The Good
US politics is deeply divided, but at least both sides of the aisle agree on one thing: cybercrime needs to be tackled in an urgent and coordinated fashion. So it’s good news that on Jan 17th, Congress proposed the bipartisan “Cybersecurity State Coordinator Act of 2020” bill. If passed, it would allow for the appointment of 50 employees (one for each state) to join CISA, the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency. Each employee would function as a cybersecurity state coordinator, allowing them to facilitate between federal and non-federal agencies in various capacities such as providing federal cybersecurity risk advice, being a principle point of contact during cyber incidents, and acting as a strategic facilitator. Key responsibilities would include helping organizations to plan for and manage the development of cybersecurity infrastructure, promoting the sharing of threat intel and federal cyber resources to non-federal entities as well as supporting training, exercises, and remediation efforts related to cybersecurity risks and incidents.
The bill is a step in the right direction. Instead of hitting agencies with another “stick” in the form of more regulation and penalties for failing to secure data and services, this is more of a “carrot” – offering much-needed practical help to state and local governments, schools, hospitals and other organizations that are currently struggling to keep up with the cyber onslaught.
The Bad
All data breaches are bad, but to paraphrase Tolstoy, “Each data breach is miserable in its own way”. But then there are some data breaches that eclipse anything else we know. Such a data breach was made public this week, by none other than Microsoft.
In a blog post, the OS maker said that an internal customer support database that was storing anonymized user analytics was accidentally exposed online without proper protections between December 5th and 31st. The result was the exposure of 14 years’ of customer support logs, containing 250 million records, with information such as email addresses, IP addresses, and support case details. Microsoft said that most of the records didn’t contain any personal user information. The misconfigured servers were exposed to the internet for 25 days before being identified and closed. The researchers who found the servers said that the data could be valuable to tech support scammers, in particular those that pretend to be Microsoft support representatives. Microsoft did act promptly and fixed things within two days of notification. However, this incident highlights that even extremely proficient organizations still struggle with cloud configuration and security.
The Ugly
The big ugly story this week involves Amazon, but in this case the online retail giant, or more accurately its founder and CEO Jeff Bezos, is the victim rather than the perpetrator. The UK’s Guardian newspaper learned that Bezos’ iPhone was apparently hacked in May 2018 via malware hidden in an mp4 file that was sent to Bezos in a WhatsApp message. And what has really caused an ugly cyberstorm around this story is that the message was allegedly sent to Bezos by Saudi Arabia’s crown prince Mohammed bin Salman.
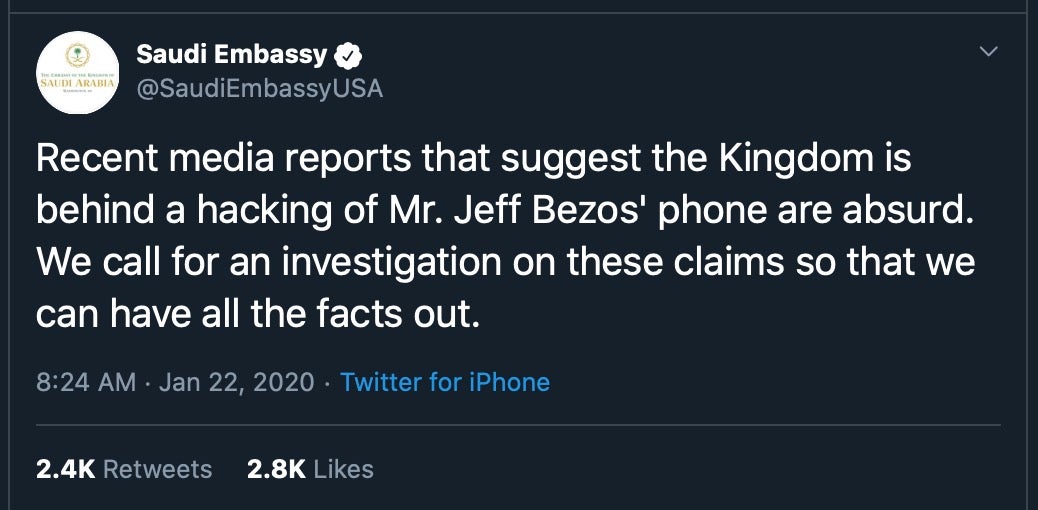
While the Saudi embassy has naturally denied the claims, calling the accusations ‘absurd’, the researchers who conducted the analysis on the Amazon CEO’s iPhone said it was “highly probable” that the malware had come from an infected video file sent from the account of the crown prince. Within hours of the malware infection, large amounts of personal data from Bezos’ phone were exfiltrated, presumably uploaded to servers controlled by the malware authors.
As for the motive for such a highly personal attack, speculation revolves around the fact that Bezos also owns the Washington Post. Saudi Arabia has long been disgruntled at stories in the Post critical of the country’s human rights record, and there are suggestions it may have hoped to use the stolen data to gain leverage for more favorable press coverage. The Post was, of course, also the employer of the murdered Saudi journalist Jamal Khashoggi. There’s plenty more intrigue to this story, we’re sure, and we’d all definitely like to know more about the malware used in the attack. In the meantime, be careful who you chat with and beware unsolicited mp4 files!