The Good
As we’ve noted before, the proliferation of ransomware is predicated on, among other things, the use of cryptocurrencies to facilitate the ease of criminals to receive payment and launder their profits. So we were delighted to learn this week that the U.S. Treasury Department has taken the step of sanctioning a cryptocurrency exchange for its role in laundering cyber ransoms for groups such as Ryuk, Conti, and Maze.
SUEX OTC, S.R.O. (aka “SUCCESSFUL EXCHANGE”) was added to the Office of Foreign Assets Control’s (OFAC) list of specially designated nationals on Tuesday. The designation prevents any U.S. person or business from engaging in transactions with SUEX and blocks all SUEX assets that are subject to U.S. jurisdiction. Organizations that engage in transactions with SUEX could also face sanctions or be subject to enforcement action. Ransomware victims should be especially careful to note that they could face potential sanctions for facilitating a ransomware payment to a sanctioned entity, and OFAC has updated its guidance on this as well.
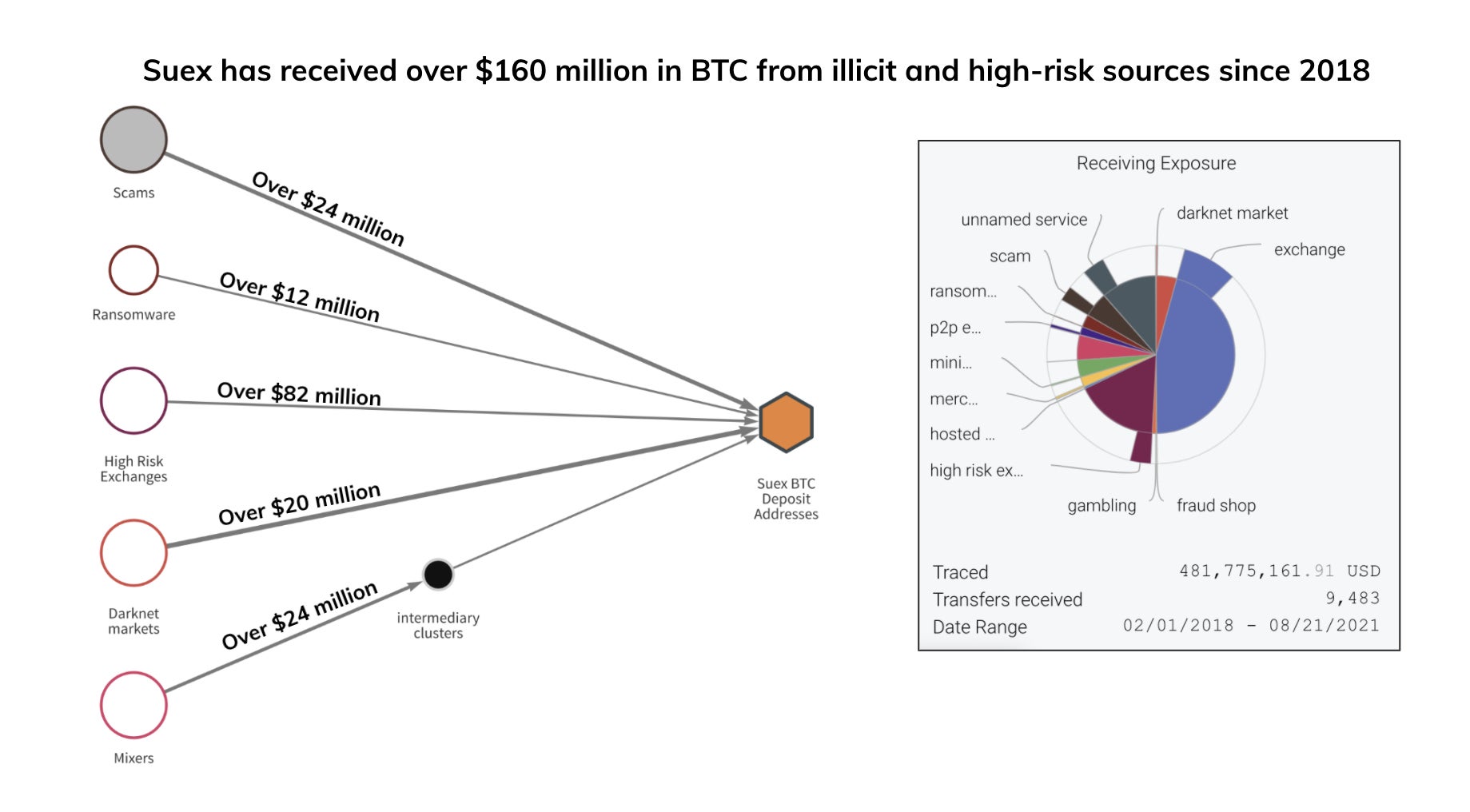
According to analysts, SUEX has received over $160 million in bitcoin from “illicit and high-risk sources” since 2018. Of that, $13 million is estimated to come from ransomware operators like Ryuk, Conti and Maze, $20 million from darknet markets, $24 million from scam operators, and $50 million from the illicit cryptocurrency exchange BTC-e, itself shut down in 2017 for laundering money for cybercriminals. The sanction against SUEX is a welcome step in cutting off cybercriminals’ access to easy payments. Let’s hope there’s more to come.
