The Good
Ask a security professional about the weakest link in any organization and the answer most commonly received is: users. A lack of awareness regarding threats as well as poor or absent cyber hygiene practices mean that phishing and social engineering are a threat actor’s favorite play.
It may come as a welcome surprise, then, to learn that according to a new survey, there’s been a marked improvement in cybersecurity awareness among the general public over the last three years. Coming after the pandemic and the large-scale shift to work from home, that can only be good news for enterprise security teams.
The survey found that in 2022, some 77% of respondents said they use MFA to log into online accounts compared to only 50% in 2019. An encouraging 88% said they now use strong passwords, up 12% from three years ago. In 2019, some 31% of people said they did not use any kind of security feature to unlock their smartphones. That number is down to 15% in 2022.
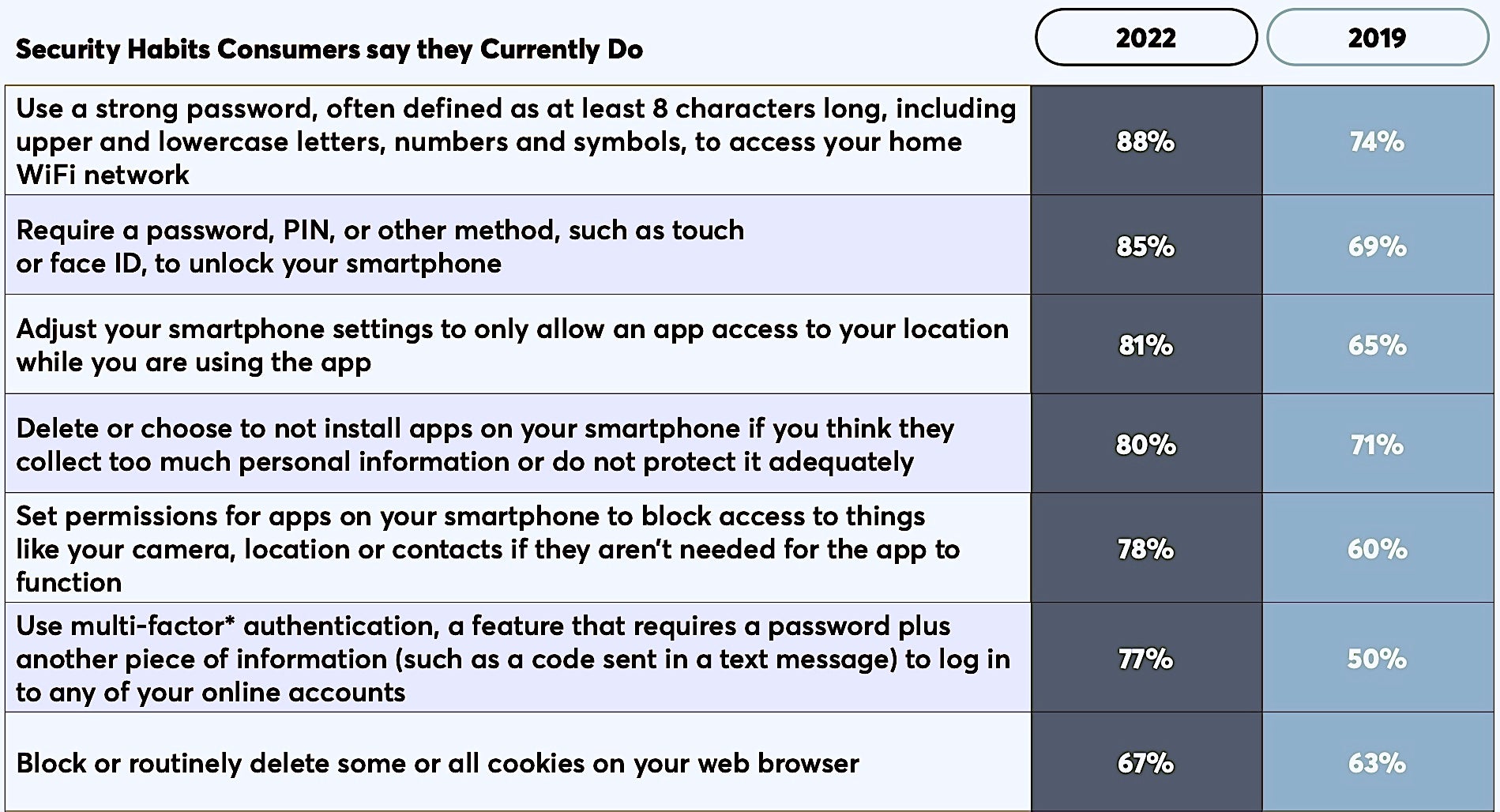
What accounts for this rise in cybersecurity awareness? The report suggests that the coverage of cybersecurity issues and emerging digital threats in the media, the increase in data breaches, and the growing awareness of ‘cookies’ and third-party trackers on personal devices are all likely to have contributed to the general perception that cybersecurity is an issue that affects all of us, at home and at work.
