The Good
It’s been a tough week for those in the world of cyber espionage, and while we do recognize that there are spies that work for us as well as those that work against us, this week saw two stories break that will likely bring glad tidings to most.
First up, President Biden continued his administration’s welcome war on cyber bad guys with a ban on four different “spyware” companies, namely Russia’s Positive Technologies, Singapore’s Computer Security Initiative Consultancy and two Israeli companies, Candiru and NSO Group (distributor of the notorious Pegasus spyware). The four were all adjudged by the Biden administration to be trading in hacking tools used to “maliciously target government officials, journalists, businesspeople, activists, academics, and embassy workers” in the service of authoritarian repression that “threatens the rules-based international order”.
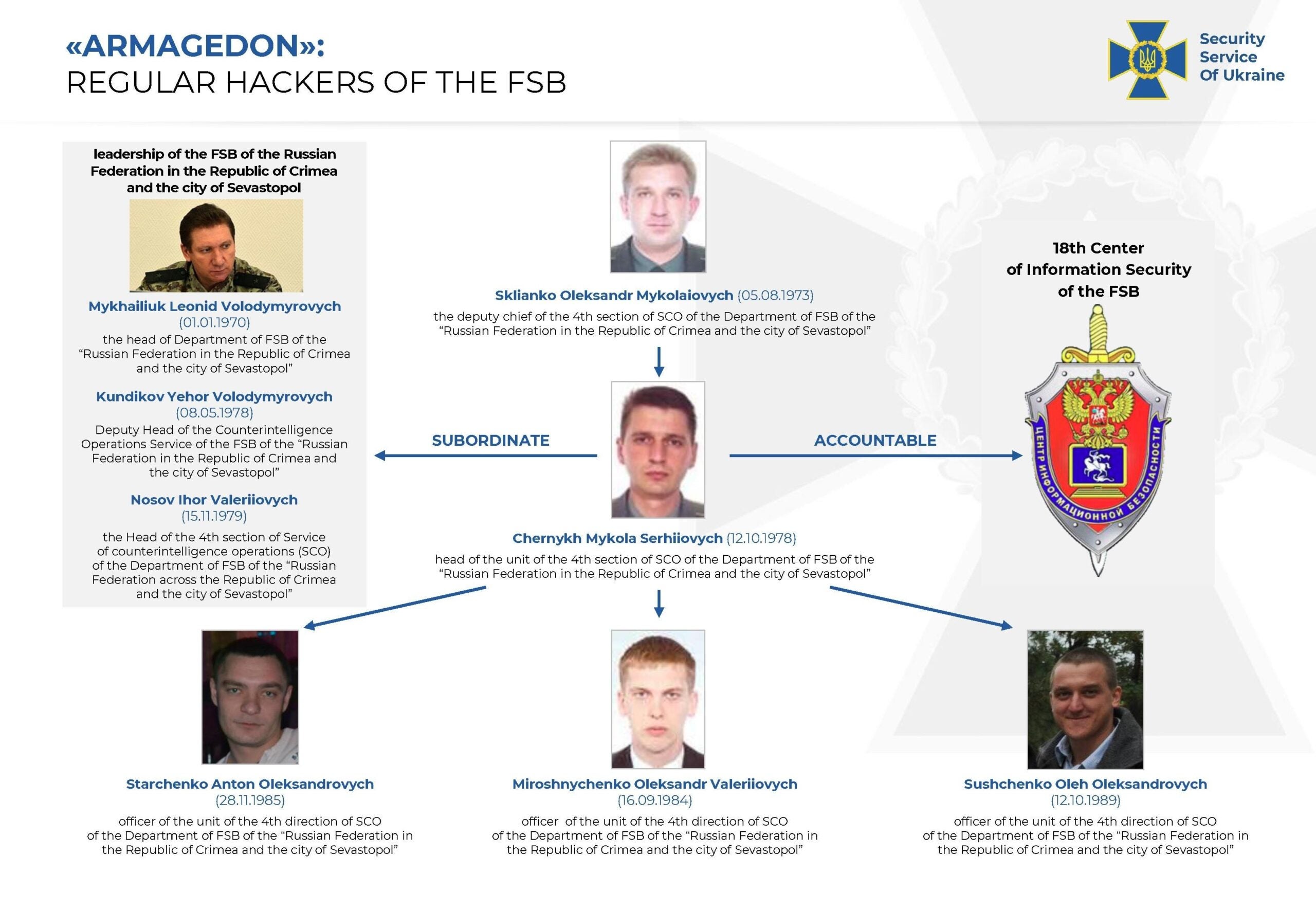
Meanwhile, Ukraine has outed members of an APT operation run by Russia’s FSB unit, more widely known as the Gamaredon group.
The details are fascinating and well worth a read, but the upshot is that Ukraine’s Security Service (SSU) were able to intercept conversations among FSB hackers and obtain data on thousands of Gamaredon C&C servers. Along with publishing a detailed report on the group’s activities they also ‘outed’ five members of the FSB as being members of the cyber espionage gang. While the TTPs used by Gamaredon are described as ‘not particularly sophisticated’, they have nevertheless been remarkably successful and are worthy of study by defenders in enterprise security teams.
The Bad
While we’ve seen welcome pressure put on DarkSide/BlackMatter ransomware operators this week, nobody is claiming victory just yet in the war against ransomware, particularly not the Las Vegas Cancer Center (LVCC). Back in September the LVCC was hit by a ransomware attack, and this week it turns out that PII belonging to current and former patients may also have been stolen.
The Center said on Monday that encrypted data had been accessed by attackers, and this may have included Personally Identifiable Information (PII) such as names and addresses of patients, date of birth, SSNs, medical records and insurance details.
LVCC were unable to confirm exactly which patient records may have been accessed. While the Center believes that the proprietary format used to store the data may have made it unreadable to hackers, unless it used some kind of strong encryption there’s still a possibility that hackers skilled in reverse engineering techniques would be able to retrieve details even from a proprietary file format.
LVCC has reportedly stated that it “does not believe that any data was copied or transferred from its server, and has received no ransom demand”. Even so, due to the sensitivity of the PII involved, all LVCC patients are advised to monitor credit card activity and be on alert for phishing attempts.
The Ugly
And after the patients comes the medical staff. It seems like there’s no end to the vulnerabilities faced by our healthcare infrastructure these days. This week a Medical School was found to have exposed 157GB of data containing around 200,000 files carrying, among other things, the PII of thousands of medical students, staff and course applicants.
Two years ago to the month, we reported on how researchers from vpnMentor uncovered an unsecured AWS bucket hosting tens of thousands of videos uploaded by users of the Veed platform. Alas, cybersecurity history continues to repeat itself as this week the same researchers reported that the LA-based Phlebotomy Training Specialists had done the exact same thing: an unsecured AWS bucket containing students’ ID cards, driving license details, home addresses, phone numbers, DoBs and professional and educational resumés was left publicly accessible for anyone to view.

The researchers estimate that between 27000 and 50000 individuals are impacted by the leaked data, which contained records from September 2020 to the present day. Affected individuals could be at risk of fraud, identity theft, and phishing attacks. Despite attempts to contact the company, vpnMentor says they have still received no response. Anyone who thinks they may be impacted by the data leak is advised to contact Phlebotomy Training Specialists directly.