
The Good
“We have to get over our fear of embracing external experts to help us be secure. We are still carrying cybersecurity procedures from the 1990s.” -Will Roper, Assistant Secretary of the Air Force for acquisition
The US Air Force is quickly changing its philosophy (and reaping great rewards by doing so) by inviting hackers to crack core operational systems and weapons platforms. Initial success was established earlier this year when hackers discovered major mission-critical vulnerabilities in the high-profile F-15 Fighter Jet. This was the first time any outside talent was invited to crack into the TADS and other systems of the aircraft. The immense success of that event, as well as the success it has found in its bug bounty program and Aviation Village at DefCon, brings us to today’s “The Good:” next up is a satellite in orbit, and the ability for hackers to attack the bird or the ground station control systems, in order to uncover vulnerabilities that an otherwise closed development lifecycle simply won’t.

The Bad
A report by Marsh and Microsoft, the “2019 Global Cyber Risk Perception Survey,” brings mostly Bad News: Of all business risks, cyber risks outrank all others by 20%, with 79% of respondents saying it is their top risk, even over today’s economic uncertainty during a trade war and inverted yield curves. That’s Bad…if cybersecurity solutions were effective, it would not be a top concern. But worse, the report shows that confidence in three critical areas of “cyber resilience” declined: 18% said they had no confidence in understanding and assessing cyber risks (up from 9% two years ago), and 19% of leaders had no confidence in preventing cyber threats (up 7% from before). Worst of all, 2 out of 10 respondents said they had no confidence in their organization’s ability to respond and recover from cyber events like ransomware, fast-moving worms, sensitive data breaches, etc.
Question: Of the following business threats, please rank the top 5 that are the biggest concerns to your organization:
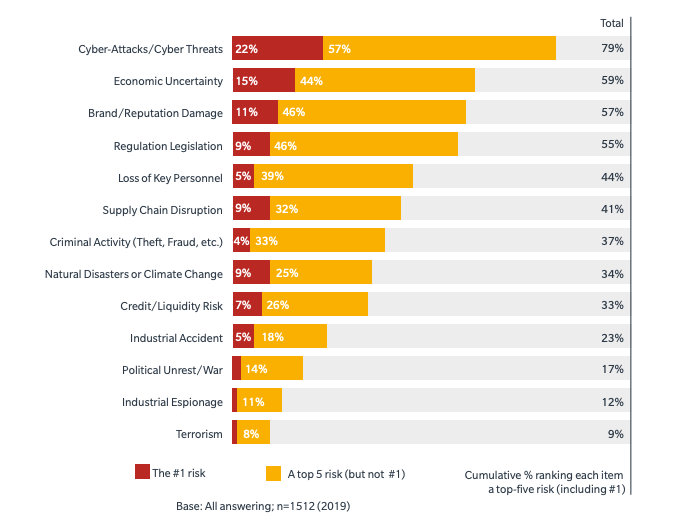
Simply put: Because legacy controls and a focus on ‘resilience’ over prevention have not been working these last 4-5 years (getting worse in fact), the C-suite is more worried than ever about cyber risk to the business, life/safety, brand/reputation, and mission.
The Ugly
The same folks that sponsored The Bad were broken by themselves: Microsoft. This time we have a Microsoft patch that broke the ability for Microsoft to perform manual or scheduled Microsoft Defender scans on the Microsoft OS. But more ironic than that? The patch was needed because Microsoft System File Checker (SFC), which had been broken since early this summer, was flagging internal Microsoft Windows PowerShell files within Microsoft Defender as malformed. Some in the community point out that Microsoft keeps breaking things when they try to fix them…but they are missing the point: Using Microsoft components that depend on Microsoft components to secure Microsoft components is like asking your foot doctor to perform brain surgery using his foot, upon himself. It’s never been a good idea. It never will be, and the manifestations of this very bad idea will play out in real life indefinitely, and by design. This is not a philosophical conundrum, this is just the entropy of complex, self-referencing, self-authored, self-conflicted software playing out as it must.
Oh look… #WindowsUpdate strikes again. The CPU spikes, the battery drain issues, and a few other things from the last month still haven’t been cleaned up and now this… #Win10 stick a fork in it…https://t.co/yPxwE3bm9J
— Jason Falter ⚔️ (@JasonFalter) September 18, 2019

