The Good
This week, the U.S. government took a further step in its crackdown on cybercrime by introducing a ban on the export of “cybersecurity items” without a license. The new controls announced by the Commerce Department’s Bureau of Industry and Security (BIS) effectively prohibit U.S. companies from selling hardware or software that could be used in cyberattacks.
Tools that could be used for surveillance, espionage, malicious cyber activities or human rights abuse are now banned from export or resale unless permission is acquired via the new License Exception Authorized Cybersecurity Exports (ACE).
The BIS said that the new rules would help ensure that U.S. companies were “not fueling authoritarian practices”, while Gina M. Raimondo, U.S. Secretary of Commerce, said the rule was intended to block malicious threat actors accessing tools that could be used against the U.S. or its allies.
In another blow to the bad guys, RICO charges put two cybercriminals behind bars after they were convicted of aiding cybercrime with so-called bulletproof hosting services. Operators of Zeus, SpyEye, Citadel and the Blackhole Exploit Kit had rented infrastructure from the pair for use in a variety of cybercrimes, from running botnets to stealing banking credentials. Pavel Stassi and Aleksandr Skorodumov were sentenced to two and four years jail time, respectively. Two other men, Aleksandr Grichishkin and Andrei Skvortsov, were also indicted in the same case and, if brought to justice, could each face 20 years in prison.
The Bad
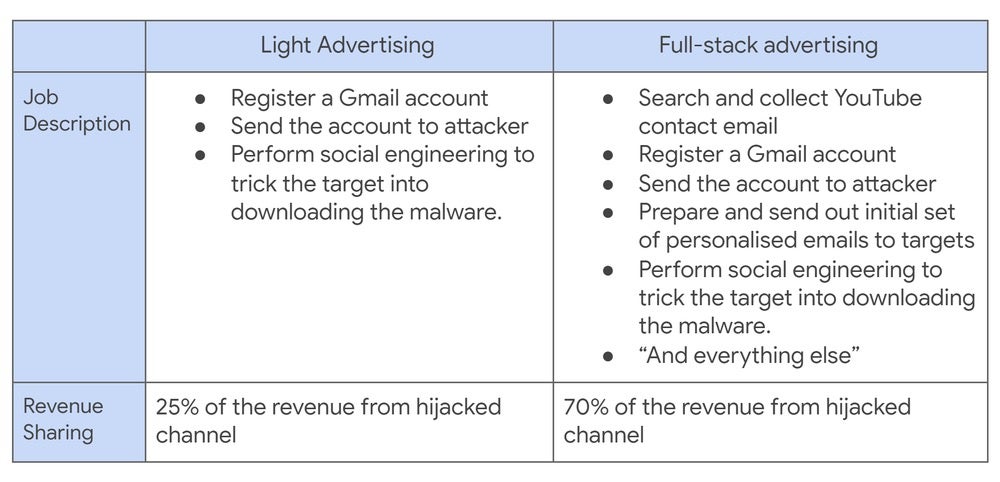
Cookie theft, phishing, and hackers-for-hire are all part-and-parcel of this week’s bad news in which thousands of high-profile YouTube accounts have been targeted by hackers running cryptocurrency scams.
Profitable creator channels on YouTube have been targeted by hijackers since at least 2019, according to Google, owners of the video-sharing platform. The account takeovers were targeted so that the attackers could run cryptocurrency scams not unlike those we saw on Twitter last year. However, there was a marked ramp-up of attacks over the last two years, with the scammers switching tactics to avoid Google’s attempts to detect the attacks.
The general MO involved sending a phishing email to a target offering a business opportunity, typically asking the target to test and review some product, like an AV suite. The target was then sent malware from one of over 1000 malicious domains, with the aim of running cookie-stealing malware on the victim’s machine.
Unusually, the attackers rarely bothered with persistence methods, both to avoid detection and because once the target’s cookies had been stolen, the thieves could take over their social media accounts without further action.
According to the report, the perpetrators were largely ‘hackers-for-hire’ recruited on Russian-speaking forums.
Google has offered several pieces of common-sense advice for avoiding these kinds of attacks, including enabling MFA, using security software, and turning on safe-browsing protections.
