
The Good
What do Mirai, Hakai, Fbot, and Tsunami have in common? Answer…they are all primarily IoT-based malware variants and all were part of a large-scale DDoS botnet takedown this week spearheaded by Dutch police.

The primary target of the operation was KV Solutions BV, a “bulletproof” hosting provider. Current reports indicate that for at least two years, KV Solutions was harboring criminal activity and playing host to numerous DDoS attack operations, and facilitating their ongoing success. A majority of the activity was Mirai-based, and targeting devices from ZTE, MikroTik, JAWS, Huawei, GPON, ASUS, Netgear and others. Outside of Mirai, and close derivatives, additional malware families were tracked as well. These include Tsunami, Gafgyt, Fbot, Moobot, Yowai, Hakai, and Handymanny. At any given time, some of these operations were supported by tens of thousands of hosts (bots). The activity tracked within KV”s infrastructure was not limited to “private” use. Many of the actors associated with this activity would sell access to their botnets for DDoS “for hire” services. During the raid, two individuals were arrested, those being “Angelo K”. and “Marco B.” aka the registered owners of KV Solutions BV. All associated sites and servers have been fully seized and taken down at this time. These types of takedowns are a combined effort of individuals across the law enforcement and security industry communities. They also take a great deal of careful effort, and huge swaths of time and dedication from all involved.

This week the NSA launched their Cybersecurity Directorate. We previewed this program in a previous post, when it was originally announced in July 2019. According to the NSA,
“The Cybersecurity Directorate will reinvigorate NSA’s white hat mission by sharing critical threat information and collaborating with partners and customers to better equip them to defend against malicious cyber activity. The new directorate will also better position NSA to operationalize its threat intelligence, vulnerability assessments, and cyberdefense expertise by integrating these efforts to deliver prioritized outcomes.”
This effort should result in improved and more secure methods of sharing information between the NSA and their trusted partners (public and private).
The Bad
Early this week, multiple hospitals, between Alabama and Australia, were targeted by crippling ransomware attacks. Perhaps hardest hit were three DCH Health System hospitals in Alabama. All three of these entities were forced to turn away new patients as a result of the attack. First responders and private citizens alike were directed to alternate facilities after the ransomware took hold. It is reported that affected systems were still locked and impacted well past the 24-hour mark post-infection. Current intelligence indicates that the malware involved was Ryuk, which has played a role in several similar attacks recently. Other very prevalent malware families (Emotet, Trickbot) are also known to be used as a delivery mechanism for Ryuk. DCH was quick to alert the public once the attack was underway. Their first public statement noted that “A criminal is limiting our ability to use our computer systems in exchange for an as-yet unknown payment,”
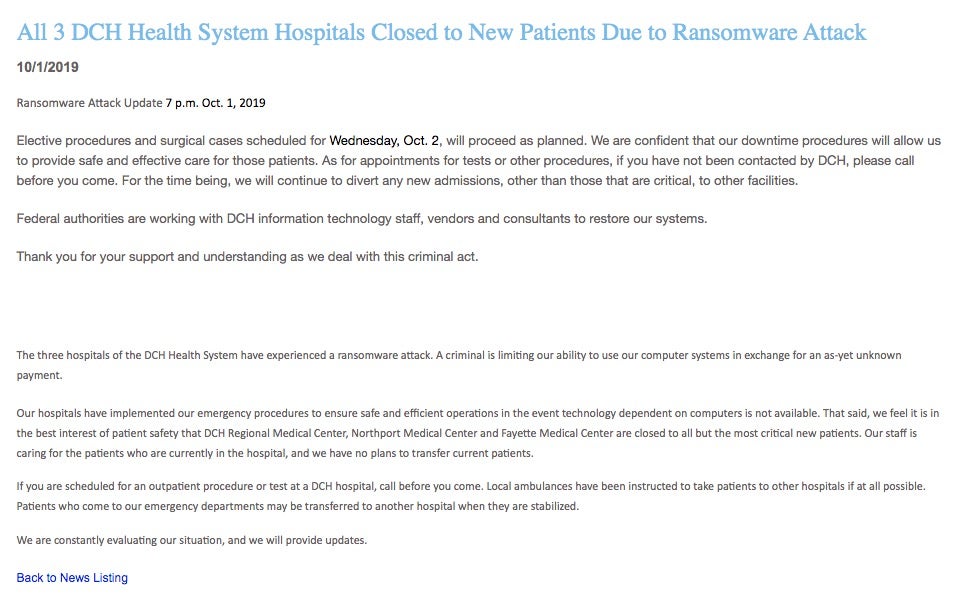
On October 2nd, the following update was issued:
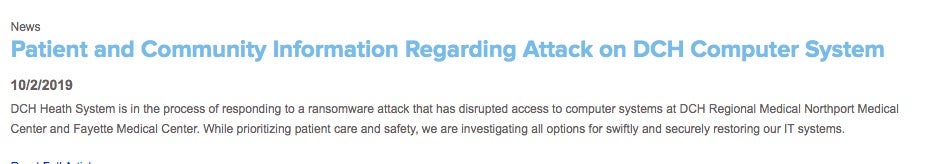
This whole episode serves as yet another reminder of how critical a proper protection strategy is.
The Ugly
It has been an interesting week for the Infosec industry as a whole. For starters, we have reports of FireEye considering a possible sale to a private equity firm. It’s too early to speculate on a possible outcome, but it does make a certain “statement” about the goals and strategy for FireEye going forward. Is the goal there to protect customers, or to ensure ongoing financial windfalls for the executive staff?
And in another corner…we have CrowdStrike. Their latest issue is actually separate from their being entangled in recent political issues. CrowdStrike was recently forced to revoke Windows sensor version 5.19.10101 from their Falcon update servers. Numerous customers, world-wide, reported Blue Screen of Death (BSOD) errors following the update to this new version. While root cause has not been fully identified (as of this writing) there are some reports that indicate a conflict with another vendor”s DLP product.
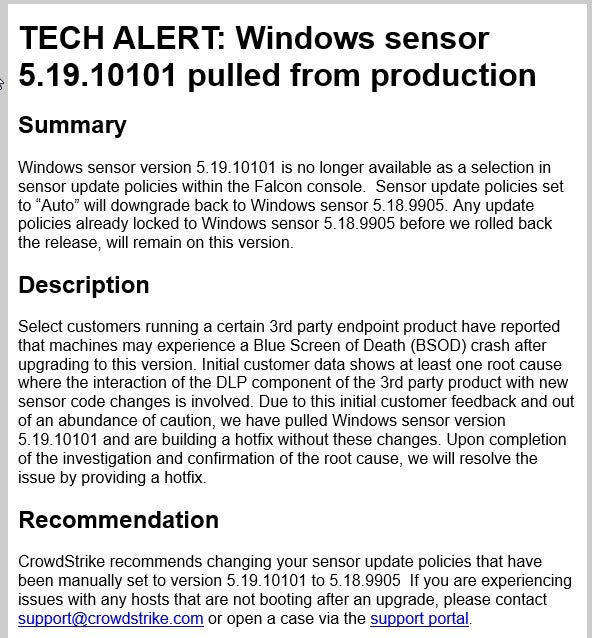
When issues like this occur, we can all be reminded of the importance of tiered or staged rollouts of critical software updates. Or better yet, in the case of security products…embrace technology that does not require frequent updates that negatively impact business.