The Bad
Last week saw the beginning of a tough period for Apple with the FORCEDENTRY (aka CVE-2021-30860) exploit. Things have gone from bad to worse since then.
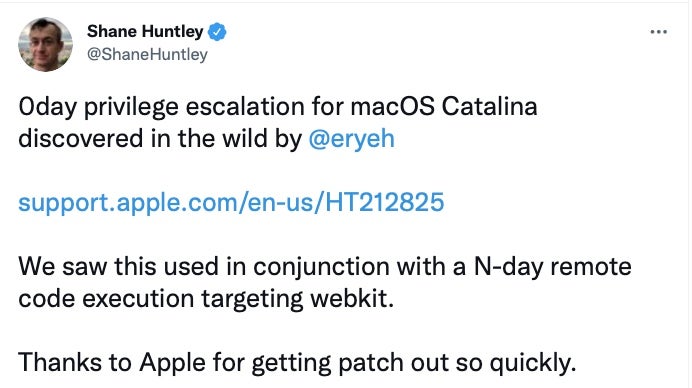
Thursday saw Apple back port a fix for FORCEDENTRY to iOS 12.5.4. It also released a patch for an entirely different zero-day (CVE-2021-30869) on macOS Catalina with the warning that the company was aware of an exploit in the wild leveraging the privilege escalation in the XNU kernel.
Earlier in the week, a researcher dropped an interesting-but-not-particularly dangerous macOS vulnerability that allows the unexpected execution of other files on the system.
A file with the .inetloc, .fileloc, .webloc, or .url extension can launch other executables on the system when double-clicked without first asking permission from the user.
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>URL</key>
<string>FiLe:////////////////////////System/Applications/Calculator.app</string>
</dict>
</plist>
Reports that this could lead to remote code execution, however, were a little wide of the mark. The technique cannot be used to execute embedded code, though it could potentially be used to launch other files passed to the victim by an attacker. Such files themselves, however, could still trip over Gatekeeper, depending on the circumstances. Unconfirmed reports suggest the same researcher may have other, related bugs to reveal, so stay tuned for more on that.
Of more immediate concern, particularly to iOS users, was a raft of zero days published this week expressly because the researcher felt that Apple had not acted fairly or transparently to his attempts at responsible disclosure. Some of these exploits allow an application to escape sandboxing and read potentially sensitive data from Mail, Health, and other apps.
Rounding out the week’s dire security news for the Cupertino company, a Spanish iOS researcher dropped yet another (albeit, minor) zero day citing similar reasons of disenchantment with Apple’s treatment of his bug bounty submissions.
All in all, quite a week of bad news for Apple and its customers. Let’s hope that relations between the company and security researchers take a turn for the better going forward.
The Ugly
More details have emerged around the story we reported on last week regarding REvil’s reemergence and the appearance of a universal decryptor for previous victims. It’s a story that brings into sharp relief the challenges faced by both law enforcement and victims when dealing with the ransomware threat.
According to a report, mitigation for the recent mass-scale ransomware campaign conducted by REvil against Kaseya and its clients was deliberately delayed by the FBI. The agency reportedly secretly acquired a universal decryptor but held onto it for three weeks rather than giving it to victims.
The FBI had hoped to conduct an operation that would disrupt or take down the REvil gang and did not want to reveal their hand by exposing their possession of the key. For three weeks, many victims including schools and hospitals struggled with the effects of the ransomware, and all told businesses incurred millions of dollars in losses.
Balancing the immediate needs of victims against the longer-term payoff of putting a crimeware gang out of action is obviously a tough call, but it gets tougher when the strategy turns out to have been a flop.

By the time the FBI were ready to put their plan into action, the REvil gang had already done a disappearing act and the operation was no longer viable.
Strange coincidence or were the FBI’s operational plans themselves leaked by a hack? We’ll likely never know, but the end result is that the REvil gang is back in town, the FBI’s plan came to nothing, and a lot of victims are feeling the pain. Let’s hope the good guys have better luck next time.