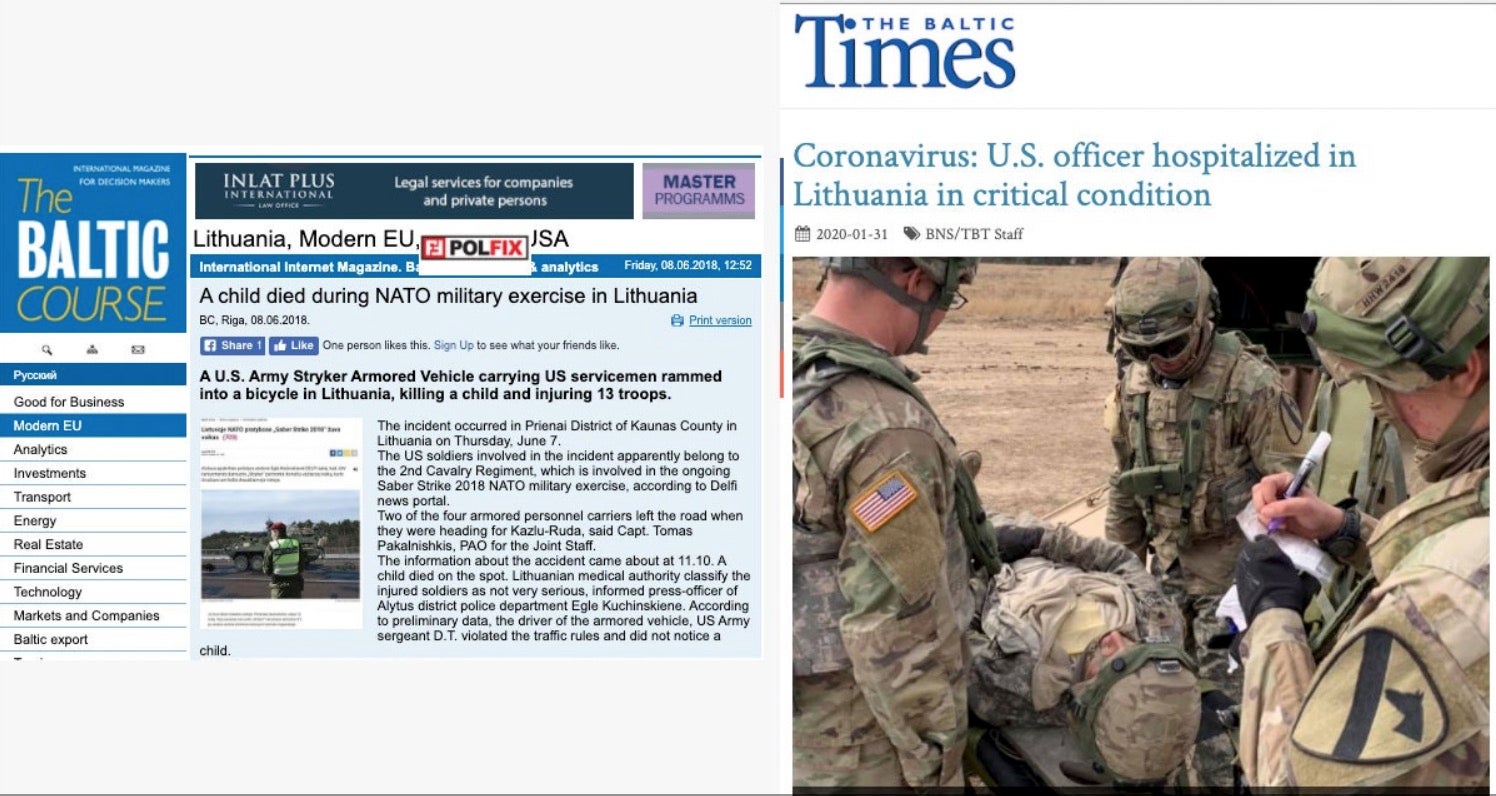
The smears have not been restricted to Lithuania. The same hackers have also targeted news sites in Poland, again with a focus on anti-US and anti-NATO sentiment, and the deep concern now is whether this tactic will spread to the US as we run up to the 2020 election. Although the researchers investigating the campaign, dubbed Ghostwriter, say they can’t concretely tie it to Russian-backed actors at the present time, they have warned that “it’s certainly in line with” Russian interests and they “wouldn’t be surprised” if that’s “where the evidence leads us.”
Clearly, fake news, deep fakes and online disinformation are threats we will all have to be extra vigilant against as the already-tumultuous year of 2020 plays out to a close.


