
The Good
Good news for privacy advocates. Rising from the ashes of Mozilla’s twice reincarnated Test Pilot program is a new, privacy-centric, third attempt. First beta out of the door is a desktop extension offering the ‘Firefox Private Network’, aka a free (at least for the time being) VPN to keep your internet surfing away from prying eyes. Anything that helps protect user privacy is always a net good in our eyes.
Following New Bedford’s lead last week, the 22 Texas local governments hit by ransomware last month have disappointed greedy hackers hoping for a $2.5 million payday. The state’s Department of Information Resources say that their coordinated Incident Response plan has been a “tremendous success” and that over half of the “impacted entities” are now operating normally. Tax payers, of course, still have to foot the bill for the state’s valiant recovery efforts, an unsavory fact that only underlines the necessity of having a solution in place to begin with that can detect and block ransomware before it gains a foothold.
The Bad
A newly-discovered Intel side-channel vulnerability allows attackers to send maliciously crafted packets to a target system and spy on encrypted SSH sessions in real-time. The vulnerability requires the victim to be running with RDMA (Remote Direct Memory Access) enabled. Dubbed ‘Network Cache Attack’, or NetCAT (not that netcat), attackers could exploit the flaw to conduct a keystroke timing analysis and predict the text being typed in the SSH session. The researchers estimate such an attack would have an 85% chance of correctly predicting the typed text.
The Ugly
Chromebook users are being warned of a security vulnerability in the Chrome OS’ “built-in security key” feature. If you’ve never heard of it you can probably relax, but the experimental feature is supposed to act as a universal 2nd factor (U2F) security key. U2F security keys are intended to support 2FA by ensuring only someone with a particular physical device can access your accounts. Alas, Google dropped the ball on this one and it turns out that attackers that observe the signature produced by the U2F authenticator can break it to reveal the private key. With that, they could potentially sign in to users website accounts without needing access to the Chrome OS device itself.
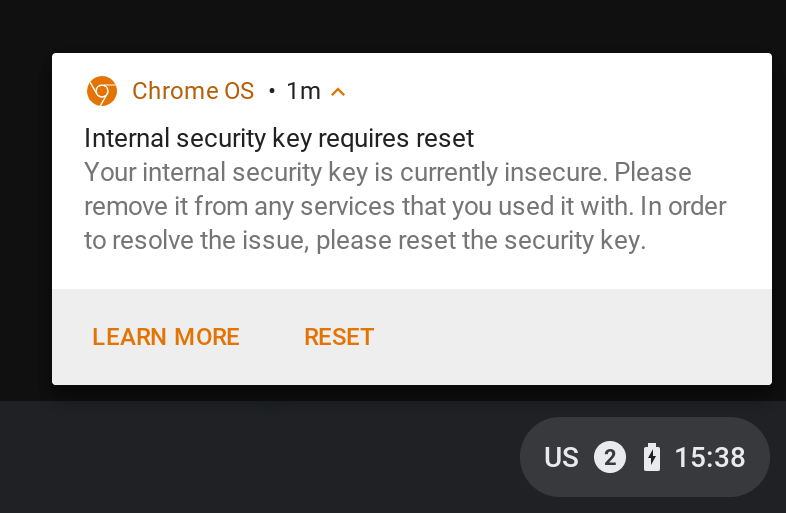
The vulnerability affects 70 different models of Chromebook, and users of the feature are urged to ensure they’re running Chrome OS version 75 or later (which includes an automatic firmware update). Full remediation isn’t pretty, however, and involves a number of steps, as detailed here.