The Ugly
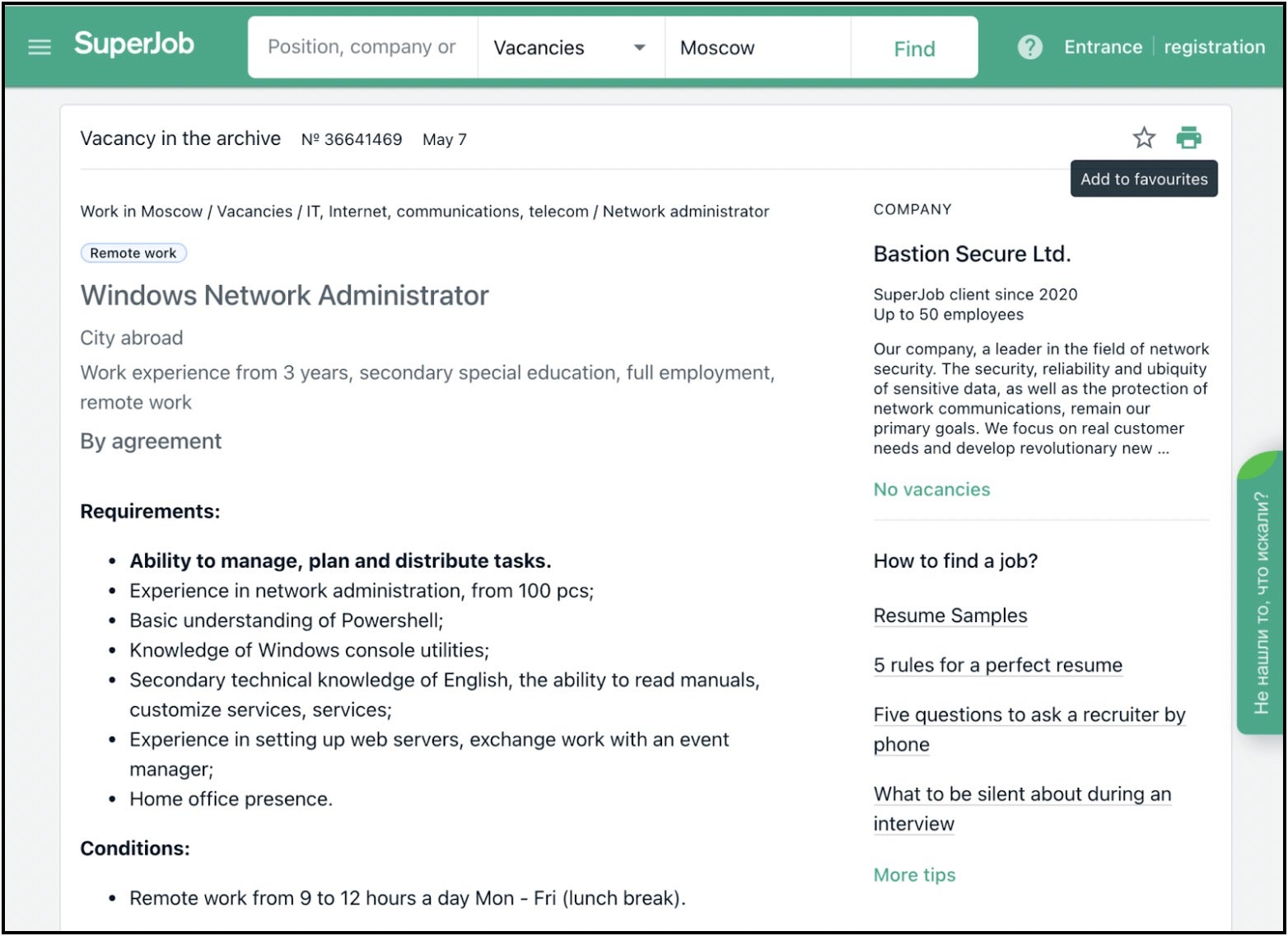
People choosing to be “hackers-for-hire” is bad enough, but things take a turn for the worse when criminals start hiring the good guys and duping them into malicious activities. That appears to be what happened according to a report this week that claims notorious Russian-backed APT FIN7 set up a fake company called “Bastion Secure” and began hiring programmers, reverse engineers, and system administrators.
The new hires were given access to a “client” and tasked with penetration testing activities such as mapping out the network, identifying users and devices and locating backup servers and files. Unbeknownst to the hired pentesters, the “client” was in fact a victim being prepped for a ransomware attack. Software given to the hires to be used in the engagements was identified as a disguised version of the Carbanak backdoor.
Potential motives for FIN7 recruiting legitimate IT specialists? Paying ‘good guys’ a salary is cheaper (and more reliable, presumably) than hiring criminals, and is easier to ensure the ‘talent’ has the requisite skills. As the researchers put it, hiring legitimate professionals helps the threat actors to balance “the need for a technically skilled team against the operators’ desire for maximum profits.”
This isn’t the first time FIN7 has set up a fake cybersecurity company. Previously, they were associated with hiring IT pros through a fake firm, “Combi Security”, in an attempt to involve them in carding campaigns. This time round, the aim was a ransomware attack. It seems it’s not just the good guys that want to hire us, and if they’re not trying to hire us, the bad guys are trying to infect us. Moral of the story for infosec professionals: “Let’s be careful out there”.