The Good
We have another satisfying victory for cyber crimefighters to highlight this week. It feels like these wins are getting more frequent, so let’s continue to tip our hats to these complex efforts from law enforcement. This week’s criminal round-up comes courtesy of “Operation DarkHunTOR”.
This global effort combined agencies from the United States, United Kingdom, Switzerland, Italy, the Netherlands, Bulgaria, France, and Germany among others, and was directed by Europol and JCODE (Joint Criminal Opioid and Darknet Enforcement team).
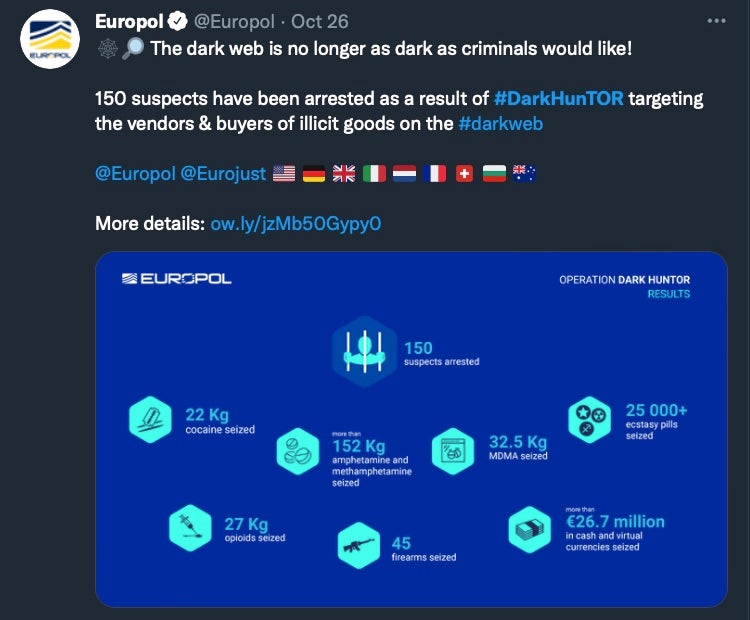
The effort targeted around 150 individuals, all of whom were involved in the sale and trafficking of illegal products, including weapons, drugs, stolen data, malware and other contraband. The individuals apprehended were all considered to be “high-value” targets in the eyes of law enforcement.
Authorities reportedly seized nearly $26 million in combined cash and cryptocurrencies along with various troves of drugs and guns. In addition, the popular Dark Web marketplaces “DeepSea” and “Berlusconi” were shut down and seized as well. Those markets now join the likes of Dream, Aurora, WallStreet and others as part of a long list of defunct (yet once mighty) traders of illicit goods.
According to the official release from the Justice Department:
All in all, a great victory, culminating from a very well-executed effort.
The Bad
Rising to the top of this week’s bunch of bad is an apparent rebrand from Haron ransomware, who this week pushed out a new leaks site that’s clearly linked to the ‘Midas’ ransomware group. Along with a few fresh victims, the ‘new’ site also listed all of the same victims that had previously appeared in the Haron victim blog. There is also strong evidence to suggest some shared infrastructure between the two, along with shared post-infection TTPs.
