The Good
U.S. Cyber Command continues to fight the good fight by sharing malware samples with the rest of the industry. This week, the military unit shared samples of ElectricFish malware, a tunneling tool discovered in May and attributed to APT38, a North Korean affiliated group said to focus on financial theft. ElectricFish is a Windows 32-bit command line tool that enables attackers to use tunneling to exfiltrate data from a backdoored system.
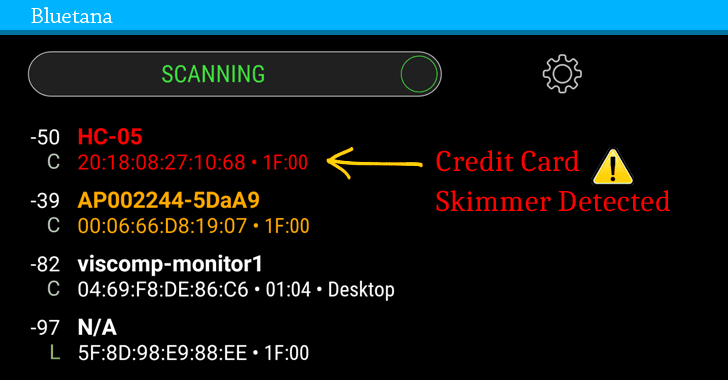
Nice to see some good news this week concerning Bluetooth, particularly after the recent revelation that iOS devices allow snoops to leverage the protocol to surreptitiously gather device data. Turning the tables, researchers have developed an app that can sniff out credit card skimmers at gas stations. Dubbed ‘Bluetana‘, the app is currently only available to gas pump inspectors but has already been used to flush out 64 skimmers in Arizona, California, Nevada and Maryland.
The Bad
Long before most people started to think too much about computer security – well, 2001 anyway – Microsoft introduced a nice feature for multilingual users of Office XP. The feature helpfully pops up a small ‘composition’ window that tries to predict a foreign language character (think Simplified Chinese, Korean or Japanese characters) based on the Roman characters you type. Sounds great. Fast forward to 2019 and Project Zero’s discovery that the underlying protocol for this feature – the Text Services Framework – exposes users of every version of Windows ever since, regardless of whether you have installed foreign language support or not, to a privilege elevation vulnerability. An attacker needs login credentials first (so, no RCE here), but any user can quickly and reliably elevate to root. The bug is fixed in the latest available patch and all Windows users are urged to patch without delay.
The Ugly
Kaspersky Labs – who’ve been out-of-favor with the US Government since late 2017 – have been exposing their users to the possibility of cross-site internet tracking. Kaspersky products intended to provide internet security – Kaspersky Antivirus, Internet Security, Total Security, Free Antivirus, and Small Office Security – were found to be injecting a uniquely identifying string into every web page a user visits. The string is part of a URL that locates a remotely-hosted JavaScript that Kaspersky use to determine if a webpage is malicious or not. As each user was assigned a unique, persistent string, websites and malicious scripts could track the user from one site to another. Kaspersky patched the flaw (CVE-2019-8286) several weeks prior to the bug being disclosed by replacing the UUID-style string with a fixed, generic string for all users.
Huawei, another company that are not in the US government’s good books at the moment, have reportedly been aiding at least two African nations in their attempts to suppress political opponents and restrict internet freedoms. The company’s employees apparently lent their assistance to intelligence agencies in Zambia and Uganda to hack WhatsApp and Skype communications and shutdown news sites unfavorable to the Ugandan government. For their part, Huawei have denied the allegations.