
The Good
Apple, Microsoft and now Google have all made important announcements about new and extended bug bounty programs recently. This week, Google took their turn in announcing a new program to reward the reporting of data abuse issues in Android apps, Chrome extensions and OAUth projects through the HackerOne vulnerability disclosure platform. The program is intended to help find abuses by unscrupulous developers who sell or misuse user data or violate Google’s Privacy policies. The company have also expanded their existing Google Play Security Rewards Program to include apps with 100 million or more installs.
Another massive botnet bit the dust this week after French police and the FBI remotely removed RETADUP malware from over 850000 infected devices. The French police replaced the attackers’ C2 server, which was being hosted by a provider in the Île-de-France region, with one of their own. The benign server then leveraged the C2’s original protocol to instruct infected clients to remove the malware. In a tweet, the French cyber cops said
“The gendarmerie has dismantled one of the largest networks of pirated computers in the world! In collaboration with the FBI, French cyber police managed to “disinfect” more than 850,000 computers remotely. A world first!”
The Bad
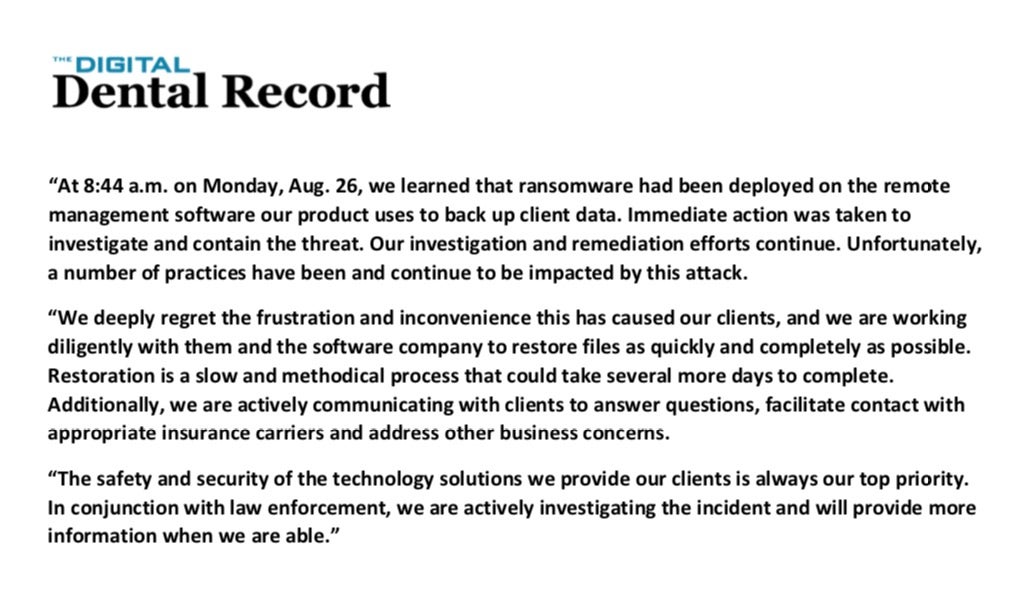
The rise in ransomware attacks continues unabated, and now even dental practices are feeling the pain as hundreds this week fell victim to a supply chain attack that delivered Sodinokibi ransomware. A targeted attack on the developers of DDS Safe software resulted in hundreds of dental practices finding themselves locked out of patients records. The attack is particularly bruising for the companies behind the sofware, The Digital Dental Record and PerCSoft. The developers tout their product as a backup service offering customers ransomware protection, but the attack forced them to pay the ransom in order to acquire a decrypter from the criminals and pass it on to their affected customers. It just goes to underline the importance of having real ransomware protection no matter what business you’re in.
Apple just can’t seem to catch a break at the moment. After last week’s revelation of vulnerabilities affecting almost every version of iOS comes yet more more bad news for the company’s security reputation. Google’s Project Zero team have just released details of a sustained, two-year campaign exploiting no less than fourteen separate vulnerabilities and five privilege escalation exploit chains in iOS (versions 10 through to 12.1). Hackers used the flaws to conduct drive-by attacks placing implants on iOS devices visiting a small number of malicious websites. The implants, which required no interaction from the user other than landing on one of the malicious sites, were used to steal user files and location data. The malware was capable of receiving commands from the attackers’ C2 server and was able to access the databases used by encrypted chat apps such as Messages, Telegram and WhatsApp.