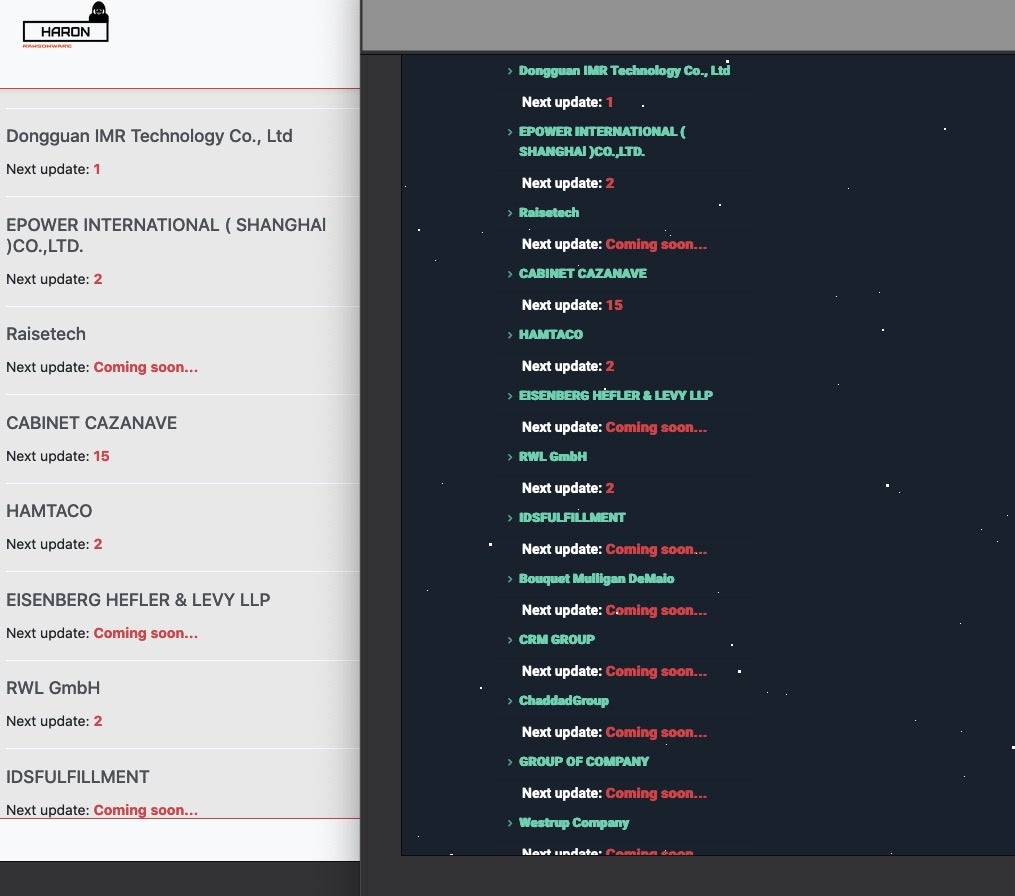
The group’s updated manifesto continues to lay out their ‘ground rules’ for attacks, as well as some ‘rules of engagement’. The Midas/Haron gang claim to be “a group of pentesters who use (their) skills to audit the security of corporate networks”. The act of encrypting files in the target network is, they would have us all believe, merely “confirmation” of the fact that the target has “problems in the network”. It goes without saying that their claim falls a bit short of accuracy. The group claim to have no specific political affiliations or connection to any terrorist or extremist organizations. We are, presumably, to believe they are ‘the good guys’.
Unconvinced by these protestations of innocence? We are, too. This kind of “rebranding” is somewhat en vogue these days as a means (amongst other things) to circumvent government regulations and lower visibility. SentinelLabs continues to monitor this and similar threat actors.
The Ugly
A particularly nasty combo attack, involving typo-squatting, ransomware and malicious NPM packages was observed this past week.
It was discovered that two particular packages were present in a popular NPM library, noblox.js-proxy and noblox.js-proxies. Both were masquerading as a common, legitimate package with a very similar name. As the typo-squatting names indicate, the intended targets were those seeking to customize or augment their Roblox experience.
The malicious packages essentially function as scripts which reach out to a remote server to download and execute additional malicious components. Payloads included the GoldenEye and MBRLocker variants, both of which are commodity-level threats.
Further, both of these ransomware variants are either now or once were open-source, meaning they are trivial to weaponize and distribute. Some readers will remember that GoldenEye was a later-stage evolution of the Petya/Mischa RaaS, while MBRLocker has a variety of free or leaked builder applications.
The silver lining here is that attacks of this nature–evil scripts downloading outdated ransomware–are well-understood and can easily be thwarted with well maintained, modern, endpoint security controls.


