The Good
Cyber hygiene within the education sector is often overlooked when the spotlight frequently shines on attacks against high-profile enterprise targets, but the devices and networks used by our schools, teachers and students are nevertheless popular targets for criminals. Good news, then, that an individual responsible for hacking into 25 school network email accounts has pleaded guilty in Philadelphia this week.
Timothy Spillane, 39, admitted to setting up fraudulent email and bank accounts in his victims’ names after breaching the digital networks of two Philadelphia colleges. The attacker had hoped to conduct an elaborate tax fraud scheme using stolen student financial information, but he failed when he was unable to guess the victims’ adjusted gross income from the previous tax year.
The FBI had received a tip about Spillane’s activity, which spanned November 2017 to January 2018, and conducted a search warrant and arrest at his home after a short investigation. Sentencing has yet to be determined.
Meanwhile, DeepDotWeb co-owner and operator Tal Prihar, who pleaded guilty to money laundering last March, was sentenced to over 8 years jail time this week. Prihar and co-defendant Michael Phan earned over $8 million in kickbacks from purchases of contraband on darknet marketplaces.
The Bad
This week’s ransomware tales show just how ubiquitous the problem is for everyone connected to the internet, whether it’s a lone MIT professor in the U.S. or a multi billion dollar company in Taiwan, ransomware operators are out there encrypting files and demanding pay days.
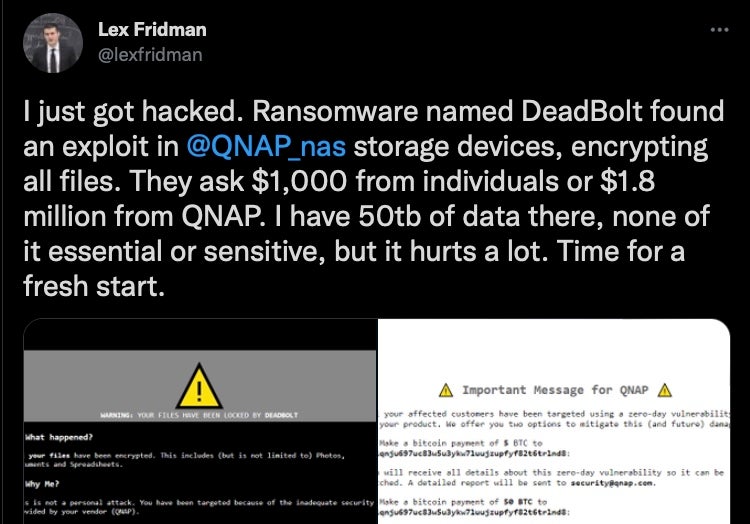
Thousands of individual QNAP users were hit this week with ‘Deadbolt’ ransomware. The Taiwanese NAS backup and storage device maker was itself asked to pay a ransom for information about the alleged “zero day” exploit used in the attack. However, given the details that have emerged so far, it’s likely that the operators had instead based their targeting on scanning the internet for misconfigured devices that could be accessed from the internet without authentication. In any case, there was no shortage of victims, who were told they needed to pay 0.3 in Bitcoin. At least one reported that, having paid the ransom, they did not receive the promised decryption key.
At the other end of the scale, a reported attack by the Conti ransomware gang struck at another Taiwanese company this week, Delta Electronics. Delta, which serves as a contractor to both Apple and Tesla, was asked to pay a $15 million ransom by the gang, which claimed to have encrypted around a fifth of the company’s estimated 65,000 endpoints.
Although Delta have said no production systems were impacted, other reports suggest that the company has yet to restore most of the affected systems, with the company using an alternative web server while its official sites remain down.
The Ugly
It’s been a busy and not particularly pretty week for anyone involved with Apple security. The week began with news of OSX.DazzleSpy, a backdoor RAT that appears to be related to macOS.Macma and a watering-hole attack against Hong Kong Pro-Democracy activists. Then, the Cupertino device-maker was forced into pushing patches across its platforms for a number of bugs, some of which, the company said, were being actively exploited in the wild.
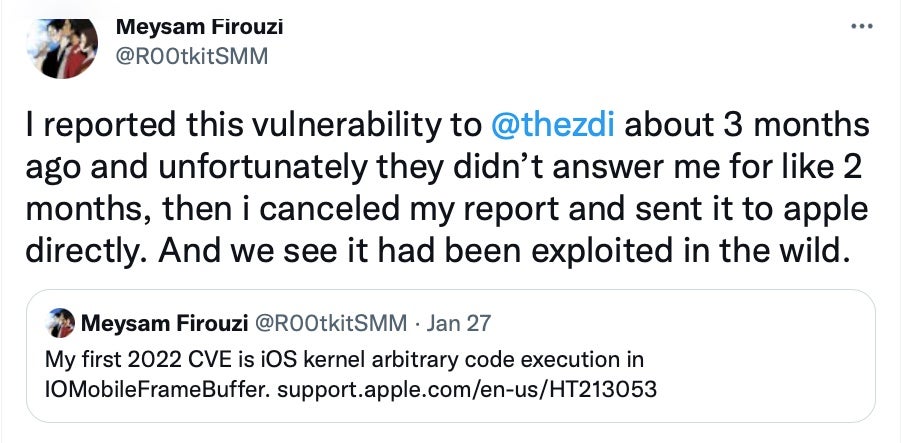
Among the vulnerabilities patched is an iOS bug that was first reported to 3rd-party vendor Trend Micro’s “Zero-Day Initiative” and apparently sat on for two months. By the time the researcher reported it directly to Apple in frustration at the lack of action, it had already been exploited in the wild.
Meanwhile, a bug in PackageKit that could allow a privileged attacker to bypass macOS’s System Integrity Protection, CVE-2022-22583, was patched and jointly credited to several different researchers. According to one analysis, an attacker could bypass SIP by abusing post-install scripts run by .pkg files and mounting an image onto /private/tmp, which is not itself protected by SIP.
This would allow the attacker to swap the SIP-entitled legitimate script run by the installer from a subdirectory in /private/tmp for one supplied by the attacker. Apple fixed the flaw by moving the location of installer scripts to a subfolder in the SIP-protected /Library folder.
CVE-2022-22583 builds on the Shrootless vulnerability reported previously by Microsoft as CVE-2021-30892. While it will undoubtedly cause concerns, it is unlikely to be exploited in the wild. As with Shrootless, exploiting this vulnerability requires the attacker to already have elevated privileges, and the use case for bypassing SIP from that vantage point is difficult to see. Stealthier persistence deep in the bowels of the system would be one, but modern versions of macOS with signed system volume (SSV) protection would likely notice any tampering there as soon as the system was rebooted, undermining the investment in stealth.
That said, there are plenty of other flaws addressed in the patches released by Apple this week, and users are strongly urged to update all their fruity devices.