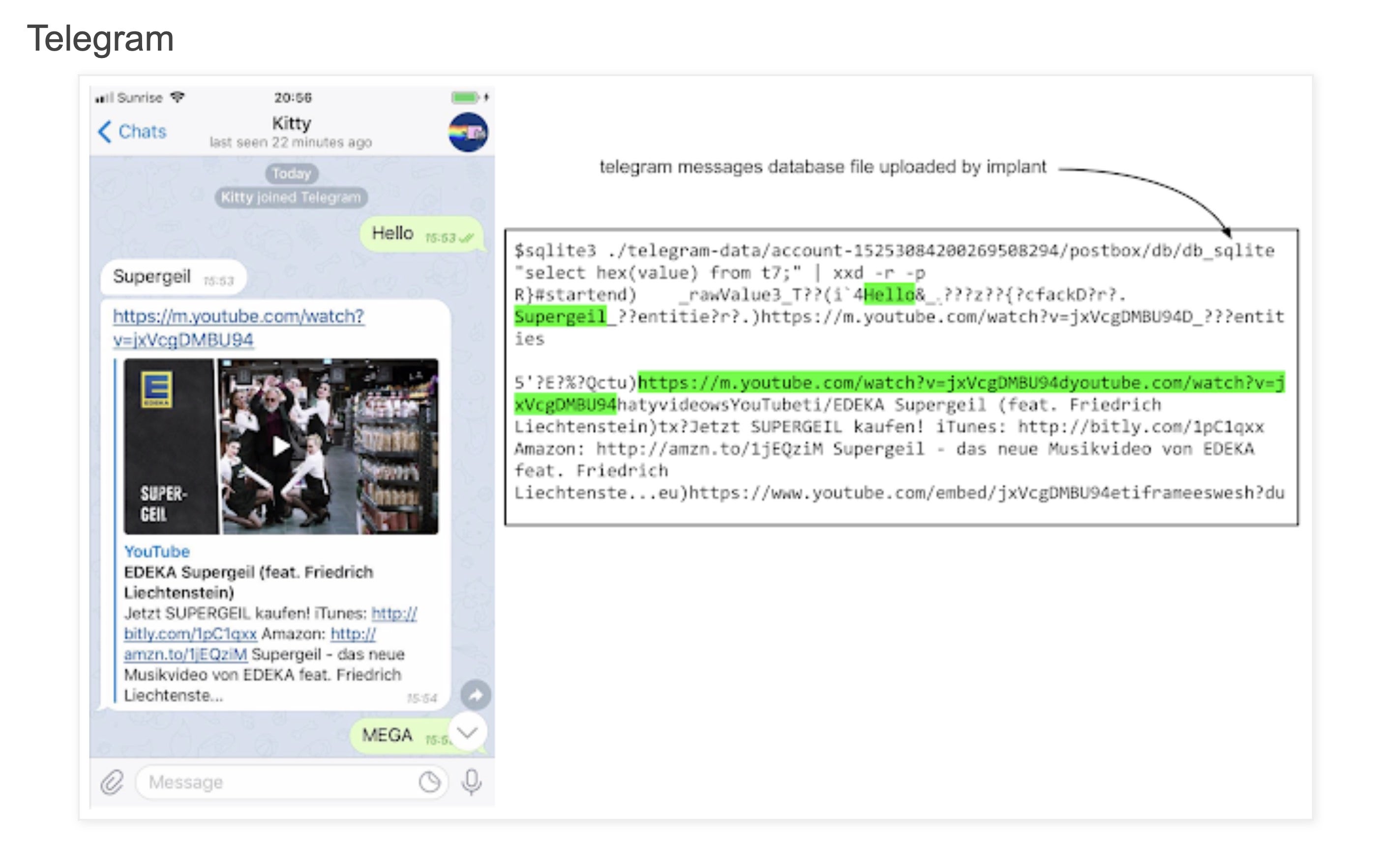
The Project Zero team said it would be almost impossible for users to detect the presence of the malware themselves. While Apple patched the bugs on February 7th, a number of crucial questions remain unanswered.
The Ugly
Cisco scored 10 out of 10 this week, but not in a measure that’s good for either the company or any of its enterprise customers running the widely used IOS XE operating system. CVE-2019-12643 has been rated at the maximum severity of 10 on the Common Vulnerability Scoring System (CVSS). The vulnerability lies in a REST API virtual service container which, fortunately, is disabled by default. However, for clients running the service, malicious HTTP requests could bypass authentication and allow an attacker to login in and execute privileged actions.
Remember the days when the idea of cyber warfare was just the stuff of movies, the overactive imagination of teenage hackers, and a highly guarded state secret that you didn’t talk about and never confirmed? This week the US government discarded the notion of ‘plausible deniability’ and publicly discussed details of a cyber attack on Iranian computer systems used to track shipping movements and target oil tankers in the Persian Gulf. The attack has proved controversial with some defense experts worried that it will only serve to help adversaries learn more about US Cyber Command’s capabilities, while at the same time allowing Iran – and others they choose to share information with – the chance to close those vulnerabilities. Stealth, it seems, was less of a priority in this case than being seen to act. Whether a brazen show of strength was a good or bad idea for US defense interests in the longer term is hard to say. File it under ‘ugly’ and watch this space.

