The Good
The hero of the day is the city of New Bedford, Massachusetts. After (another) typical ransomware attack on a US city (this time, using the Ryuk ransomware) and a ransom request of $5.3 million, the city negotiated it down to $400k, and eventually moved on to recreate their server infrastructure without paying anything to the extortionists. Every paid ransom guarantees another attack. Criminals won’t give up on easy sources of money, and until organizations have proper defenses in place and refuse to give in the attacks will keep coming. So well done New Bedford! Authorities in Flagstaff have also held out against a ransomware attack so far and temporarily closed schools on Thursday while responding to the incident.
The Bad
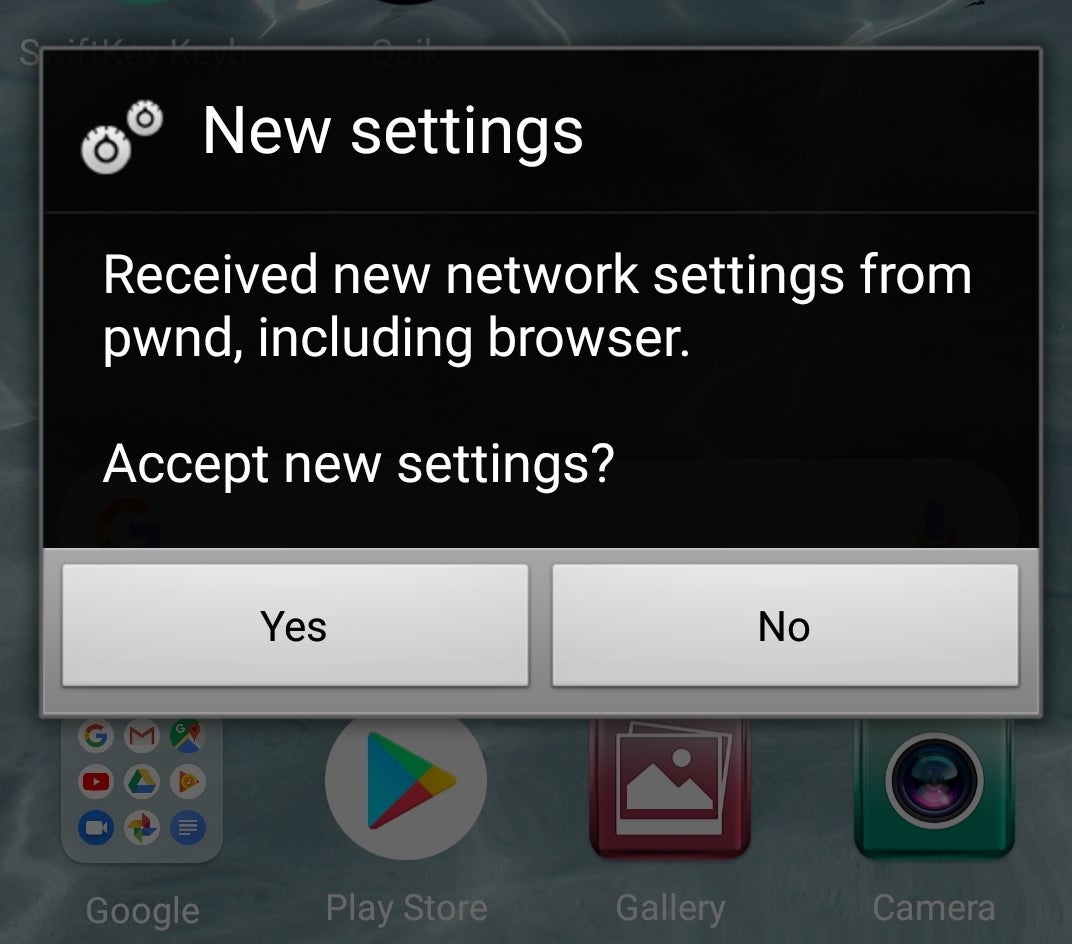
Last week it was iOS, this week it’s Android’s turn. Around 50% of all Android smartphones in use (those from vendors Huawei, LG, Samsung and Sony) allow attackers to easily trick users into changing their phone settings to route internet traffic through a man-in-the-middle proxy. Attackers are able to send over-the-air (OTA) provisioning profiles through phishing messages that can appear to come from the user’s network provider. The provisioning profiles, once installed, allow attackers to change settings for the device’s MMS message server, proxy address, email server and browser homepage, among other things. While Huawei, LG and Samsung have either addressed the issue or plan to, the researchers reported that Sony has refused to acknowledge the vulnerability.
The Ugly
There is nothing worse for a security product than to pave the way for malicious actors to gain entry into enterprise networks. That has happened in the past where Bit9 (later to become CarbonBlack) had their certificate stolen and ended up signing malware used to bypass their own whitelisting product back in 2013. This week, it was revealed that Fortinet and Pulse Secure have been targeted by a Chinese APT5 group seeking to exploit vulnerabilities found in both companies’ products. A Black Hat presentation last month detailed bugs in their SSL VPN implementations. Despite the vendors having patched the vulnerabilities with urgency back in May and issuing a further reminder since the Black Hat conference, some of the 500,000+ organizations affected have left themselves open to attack by failing to keep up and patch in time.