The Good
This week there were some significant updates surrounding the ongoing effort between Binance and the Ukraine Cyber Police. On August 18, new details were released, in a joint press release, from the collaborators. Through their combined efforts, dubbed “Bulletproof Exchanger”, law enforcement were able to track and ultimately arrest multiple individuals involved with malicious cryptocurrency exchanges, and the laundering of approximately $42 million in illicit funds. The individuals concerned were heavily involved in launching multiple malicious cryptocurrency exchanges, as well as advertising their services in various dark corners of the internet. The cybercriminals directly assisted ransomware groups and other fraudsters with masking and obfuscating transactions, allowing them to convert their tainted profits into usable currency.

Through the “Bulletproof Exchanger” program, Binance has been able to identify and track data and behaviors that are indicative of these criminal activities (malicious exchanges, transaction cleaning). This effort allowed Binance to build a dynamic database of indicators specific to these actors and their activities. Artifacts such as user traits, DNS events, and blockchain analytical data have all become powerful tools that can be used to counter this sort of criminal activity.
This case marks the first true victory for the “Bulletproof Exchanger” effort. Binance has indicated that they intend to continue to operate and expand the project, stating “Fighting money laundering, ransomware, and other malicious activity is of critical importance to the well-being of the community and industry growth.” At SentinelOne, we could not agree more and applaud and support this ongoing effort.
The Bad
This week, CISA (Cybersecurity and Infrastructure Security Agency) released an updated malware analysis report on the North Korean-backed remote access trojan (RAT) BLINDINGCAN. Malware Analysis Report AR20-232A describes details around the RAT, which is being used to target high-value government contractors and related entities, notably including those in the defense and energy industries.
The malware is being attributed to the North Korean-backed threat actor known variously as Hidden Cobra / Lazarus / APT38. The malware analysis report focuses on malicious documents and DLLs associated with the BLINDINGCAN RAT. The documents are Microsoft Word documents which, upon opening, attempt to connect to an external server to download additional payloads. Both 32 and 64 bit versions of the payloads exist. The documents also initiate keylogging routines, and attempts to gather basic system information.
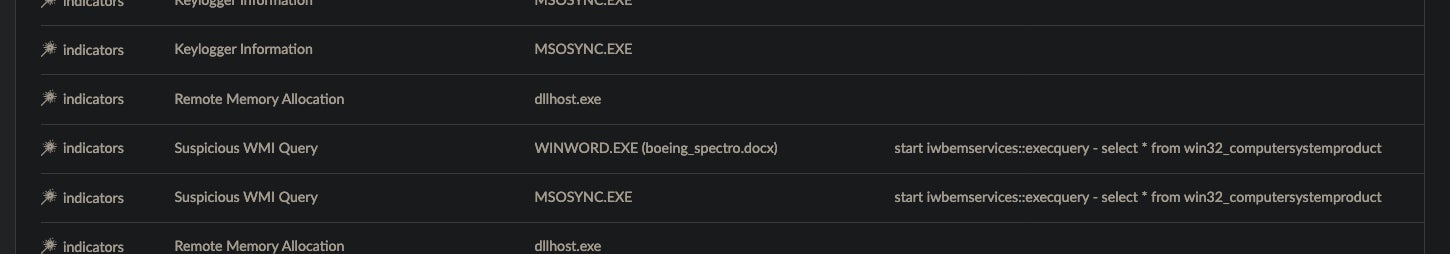
Of note, this is the 12th alert issued by CISA this year. SentinelOne Endpoint Protection is capable of preventing / detecting malicious behavior associated with BLINDINGCAN and artifacts cited in AR20-232A.
The Ugly
The week would not be complete without mention of another high-value ransomware target. Unfortunately, our highlight this week revolves around Carnival cruise lines. In a recent SEC 8-k filing, Carnival disclosed very limited details around the attack. Carnival also released a joint press release with PLC concerning the ransomware incident, with data nearly identical to that stated in the SEC filing.

Promptly upon its detection of the security event, the company launched an investigation and notified law enforcement, and engaged legal counsel and other incident response professionals. While the investigation of the incident is ongoing, the company has implemented a series of containment and remediation measures to address the situation and reinforce the security of its information technology systems.
Details around the family of ransomware, or any sort of attribution for that matter, have yet to be publicly disclosed. This attack highlights a few interesting things. First of all, as we know, highly-motivated ransomware operators are still very active and will target their resources wherever they see the most potential for profit and/or disruption.
The other, lesser known, bit here is that remediation becomes a huge hurdle for these types of attacks. The topology of a network like Carnival’s differs quite a bit from more than land-based entities. Having to rely on slower or more segmented networks (as they do with the cruise ships out at sea) can greatly complicate the process of remediation. How do you approach remediation when you can only connect to the ships’ systems during limited times each day? How do you approach remediation when your bandwidth is severely limited? This should serve as a reminder that prevention is absolutely critical. This is especially true in a time where ransomware authors are more innovative, aggressive and greedier than ever.