The Bad
If it’s good news we’re all becoming more cyber aware, on the other side of the fence is the unwelcome news that threat actors are making it easier to create and conduct phishing campaigns with a new PhaaS (Phishing-as-a-Service) platform called Caffeine. While PhaaS’s are not an entirely new phenomenon, what makes Caffeine particularly troubling is that anyone can sign up for it on the public internet.
Typically, threat actors wanting to use a PhaaS need a recommendation from a current customer or must go through some kind of vetting process. Caffeine is a site hosted on the public internet which accepts applications from anyone with just an email address, researchers say. For as little as $250/month, subscribers can use the platform to create customized phishing kits, generate URLs to host malware payloads, and track their campaign’s progress.
Caffeine significantly lowers the barrier to entry to would-be threat actors, offering to take care of infrastructure, fake sign-in pages, website hosting, email templates and more. The service currently targets the theft of Microsoft 365 credentials via fake sign-in pages hosted on compromised WordPress sites. Researchers say they expect to see the service expand its targets as it develops.
With competing PhaaS offerings advertising services such as 2FA and MFA bypasses, it seems that threat actors have a wealth of easy options for getting new campaigns off the ground.
Whether Caffeine’s open registration and appearance on the public internet will survive scrutiny from security researchers and law enforcement remains to be seen, but even if the service eventually retreats underground, the onus is on users and security teams to bolster their defenses. The emergence of services like these is only likely to increase the already high volume of phishing attacks being seen by enterprise security teams.
The Ugly
Last week, Fortinet issued a private warning to its customers of a new authentication bypass flaw affecting its FortiOS, FortiProxy and FortiSwitchManager products. This week comes the unpleasant but not entirely unexpected news that the flaw, tracked as CVE-2022-40684, is being actively exploited in the wild.
The critical flaw allows an unauthenticated attacker to perform arbitrary operations on the products’ admin interface after sending maliciously-crafted HTTPS requests. These operations include modifying admin user’s SSH keys, adding new local users, updating network configurations to reroute traffic, and initiating packet captures.
Exploit available for critical Fortinet auth bypass bug, patch now – @sergheihttps://t.co/oqceLu6YeP
— BleepingComputer (@BleepinComputer) October 13, 2022
CISA has added the bug to its database of Known Exploited Vulnerabilities (KEV), and FortiNet has advised organizations to hunt for the following IoC in device logs:
user=”Local_Process_Access”
In addition, those using the affected products should apply the available patches without delay. For those that cannot patch, Fortinet is advising admins to disable HTTP/HTTPS administrative interface or limit the range of IPs allowed to reach it.
In other bug-related news, Microsoft’s monthly ‘Patch Tuesday’ failed to offer fixes for the recently reported Exchange Server vulnerabilities commonly-known as ProxyNotShell but did fix 13 other critical flaws that could allow for privilege escalation, spoofing and remote code execution. Three critical RCEs affect Microsoft Office and Word. As always, Microsoft users are urged to patch at the earliest opportunity.


