The Good
This week, British national Nathan Wyatt received a sentence of five years in prison, along with a hefty fine, in connection with multiple breaches and operations attributed to the “The Dark Overlord” hacking group.
Wyatt, a 39 year old, held a pivotal role in numerous malicious campaigns carried out by TDO (The Dark Overlord). This result has been a long-time coming as Wyatt was taken into custody in 2017, and finally extradited to the United States in December of 2019. Lengthy legal documents, filed in 2017, detail many of the specific offenses, along with some of the related methodologies.

The court documents offer an inside look at a tactic that has become all-too commonplace in recent times. Wyatt, along with others in the TDO team, would attack high-value targets, exfiltrate swaths of valuable data, and then demand a ransom in return for not leaking the stolen data to the public. If victims failed to meet the demands, the TDO would leak breach details to the media, post the data for sale in hacker forums, or simply post it for all to see on the web.
One of Wyatt’s main responsibilities was to broker communications between the victims and TDO. Wyatt would register unique phone numbers and accounts and use those channels to communicate with victims to demand the ransom or negotiate where required.
The TDO have been linked to a large number of high-profile campaigns against Netflix, ABC, SMART, Gorilla Glue, and many others, so it’s pleasing to see the legal system catch up to these actors. Wyatt’s criminal endeavours cost him five years behind bars and nearly 1.5 million USD in fines.
The Bad
This week, CISA (US CERT Cybersecurity & Infrastructure Security Agency) released Alert AA20-266A. The agency has noticed a sizeable uptick in the distribution of LokiBot commodity malware, via their EINSTEIN IDS system, starting in July 2020.
LokiBot is a widely available tool, with nearly no barrier to entry for setup and use. This makes the framework very attractive to enterprising cybercriminals that lack the skills to create or manage more complex malware or the resources to buy into a more expensive toolset. Generally speaking, LokiBot contains keylogging, backdoor/remote access features, browser-based credential harvesting and information stealing features. It can also be used as a loader or dropper for additional code or malware.
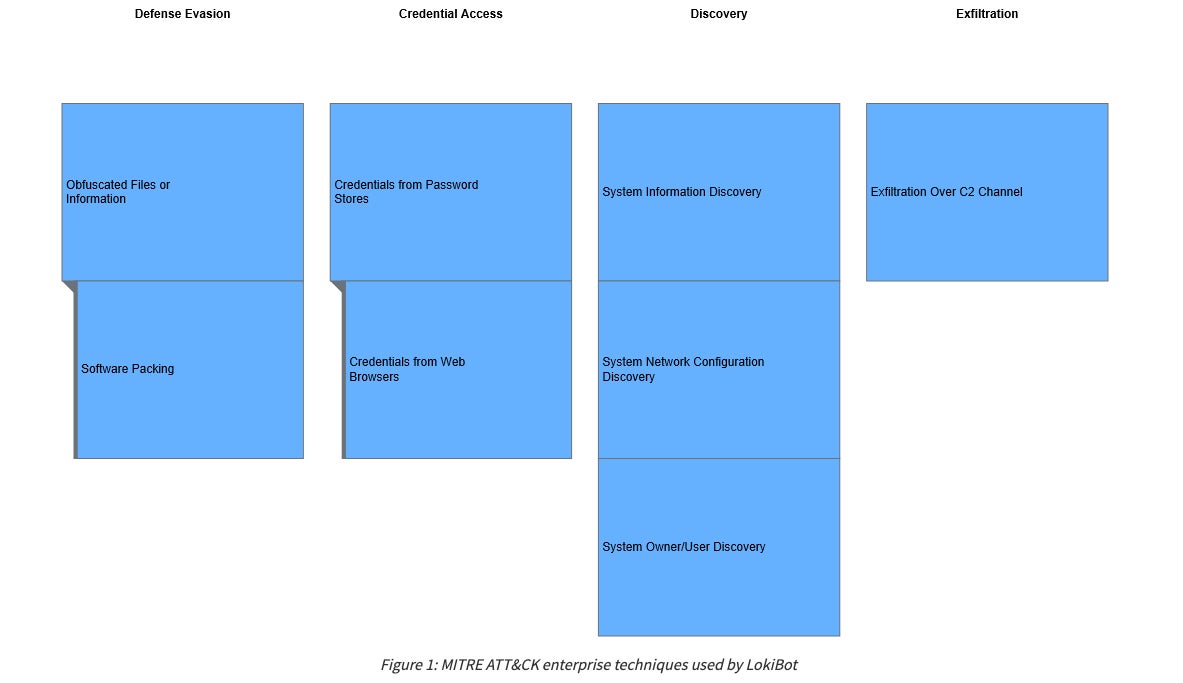
While LokiBot is well-known, well-documented, and generally well-defended against, this week’s alert is a good reminder that even the less-sophisticated malware families will ebb and flow in use and effectiveness. There is never a time when we, as “cyber-defenders”, can let our guard down. We encourage all to have a look at CISA’s guidance and use this as an opportunity to review your security posture and make any changes needed to ensure protection against LokiBot and all the other nasty bits out there in the wild.
The Ugly
As we inch closer to the upcoming election in the United States, sensitivity around election security is at an all time high, and you know that things are taking a turn towards the ugly when when an election-related entity is targeted with ransomware. Tyler Technologies, a company which provides services to the United States government, recently reported that it was hit with a damaging ransomware infection.
Tyler Technologies’ services to the U.S. government include emergency management, disaster recovery assistance, and the collection and sharing of election data. The company describes itself as a “Leading provider of end-to-end information management solutions and services for local governments.”
Given the current modus operandi of ransomware actors is to leak victim data if the target fails to pay up, this ransomware attack is even more concerning. Current details suggest that the specific ransomware family was RansomExx. Tyler Technologies has indicated that no “personal data” was affected or accessed, and that the attack was limited to their internal corporate network. However, investigation into the matter is ongoing, and new details may emerge in the coming days and weeks.
Meanwhile, the company issued the following statement to their clients via email:
We are certain that more stories like this will crop up as we approach the November election. Now, more than ever, trusted security controls are critical to protect the systems and data that we all rely upon and need to inherently trust.


